IoT Pentest Automation for Increased Efficiency
Developed by security engineers
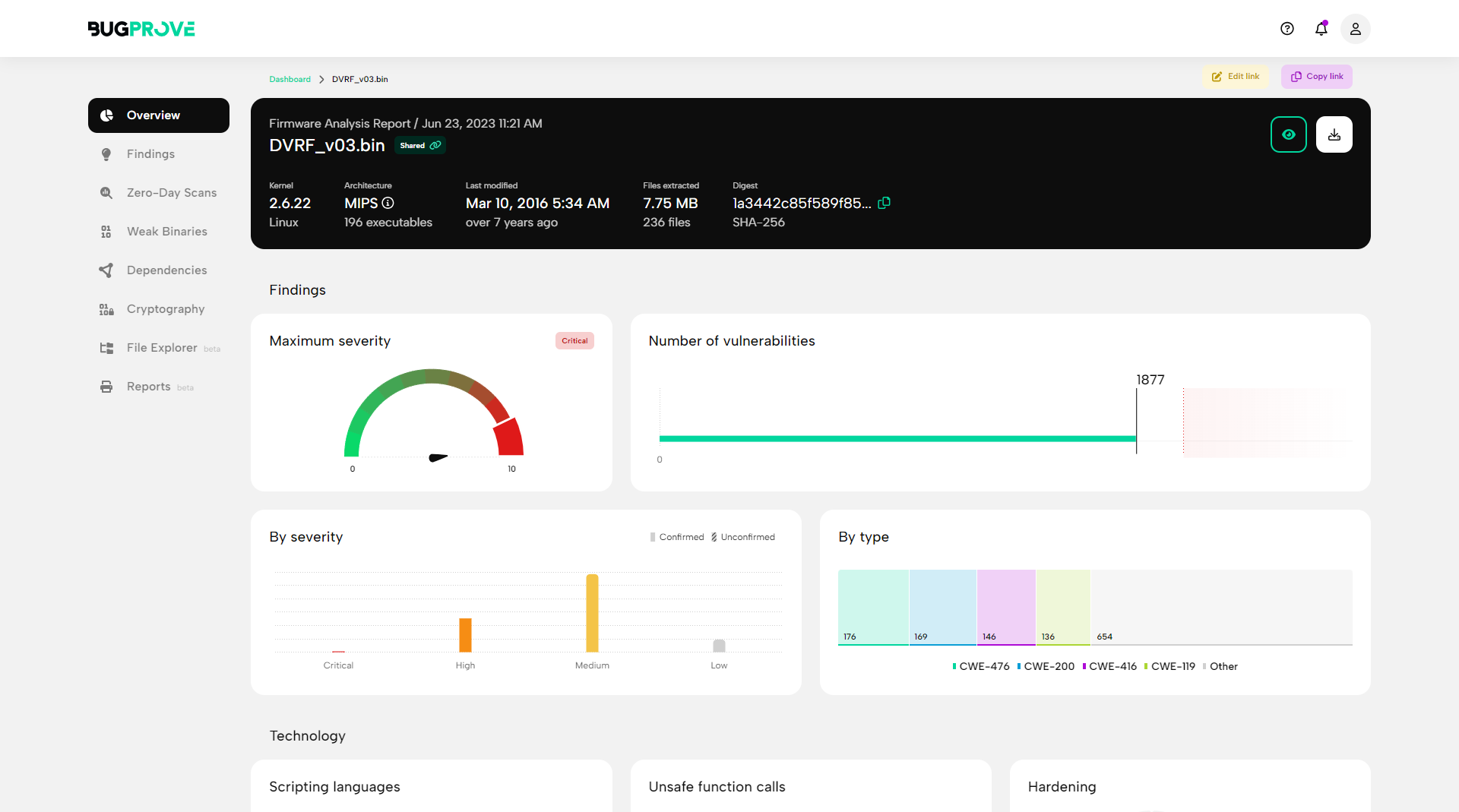
Advanced binary analysis with zero-day detection, interactive reports, and AI-assisted recommendations for you – better and faster service to your clients.
Start for freeAccelerate your process with automation
We automate:
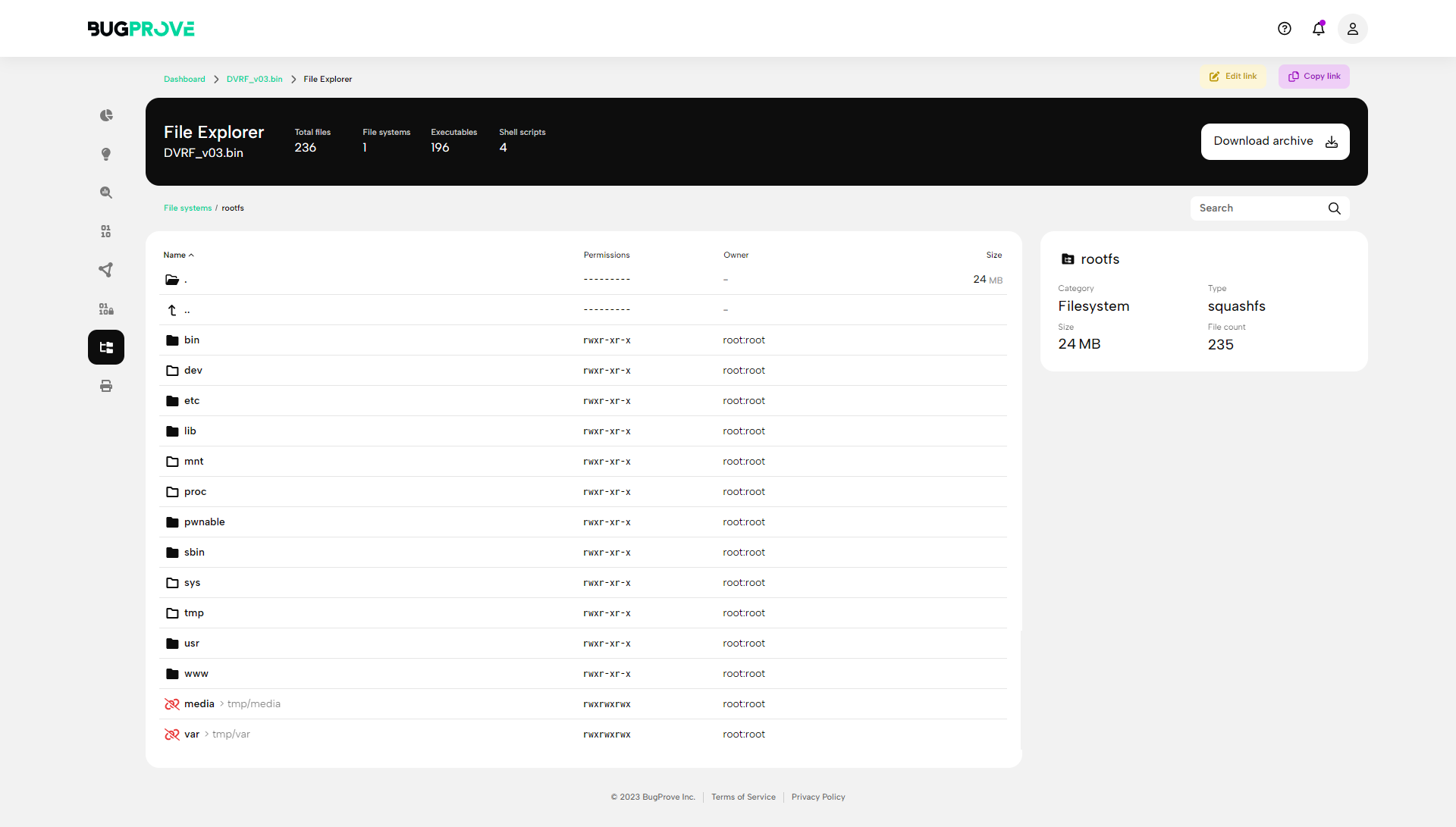
Firmware extraction
Component identification
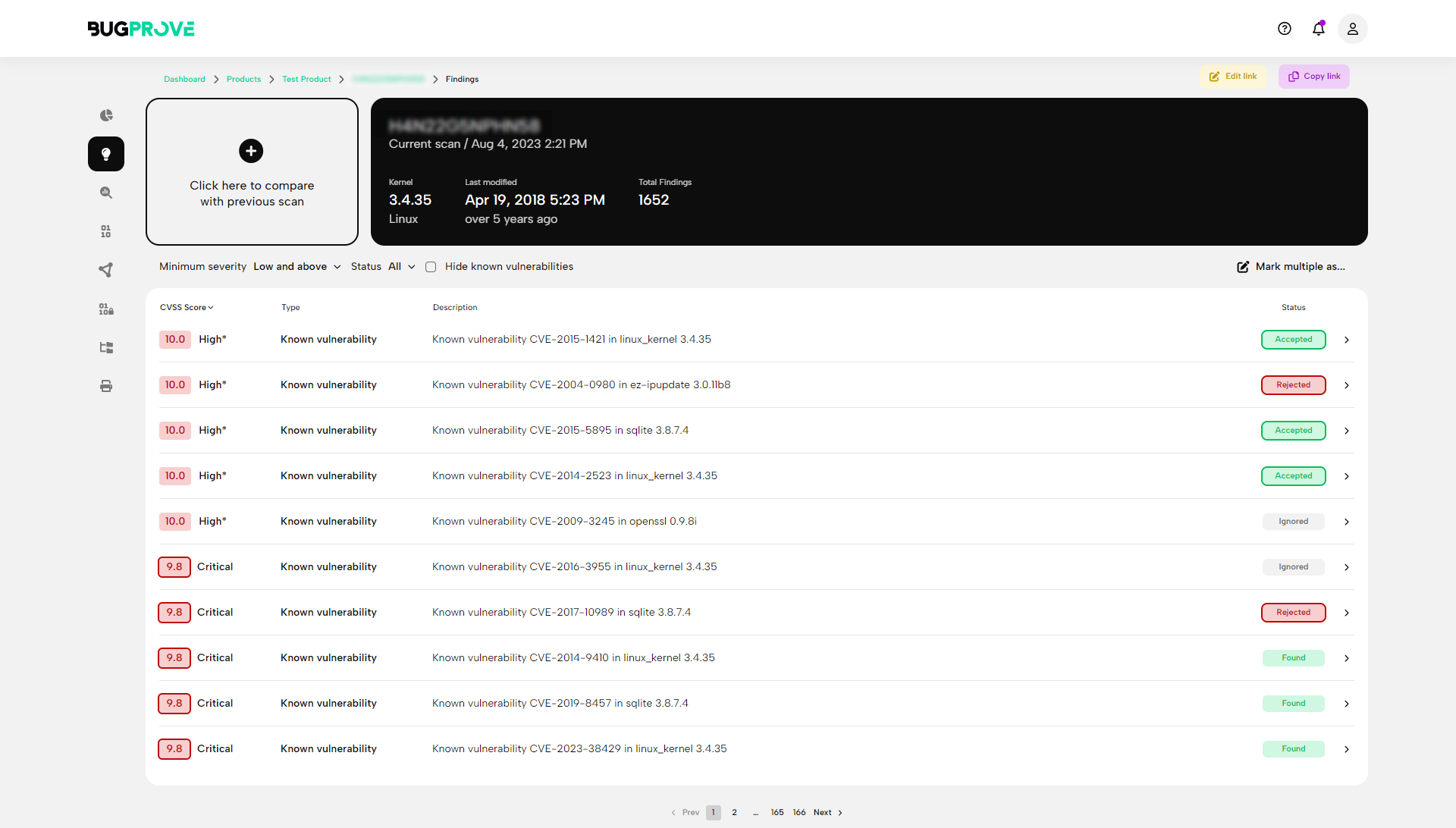
Known vulnerability lookup
Cryptographic key and parameter collection
Hardening checks
Binary and script analysis
Reconnaissance
Report generation
So you can focus on:
Binary reverse engineering
Exploitation
Protocol analysis
Hardware hacking
Boot trust chain verification
Fuzzing
Level up your IoT cybersecurity services
Don’t waste your sr. researchers’ efforts on repetitive tasks
Impress your clients with the depth of your findings
Focus on your core expertise and let us handle the tooling
Get to know our Platform in 5 minutes
Let us give you a tour of our product in this video.
If you have any questions, or you just prefer a personalized demo, book a call here!
Let’s talkWhat's under the hood?
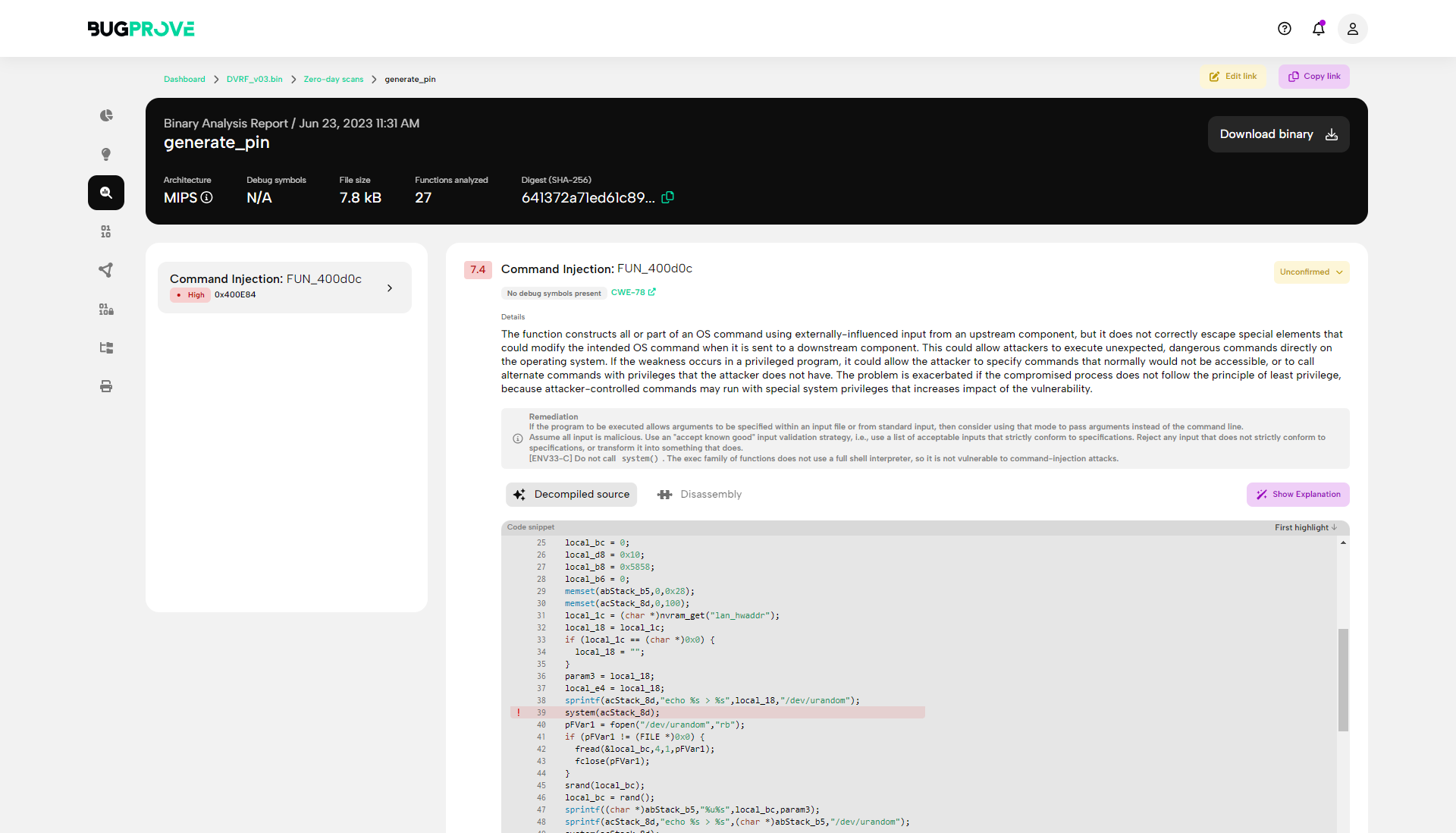
Powerful vulnerability discovery for C/C++ binaries
Find zero-day vulnerabilities in minutes by employing advanced dynamic analysis techniques on binaries.
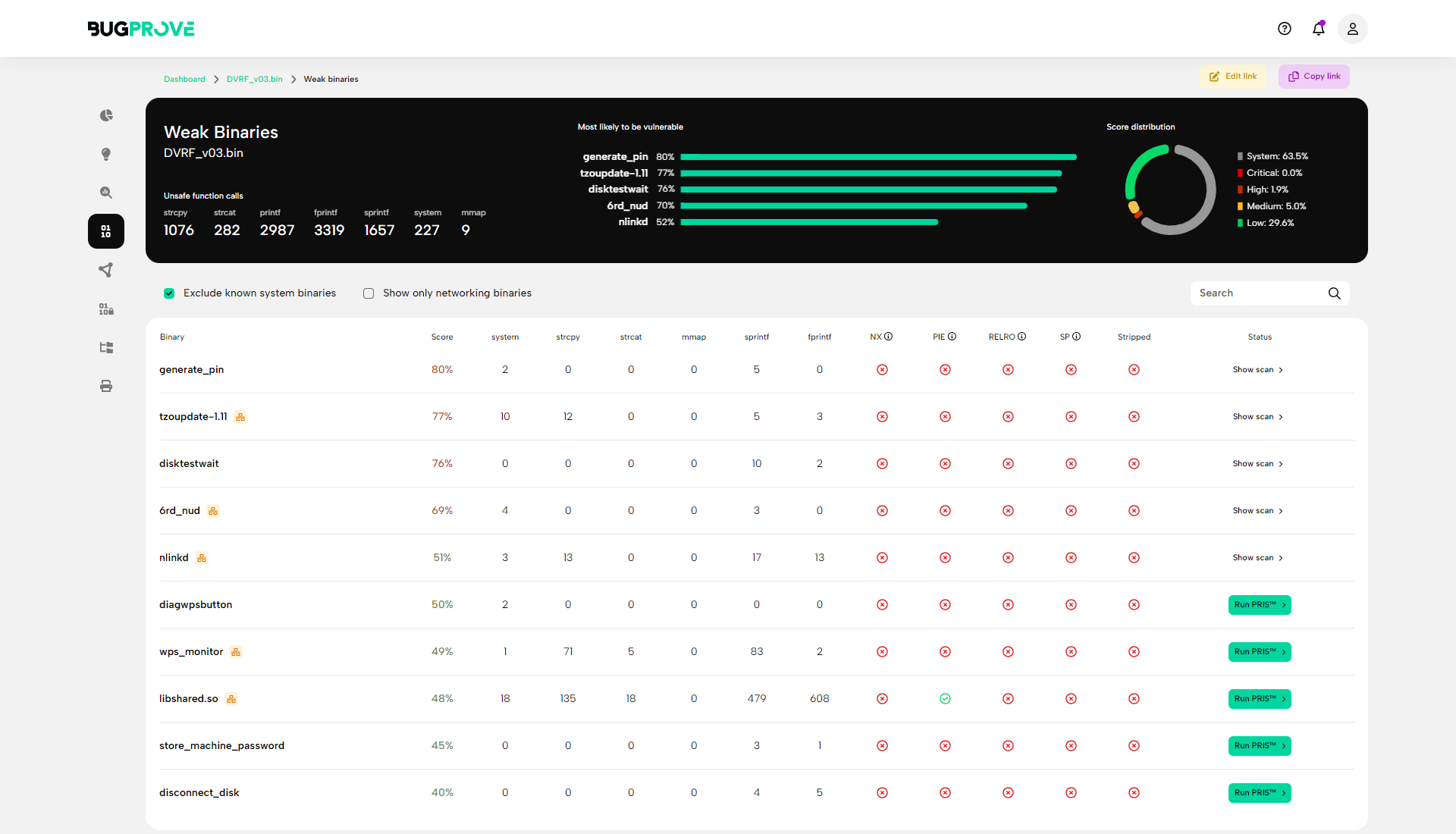
Binary intelligence
Gather in-depth information on binaries and detect common hardening techniques like stack canaries, fortification, stripping, and so on.
Cryptographic analysis
Assess the strength of cryptographic algorithms, and discover relationships between private keys, public keys and certificates.
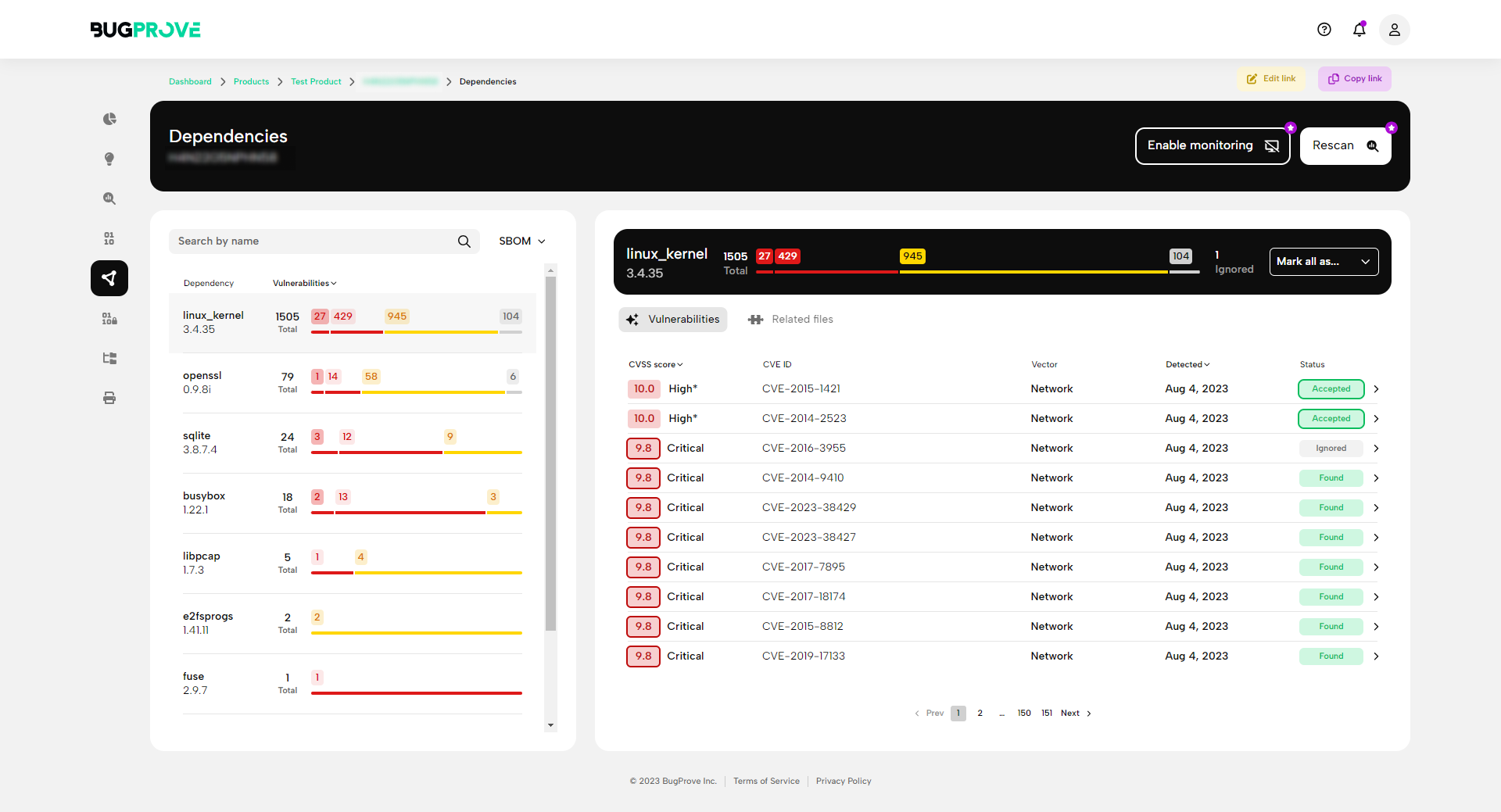
Composition analysis
Identify third-party dependencies and scan for known vulnerabilities, even without an explicit SBOM.
Live reports and PDF exports
Access live report sharing and PDF exports to speed up your reporting to clients.
AI-driven assistance
Receive remediation recommendations to both known and zero-day vulnerabilities to deliver practical advice to your clients.
Speed and accuracy: without the legacy feel
Dive into scan results within minutes and enjoy a clean and intuitive design.
A tool you will love
In BugProve, it was a pleasure to use the main functions, with an intuitive interface. Displaying CVE numbers was very useful. And by the way, everything looks damn good!
BugProve is intuitive and automates many of the repetitive tasks in firmware security testing. Uploaded images of the most common formats are unpacked, the file system is extracted and exposed to further analysis. The team strives for innovation in the area of binary analysis via its semi-dynamic engine. My focus was on the core features of analyzing the firmware images uploaded, here BugProve certainly has a competitive edge. Overall, it is a comprehensive and well-automated tool that lets you get productive right away. BugProve Team, keep up the great work!
Does it work?
We use it ourselves to detect new vulnerabilities.

IoT Bug Bounty Hunting using BugProve - Part 1

A short guide on how to use BugProve's proprietary PRIS engine to scan and evaluate firmware for unknown security vulnerabilities - so you can start your bug bounty journey now!

IoT Bug Hunting - Part 2 - Walkthrough of discovering command injections in firmware binaries

Taking bug hunting to the next level. Here are the steps that can lead you to another variation of an OS command injection vulnerability in multiple Zavio IP camera models.

CVE-2023-3959, CVE-2023-4249 - Multiple critical vulnerabilities in Zavio IP cameras

BugProve uncovers seven pre-authentication remote code execution flaws and 26 post-authentication code execution vectors in Zavio IP cameras.
How to get started?
Create an account with a single click
Upload firmware images for analysis
Get results in minutes
Dissect binaries and dig deeper
Share interactive reports with your clients
Cloud or Self-hosted deployment
We recognize the benefits of both - the choice is yours.