Back to the articles
IoT Bug Bounty Hunting using BugProve - Part 1


This is Part 1 of a series of posts we dedicate to bug hunting. Here, we will discuss the basics of using automated tools to get started. In Part 2, we deep dive into discovering command injections in firmware binaries.
Using BugProve's Free Plan
In addition to collecting much-appreciated feedback from our valued security community, we offer a Free Plan to make it easier to get started in IoT security for all and help bug bounty hunters to broaden their scope in searching for security vulnerabilities. Currently, the Free Plan provides full functionality, including PRIS, our proprietary code analysis engine, which can help you discover zero-day vulnerabilities. This is an introduction to the bug bounty hunting process to help you get started with BugProve in an organized and well-structured way.
Choose target firmware
The IoT ecosystem is more heterogeneous, complex, and less mature than other members of the digital ecosystem. The significant number of IoT devices represents a huge attack surface for threat actors. Recent surveys show that NAS, DVR, IP cameras, baby monitors, and audio-video devices are the 5 most targeted device types. Although NAS and DVR devices face more attacks, IP cameras are infamous for their poor security: they are often exposed to the Internet and shipped with either publicly known or weak hard-coded administrator credentials. IP cameras are also excellent targets due to their advanced features and functionality. Some vendors like NETGEAR or Xiaomi have bug bounty programs with hardware and device firmware in scope. Whatever type of device you choose to target, ensure that fully built firmware is available and that the target platform is on the list of Supported Platforms.
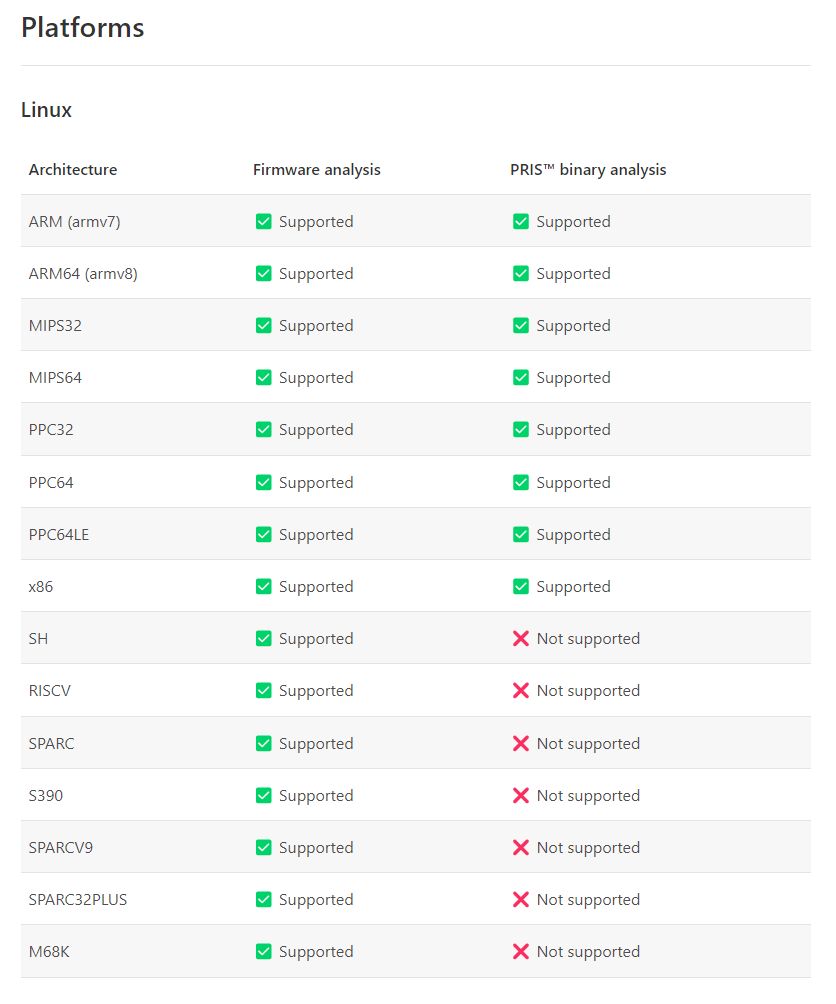
Scan target firmware
Once you have the firmware you wish to analyze, it is time to look for vulnerabilities. Just create a free BugProve account (no credit card needed) and upload the firmware to launch a new scan. The initial firmware analysis will collect information about common security issues under the Known Vulnerabilities page. However, as a bug hunter, you will be most likely interested in yet unknown security vulnerabilities. The Weak Binaries page is a good starting point for further analyzing a firmware image using PRIS. By default, the first five binaries with the highest heuristic score will be selected for further analysis with PRIS. Yet, depending on the target or your research methodology, you may want to first review and then manually launch PRIS scans on binaries selected by you. To direct your attention, you can try to sort binaries based on their score or the number of individual unsafe function calls. I recommend focusing on binaries calling networking-related functions and compiled with the fewest security hardening flags.
Evaluate scan results
When the subscans are ready, you can dive deeper into vulnerability research. The subscan results are unconfirmed findings, which you should thoroughly review and accept or reject as valid findings.
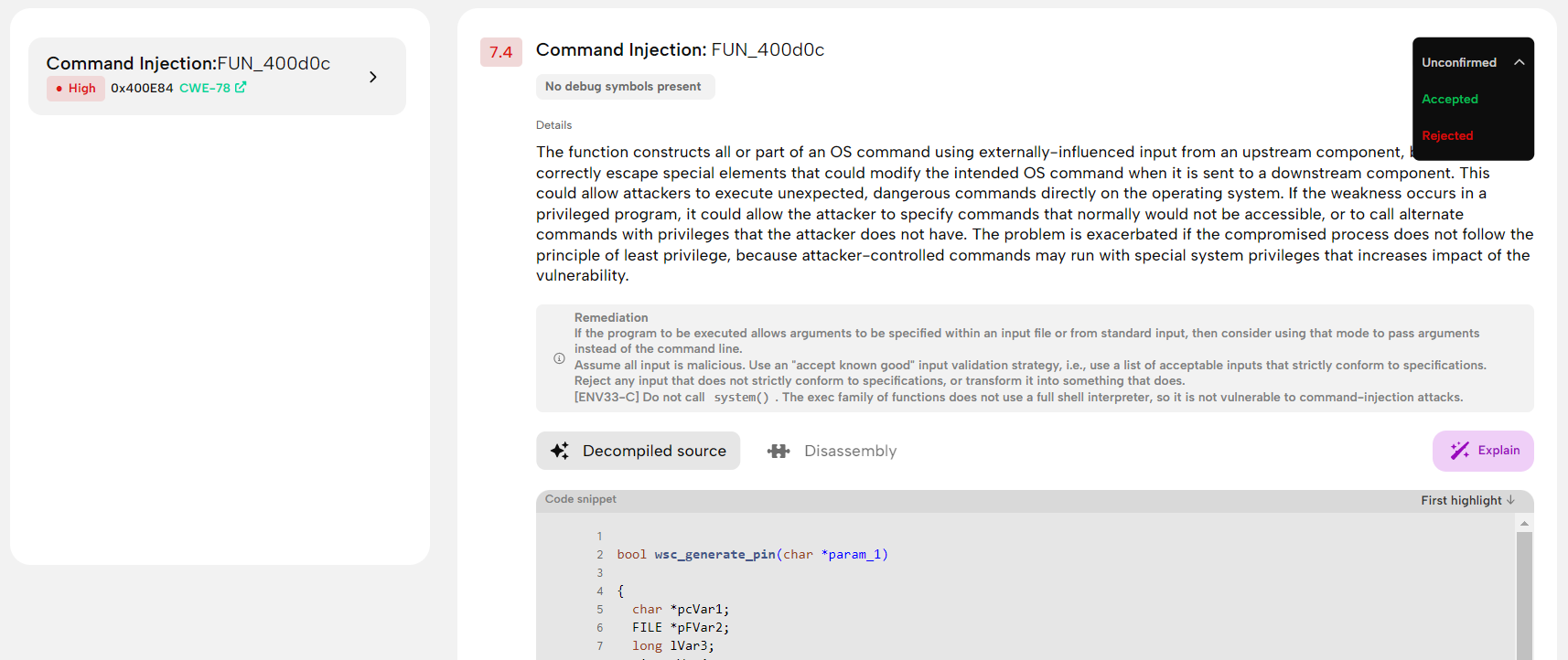
Our tool aids you in this process with a vulnerability class description coupled with syntax-highlighted decompiled C code and ASM listing, displaying the vulnerable function(s) and highlighting the problematic line, if possible. When you run into something interesting, you may use tools like Ghidra, IDA, or Binary Ninja to reverse engineer and further analyze the suspected binary. If the finding still looks promising, you may run the affected binary with QEMU user-mode emulation or GDB debugger for advanced dynamic analysis to verify the vulnerability and create a proof-of-concept to demonstrate exploitability and impact. You can find some excellent materials to help you with your research in Your Resource Directory for IoT Security.
Report vulnerabilities
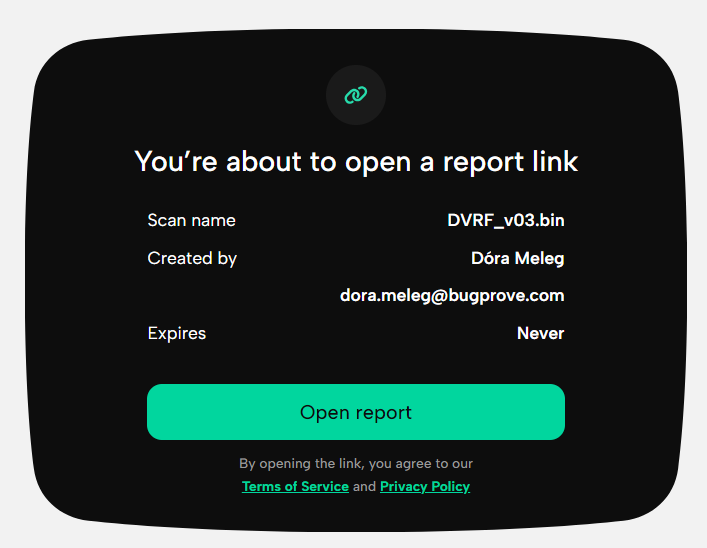
Congratulations on your findings! If participating in a bug bounty program, ensure you adhere to the program rules, especially the reporting requirements. In addition to the risk classification of the vulnerability, the report quality will usually determine the amount of bounty reward. We recommend sharing the details with the affected vendor on a secure channel and following coordinated vulnerability disclosure (CVD) practices. In your report, you should provide as many details as possible, especially what the vendor needs to know to reproduce the issue and validate your finding. For an example, see our report of CVE-2022-24942, a heap-based buffer overflow vulnerability in Silicon Labs Gecko SDK found using the PRIS engine. Furthermore, since our second product update, you can also easily share the live firmware scan report with vendors via a simple link leading directly to the PRIS results.
This is what you will see when you click such a link. Click to check out an example report.
Ready to go deeper? Check out part 2 where we offer a step-by-step guide to finding command injections.
Happy bug bounty hunting using BugProve!