IoT Product Security Knowledge Hub


7 Recommendations for IoT Manufacturers for Product Security

Learn how proactive measures can help prevent breaches and enhance the safety of your IoT systems.

CVE-2024-35467 - Stack-based buffer overflow vulnerability in the WPS method on ASUS's RT-AC87U devices

A buffer overflow vulnerability exists when some versions of the RT-AC87U devices improperly handle user-provided input.

CVE-2024-39149 - Post-auth blind OS command injection vulnerability in NETGEAR's X6 R8000 devices

This vulnerability allows remote attackers to execute arbitrary code on affected devices.

Webinar on-demand: Finding Vulnerabilities in Embedded Products - 3 Case Studies

Watch our webinar-on-demand, for free. Learn more about the vulnerability detection and remediation process via case studies.

BugProve is now available on AWS Marketplace

We just made it easier to buy BugProve. The best part? There are no extra charges for using the marketplace.

Webinar on-demand: The Cyber Resilience Act Beyond Buzzwords

Watch this webinar about the European Union's Cyber Resilience Act.

Embedded World 2024 - What We Learned

Recap of the event by our team members who were present. Short summary of the athmosphere, biggest takeaways, some surprises.

Overcoming Limitations of SAST and Other Traditional Software Security Testing Tools

"We have a SAST tool, we are fine." Sounds familiar? What is the problem with this approach?

CVE-2024-25464 - Post-auth blind OS command injection vulnerability in Asus’s Download Master application

Vulnerability disclosure about Asus's router devices. An attacker could leverage this vulnerability to execute commands in the context of the web server, running as admin.

Announcement: BugProve is available on-premise!

You can now request a self-hosted version of the platform if the cloud deployment was a blocker so far.

CVE-2023-5372 - Post-auth blind Python code injection vulnerabilities in Zyxel’s NAS326 and NAS542 devices

Part 3 of vulnerabilities detected in Zyxel's personal cloud storage devices.

CVE-2023-4473 & CVE-2023-4474 - Authentication bypass and multiple blind OS command injection vulnerabilities in Zyxel’s NAS326 devices

Part 2 of our vulnerability disclosure of Zyxel's personal cloud storage devices, including an authentication bypass vulnerability.

CVE-2023-37927 & CVE-2023-37928 - Multiple post-auth blind OS command and Python code injection vulnerabilities in Zyxel’s NAS326 devices

Vulnerability disclosure about Zyxel’s personal cloud storage device. PRIS indicates a command injection vulnerability.

IoT in the Wild West: A Personal Call for Consumer Vigilance and Responsible Development

Attila shares his thoughts about the state of IoT security to contribute to the Cybersecurity Awareness Month movement.

IoT Bug Hunting - Part 2 - Walkthrough of discovering command injections in firmware binaries

Taking bug hunting to the next level. Here are the steps that can lead you to another variation of an OS command injection vulnerability in multiple Zavio IP camera models.

CVE-2023-3959, CVE-2023-4249 - Multiple critical vulnerabilities in Zavio IP cameras

BugProve uncovers seven pre-authentication remote code execution flaws and 26 post-authentication code execution vectors in Zavio IP cameras.
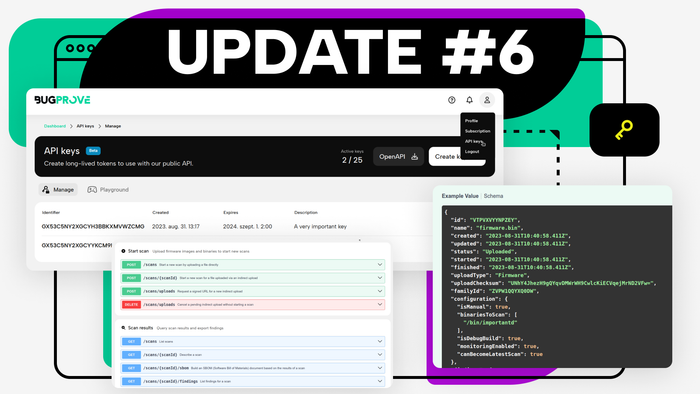
Product Update #6

Improved public API, a new developer portal, larger file uploads and more. For those who prefer integrated systems.
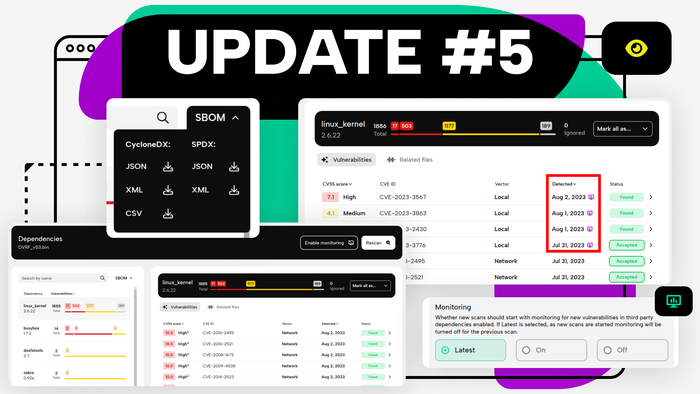
Product Update #5

Vulnerability monitoring, SBOM export, crisp new report pages and more. Great features for manufacturers.

An Overview of IoT Regulations – Compliance Checklist for the USA

If you want to learn more about upcoming IoT regulations in the US, including the Cyber Trust Mark, this is the article for you. Here's a guidance with a clear checklist included.

Binary Analysis Fundamentals

Learn the basics of binary analysis, including its use cases, limitations, the differences between static and dynamic approaches and more.

An Overview of IoT Regulations - Checklist for UK PSTI, EU RED and CRA

If you don't know where to get started about all the upcoming IoT regulations in Europe, this is the article for you. We offer you guidance with a clear checklist included.
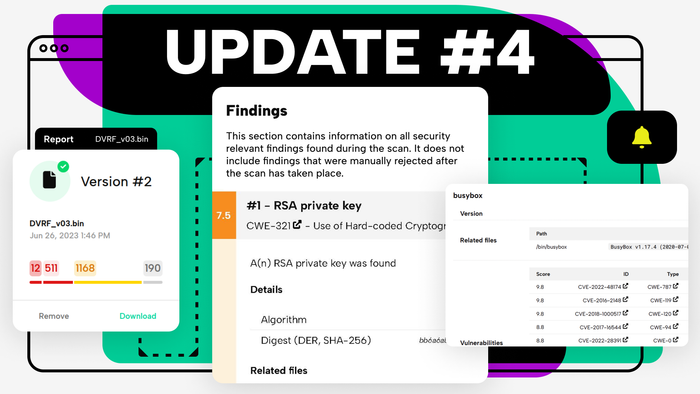
Product Update #4

Security tools should generate long PDF reports - so now we do. Hopefully, making your lives a bit easier.

Why is IoT security so difficult?

We check from a pentester’s perspective why it is so tough to have secure IoT products on the market. Let’s see the 5 main reasons.

Firmware vulnerabilities you don’t want in your product

Delve into the specific firmware vulnerabilities that pose the greatest threat: authentication bypass, buffer overflows, and injection flaws.

CVE-2023-31070 Broadcom BCM47xx SDK EMF slab-out-of-bounds write - the uncomfortable reality of the IoT Linux kernel space

Exploring the Impact of CVE-2023-31070: A Deep Dive into Broadcom BCM47xx SDK, found by Attila Szasz with BugProve's engine.

IoT Bug Bounty Hunting using BugProve - Part 1

A short guide on how to use BugProve's proprietary PRIS engine to scan and evaluate firmware for unknown security vulnerabilities - so you can start your bug bounty journey now!

Product Update #3

Announcing our first AI-powered feature, helping you understand and fix issues faster. Introducing the "Explain" button.
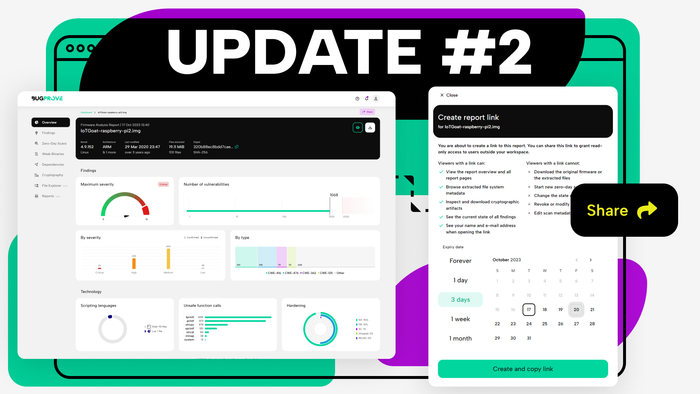
Product Update #2

A smaller one this time, focused on one much requested feature: shareable reports. Let's dive in!
Your Resource Directory for IoT Security

Check out our collection of books, podcasts, youtube channels, and other educational materials on IoT security and pentesting.
Product Update #1

This is the first major update to our platform, and we are excited to give you a brief overview of the changes.

7 Questions and Answers about Firmware and Firmware Security

Discover the ins and outs of firmware security with this all-encompassing guide, including vulnerabilities, encryption, and best practices.

Enhancing Device Security beyond Firmware Encryption

Learn about the limitations of firmware encryption and the risks of firmware hacking techniques that can bypass this security measure

EU Cyber Resilience Act (CRA) - All you need to know in a nutshell

The issue of low cybersecurity standards that plagued the IoT sector for years is going to be solved. Well, not at once, but we are making steps in the right direction.

Launching our Free Plan!

To show you the full potential of our 0-day vulnerability discovery and firmware analysis features, so we made sure all the results are there in our Free Plan.

CVE-2022-24942 Heap-based buffer overflow in Silicon Labs Gecko SDK

An overview of the vulnerabilities found by BugProve in the SDK of Silicon Labs. An attacker can send an HTTP request to trigger this vulnerability.