Back to the articles
Why is IoT security so difficult?

Table of contents
- You need to get your hands dirty with hardware hacking
- Low-level programming is a must for binary analysis
- Networking basics are useful to understand remote attack surface
- Web application security experience is a good foundation
- It is hard to do them all well to cover all angles of IoT security
- Conclusion
The reasons why securing the Internet of Things is so difficult are many-fold, but to name one from the perspective of a penetration tester: it requires a diverse set of knowledge and experience with both software and hardware security. In this article, we collected some of the main challenges of IoT security.
You need to get your hands dirty with hardware hacking
The hardware is among the most common attack vectors in an IoT device because devices are widely available for anyone and vendors often use common hardware interfaces in microcontroller development for debugging purposes. Although firmware images are typically publicly distributed by manufacturers, physical access to the device also allows attackers to tear them apart and look for hardware vulnerabilities. However, understanding electronics and how the elements on a circuit board interact is essential for hardware hacking.
Furthermore, you will need specialized hardware tools to target IoT devices at the physical level. For instance, you may need to use a multimeter to identify the UART pins on a device’s printed circuit board, then connect a USB-to-serial adapter and open a serial debug console to gain a root shell.
Doing so will require familiarity with the inner workings of the communication protocols used by debug interfaces like UART, JTAG, SPI, and I2C. You might also have to perform some (de)soldering to communicate with the target device. Vendors who follow best practices may disable debug interfaces to hinder others tampering with the system, however, attackers may still find their way into the device. Extracting the firmware directly from the microcontroller is the most complicated method and requires a chip programmer. You can read more about the firmware readout process and hardware hacking techniques in our earlier post about the effectiveness of firmware encryption.
Low-level programming is a must for binary analysis
Some IoT devices are small connected devices like sensors or actuators. They need firmware to collect metrics, turn something on or off, or perform similar basic operations. They have low computing power and limited memory capacity, so the optimal programming language for this kind of IoT device is a low-level language such as C/C++. Writing in C/C++ allows you to create compact and optimized programs that can run with limited resources. In addition, all well-known microcontrollers are compatible with C/C++ languages.
However, reading C/C++ source code, especially reverse engineering assembly code, requires expertise and a solid understanding of best practices because they are not the simplest programming languages. They are highly expressive and flexible, but they’re also very error-prone. Also, the lack of memory safety in C/C++ often results in memory corruption and potentially exploitable security vulnerabilities.
Networking basics are useful to understand remote attack surface
The network layer, which includes all components communicating via standard communication paths, is the largest attack vector. For complex IoT systems, such as smart homes or healthcare environments, even a network reconnaissance involving host discovery, service version detection, operating system identification, and topology mapping could be complicated.
Nonetheless, to perform a man-in-the-middle attack during the OTA update of a single device, you would need to intercept the network traffic using a packet sniffer with a poisoning technique and a proxy that can retrieve the firmware binary.
To better understand the security implications of IoT connectivity, it is worth recalling the infamous Jeep hack, when Charlie Miller and Chris Valasek took complete control of a car remotely via the cellular network, pivoting through another component to get access to other aspects of the car after modifying the component’s firmware.
Web application security experience is a good foundation
Being familiar with the usual suspects is important for full exploit chains. Vendors nowadays want to create cloud-based mobile applications for every use case. Many security issues of mobile applications using cloud computing overlap with web applications because the clients are usually using APIs to interact with cloud components that are simple web services. Web applications used in IoT systems are often externally accessible and riddled with vulnerabilities. Web application security is a vast topic with its own history and has improved slowly but steadily over the years.
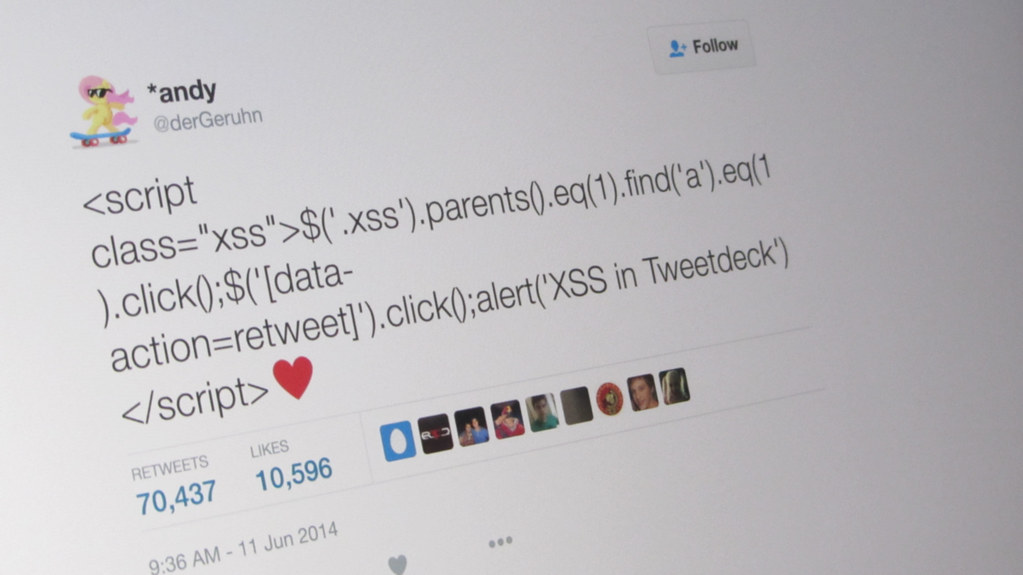
Despite being decades old, well-known web application vulnerabilities like XSS not just remain common , but their potential impact also increased as new technologies like Electron might allow RCE via XSS vulnerabilities, and now they also threaten the IoT ecosystem.
It is hard to do them all well to cover all angles of IoT security
You may notice that hardware vendors and software developers face the same challenges from different perspectives. An IoT ecosystem is a network of interconnected devices, sensors, and software applications working together to collect, analyze, and share data. Some of these IoT systems contain connected devices, including their software and hardware components, while other examples of IoT systems are web or mobile applications and cloud components. Though this large attack surface makes the developer’s work harder to protect the IoT ecosystem, at the same time, it also requires a more seasoned attacker to hack into it. Finding the “right” way to do security depends on the application, making it more difficult to develop standards and best practices.
IoT systems are still relatively new, and the ecosystem is naturally complex due to the various ways to connect devices. There are good resources for building secure computer networks or web and mobile applications, but guidance for securing IoT systems is still lacking. Furthermore, we can be sure that recently passed and planned cybersecurity legislation and standards will also impact the design of IoT devices. You can check out a short recap on the Cyber Resilience Act here.

Conclusion
Security professionals involved with penetration testing IoT devices need a specific and rare skill set, making them hard to find. This talent shortage adds to the already difficult challenge of securing these products. In my opinion, the biggest obstacle to cyber security nowadays is the skills shortage. The rapidly changing threat landscape has increased the need for cybersecurity more than ever. However, the potential workforce is not growing as quickly as the demand. Hence, the talent gap will remain an ongoing challenge.
BugProve’s tool aims to relieve the burden of security analysts by automating the firmware analysis process. This tool is further supplemented with accurate zero-day discovery performed by the PRIS™ engine, capable of detecting buffer overflows, command injection sites, and a variety of other issues that have the potential to become exploitable vulnerabilities. Give it a try via our Free Plan or book a call if you want a personalised product showcase.