Automotive Product Security
Vulnerability Discovery and Management for OEMs and suppliers
Level up your CSMS and take control of your supply chain dependencies. Extract SBOMs automatically, and monitor vulnerabilities. Detect zero-day flaws with our engine, mitigate critical risks, and prevent breaches.
Let’s talkAutomotive Cybersecurity Landscape
Automotive Cybersecurity Landscape
There are millions of lines of code in cars today, hundreds of components connecting with each other and with networks, as well as with other vehicles. Vulnerabilities are often inherited along the supply chain, making them nearly impossible to fix. Standards like ISO 21434 were designed to compel all participants to take cybersecurity seriously from design until end-of-life.
What do We offer?
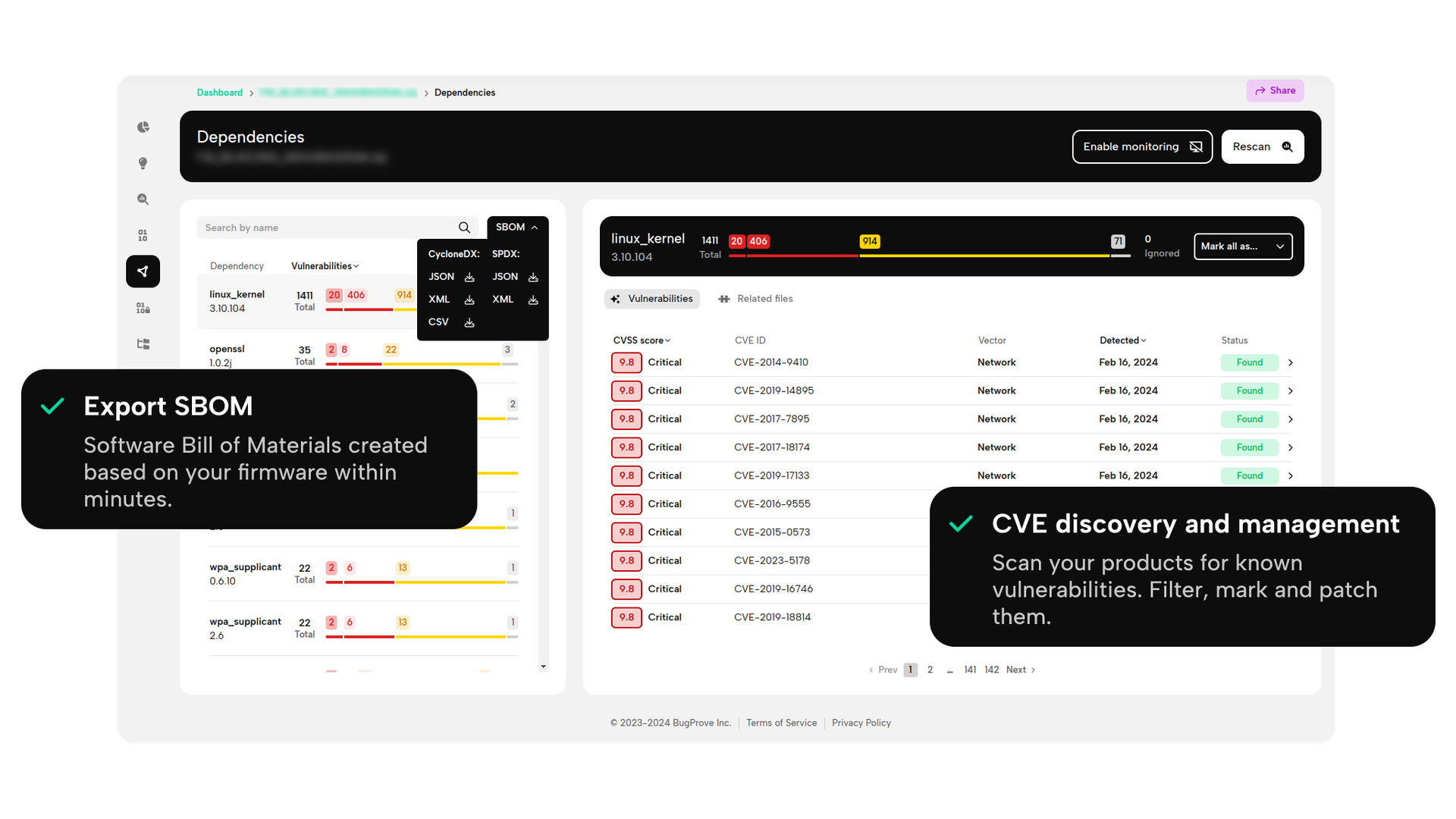
SBOM - Transparency like never before
Identify your third-party components and get a complete overview of your CSMS and supply chain security exposure.
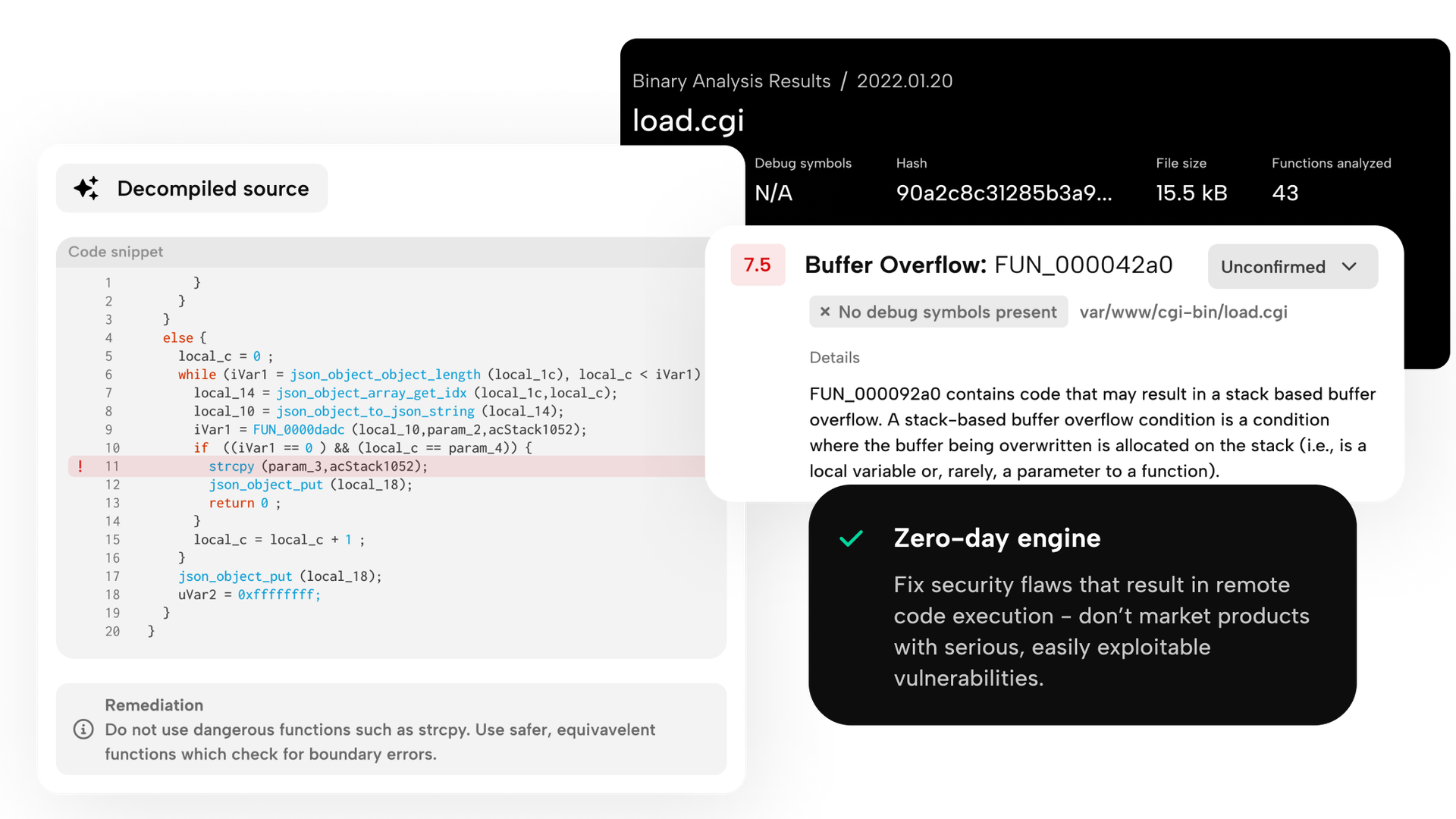
Detect zero-days during development
Use our proprietary PRIS engine to detect secure coding mistakes that could lead to seriously compromised vehicles.
Simplify compliance audits
Develop secure-by-design products using automated firmware scans and demonstrate documented processes in compliance with ISO/SAE 21434.
Set your priorities straight
Focus on the riskiest components by breaking down the attack surface based on code quality heuristics, network exposure and security metrics beyond CVSS.
Vulnerability management
Detect early, and use AI-driven recommendations for patching - all in one place.
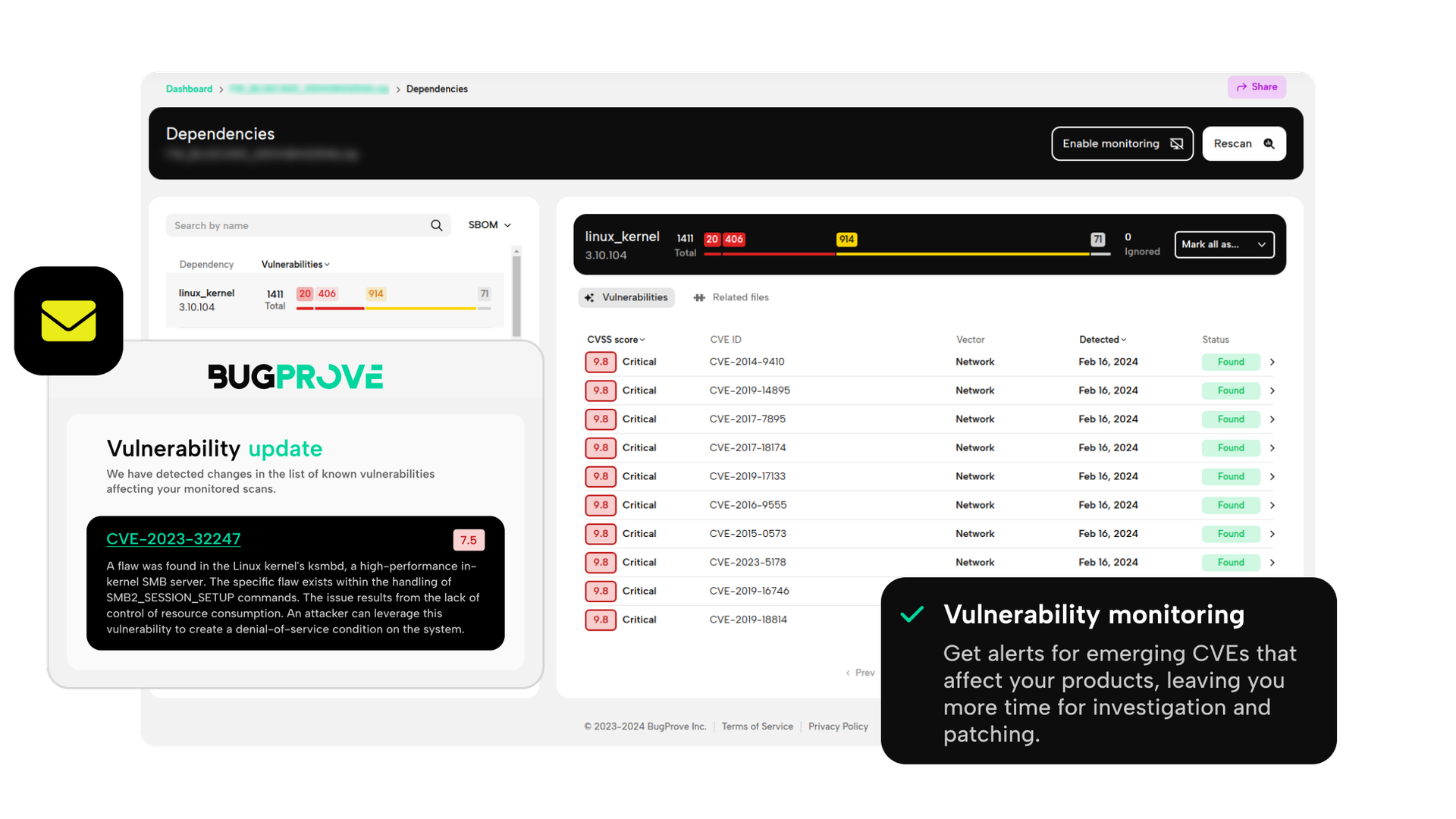
Efficient post-production security
Monitor how emerging vulnerabilities affect your products and get immediate alerts.
Check out our product showcase
A security platform you can trust
How to get started?
Schedule a call
No discovery call, we jump right into the platform together
Receive custom access
Benefit from tailored quota and onboarding support
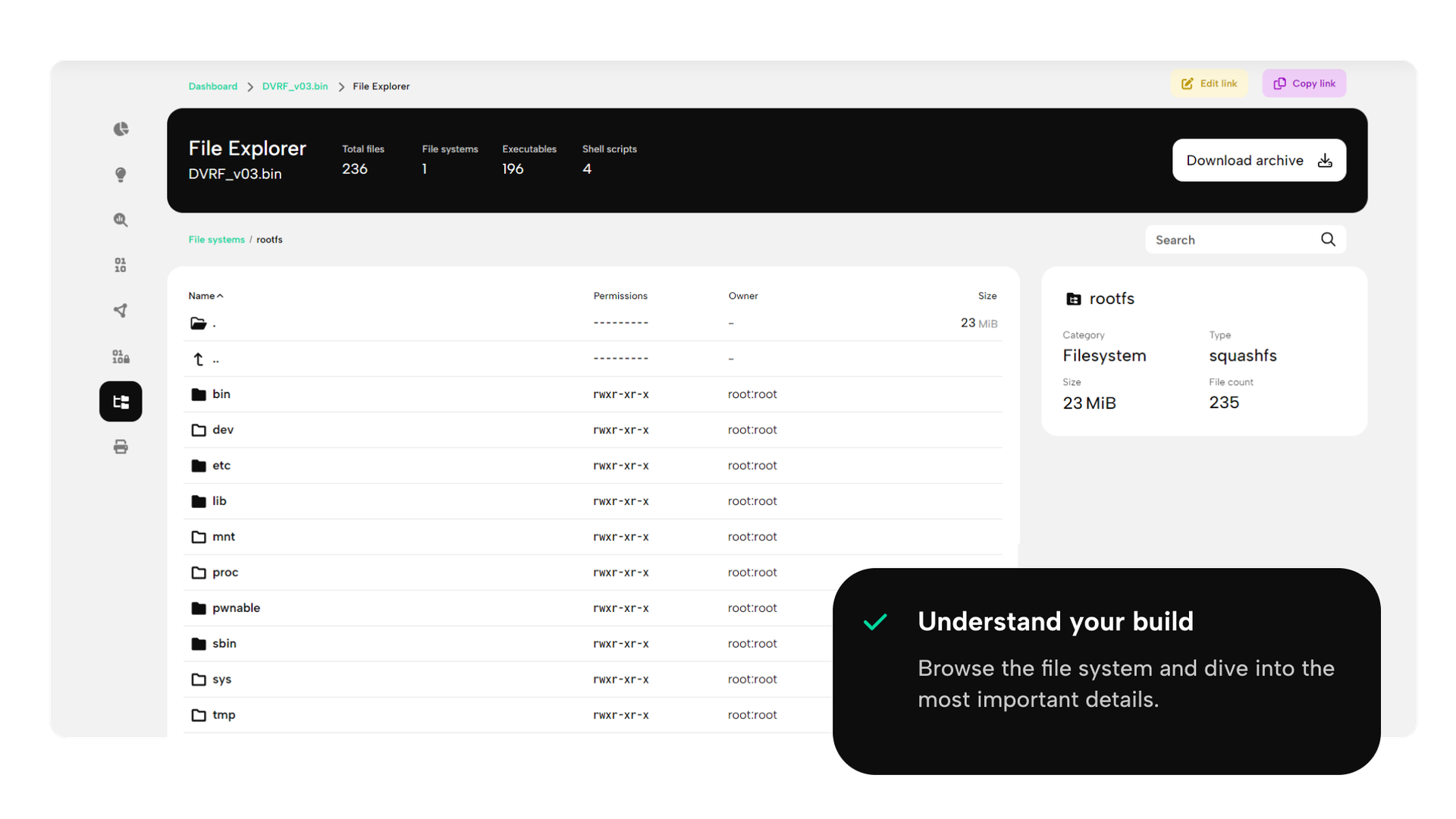
Upload your firmware
Start analyzing immediately
Report, remediate and monitor
PDF-exports and recommendations with vulnerability monitoring
Cloud or Self-hosted deployment
We recognize the benefits of both - the choice is yours.
Does it work?
We use it ourselves to detect new vulnerabilities.

CVE-2023-3959, CVE-2023-4249 - Multiple critical vulnerabilities in Zavio IP cameras

BugProve uncovers seven pre-authentication remote code execution flaws and 26 post-authentication code execution vectors in Zavio IP cameras.

CVE-2023-31070 Broadcom BCM47xx SDK EMF slab-out-of-bounds write - the uncomfortable reality of the IoT Linux kernel space

Exploring the Impact of CVE-2023-31070: A Deep Dive into Broadcom BCM47xx SDK, found by Attila Szasz with BugProve's engine.

CVE-2022-24942 Heap-based buffer overflow in Silicon Labs Gecko SDK

An overview of the vulnerabilities found by BugProve in the SDK of Silicon Labs. An attacker can send an HTTP request to trigger this vulnerability.