Start scans
BugProve operates on two primary artifact types:
- Embedded Linux firmware images that contain a complete system, or parts of it (kernel, root file system, additional file systems), or
- ELF binaries, such as executables and shared objects.
In this section, we will create and start two separate scans, one of each type.
Firmware scanning
- In order to start a firmware scan, either drag-and-drop a firmware image to the drop zone at the top of the page, or click there and browse your local file system to upload one.
- After selecting the file or dropping it into the area, the file will immediately start to upload. BugProve will try to decide whether the uploaded file was a firmware image or a single ELF binary. While there are other things you can configure here, for now simply select Let’s roll to start the analysis.
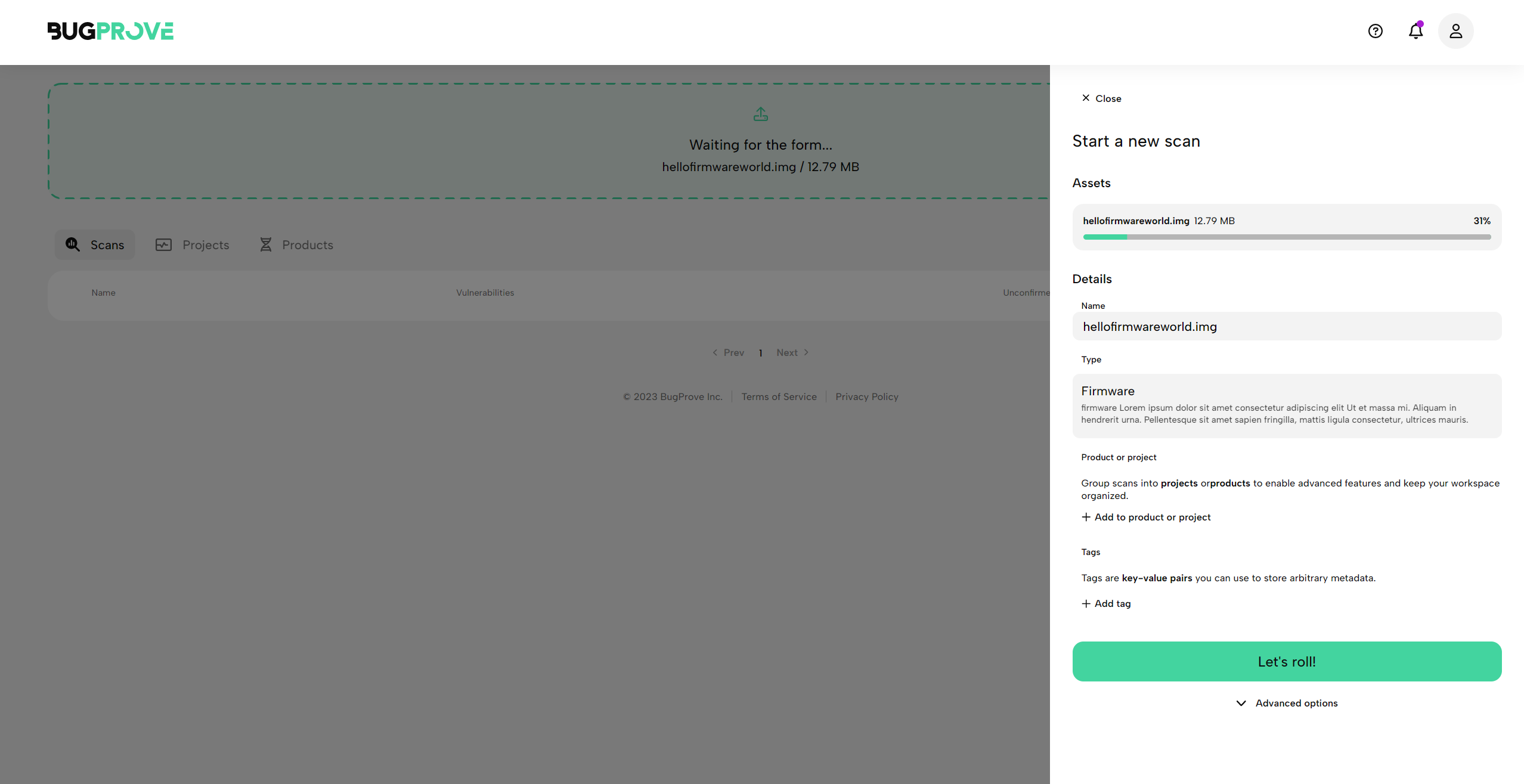
- The file will finish uploading and the analysis will begin. For firmware images, BugProve will attempt to extract useful artifacts, such as the root file system and the kernel for further analysis.
- As the scan progresses, the report comes to life and you can immediately begin inspecting preliminary results from the extraction phase. Clicking on the scan, the Overview, Cryptography and File Explorer pages should first become available. Check out the Overview page for basic information on the uploaded firmware, the underlying architecture, and binaries in the system.
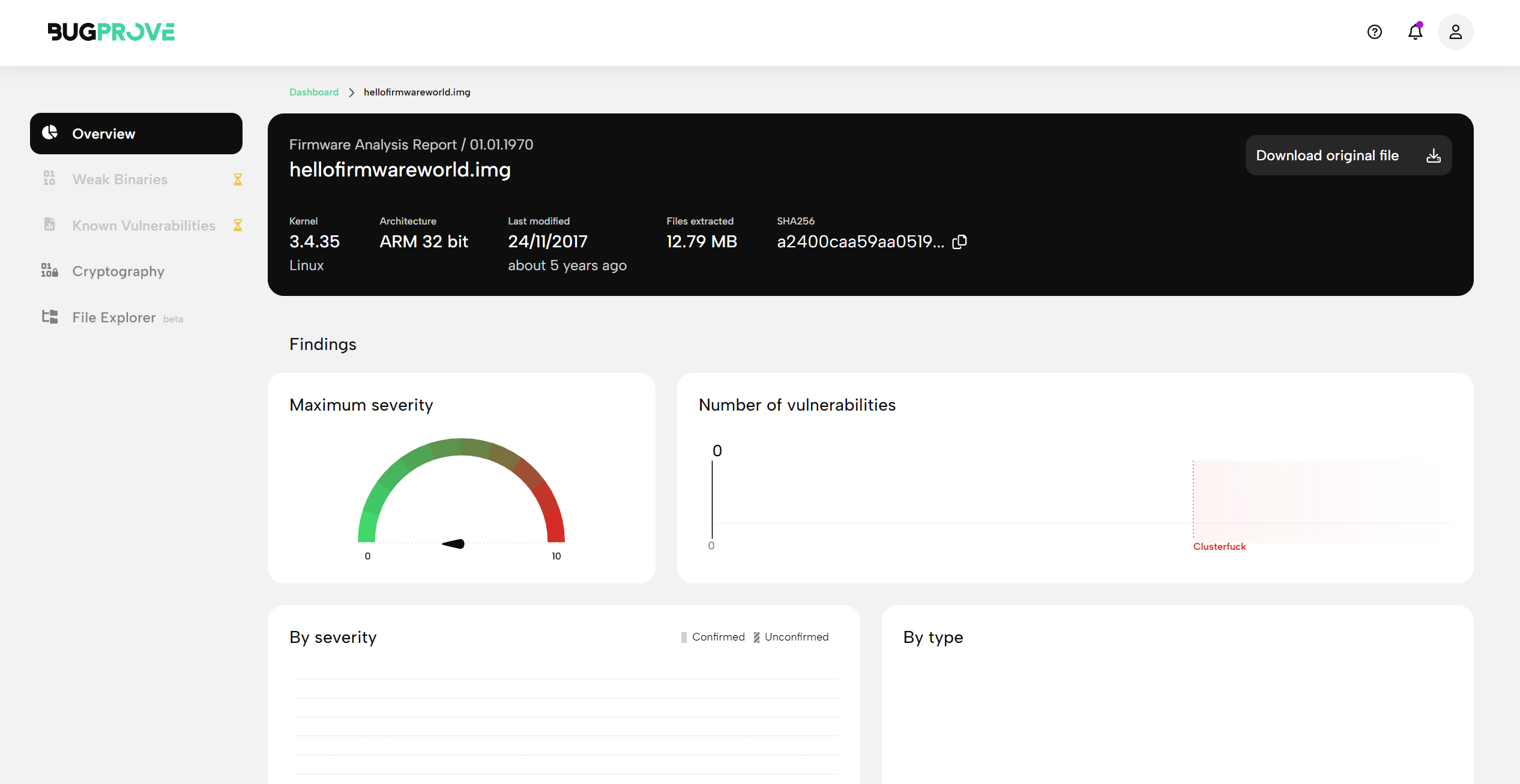
- Depending on the size of the file you uploaded, the compression algorithms and file system formats used by your image, completing the analysis might take a while. (Scanning a file smaller than a 100 MiB usually only takes about 2-3 minutes.) The system will also alert you via e-mail when the scan is complete.
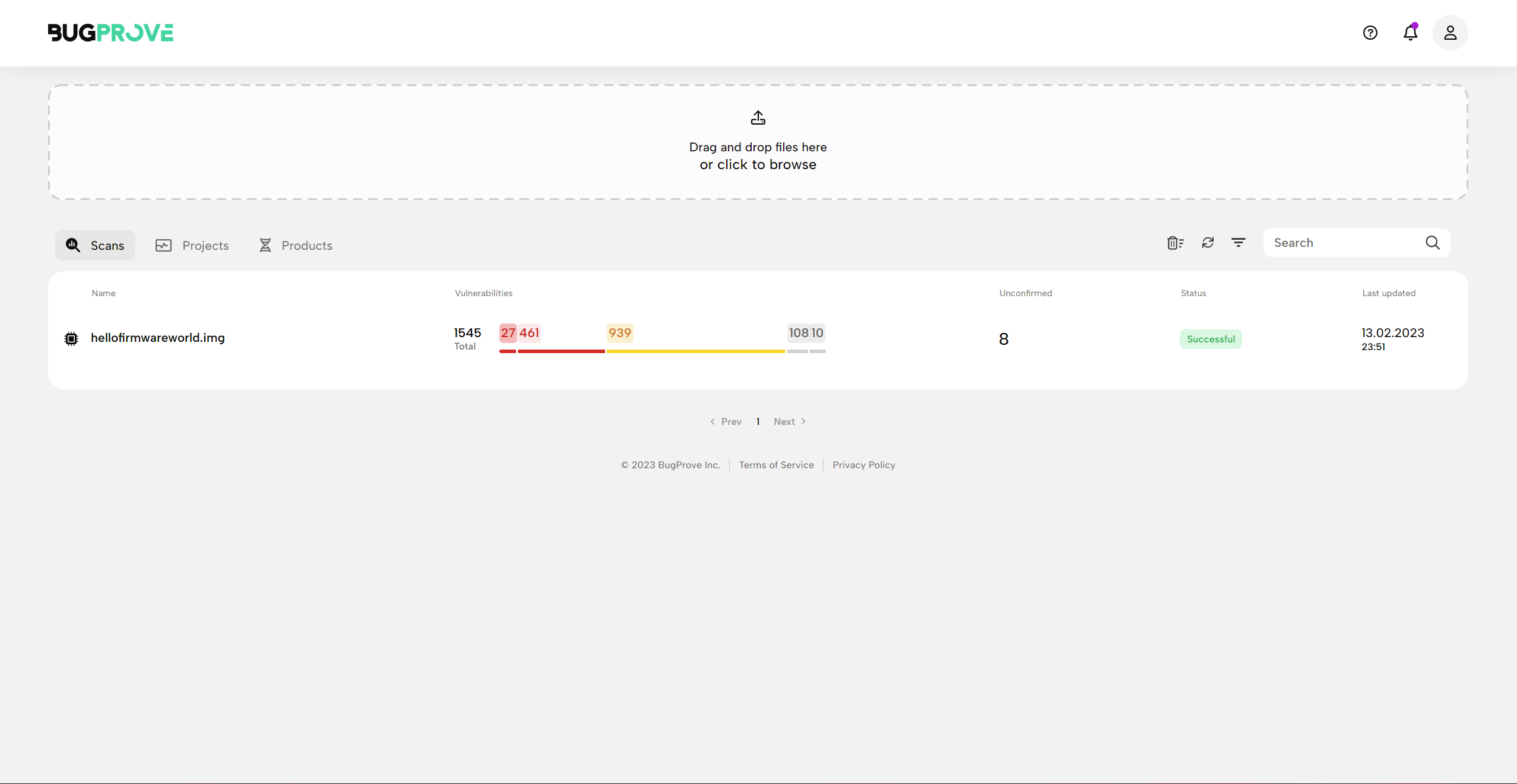
🎉 Congratulations, your first BugProve firmware scan results are ready!
ELF binary scanning
- In order to start a firmware scan, either drag-and-drop an ELF binary to the drop zone at the top of the page, or click there and browse your local file system to upload one.
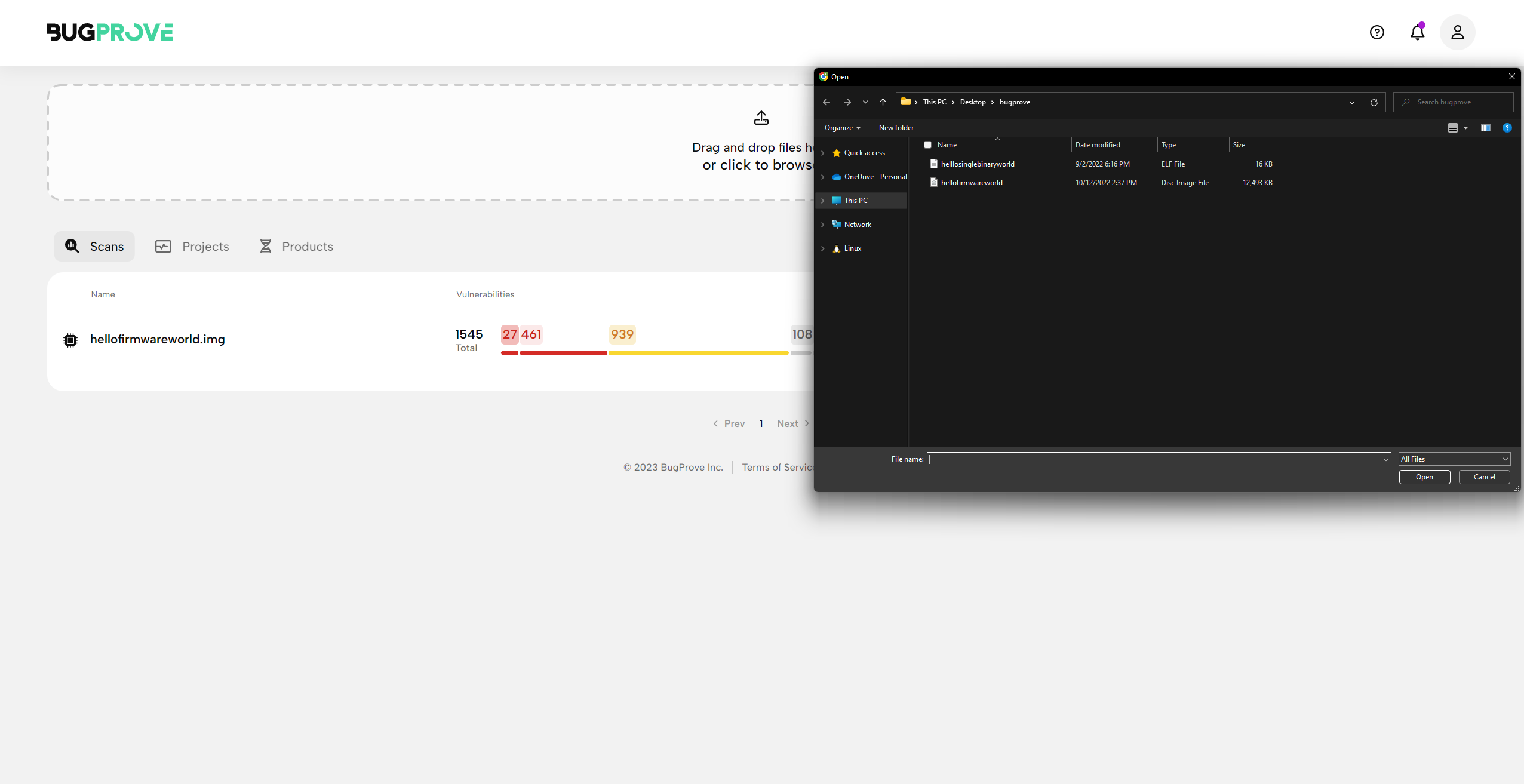
- After selecting the file or dropping it into the area, the file will immediately start to upload. BugProve will try to guess the if the uploaded file was a firmware image or a single ELF binary. While there are other things you can configure here, for now simply select Let’s roll to start the analysis.
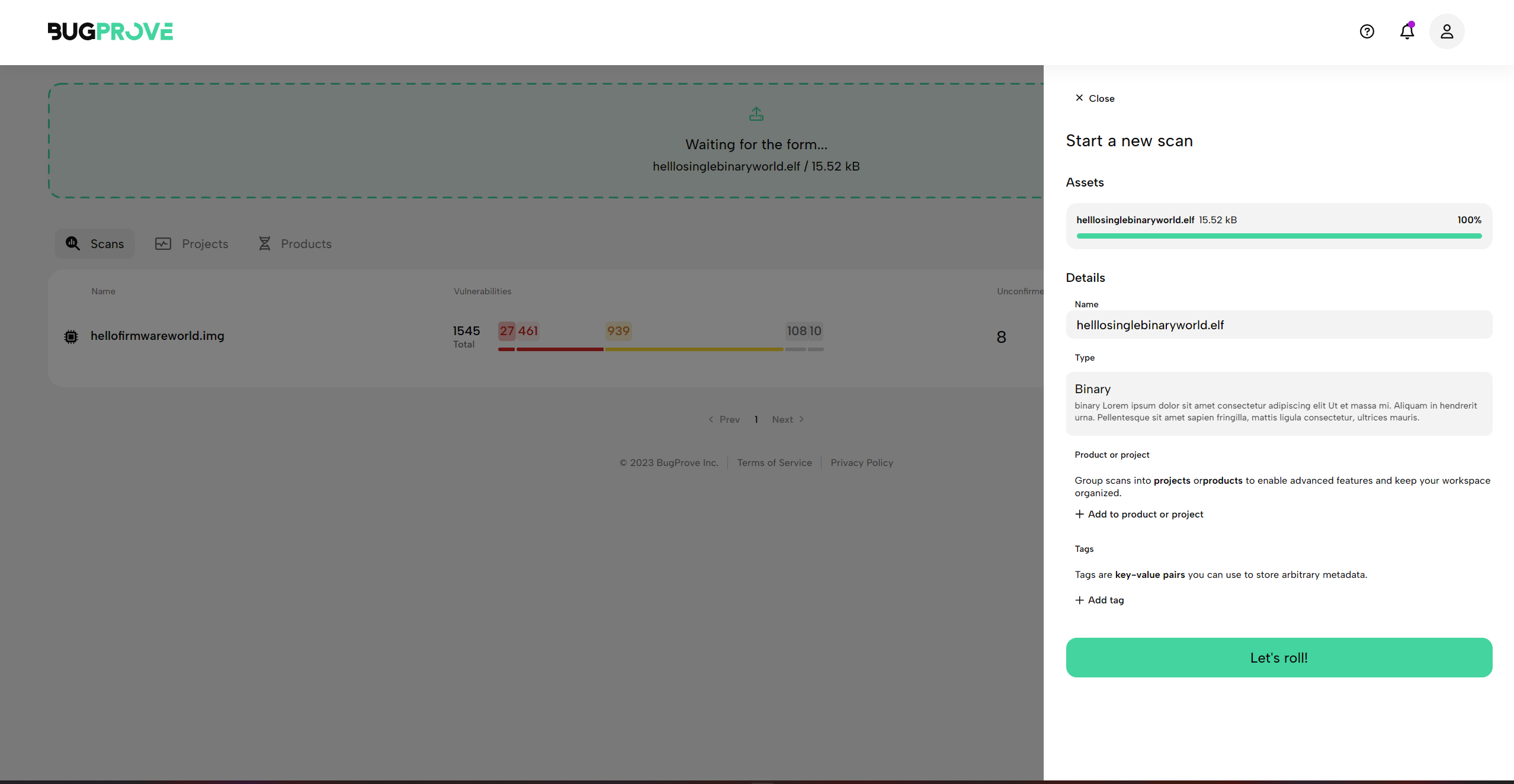
- This will start a PRIS™ scan, our semi-dynamic analysis algorithm that scans binary code for vulnerable patterns such as memory corruption issues, injection type attack vectors and a range of other issues. Depending on the size of the ELF binary, finishing the analysis might take a while. We will send you an e-mail notification once results are available.
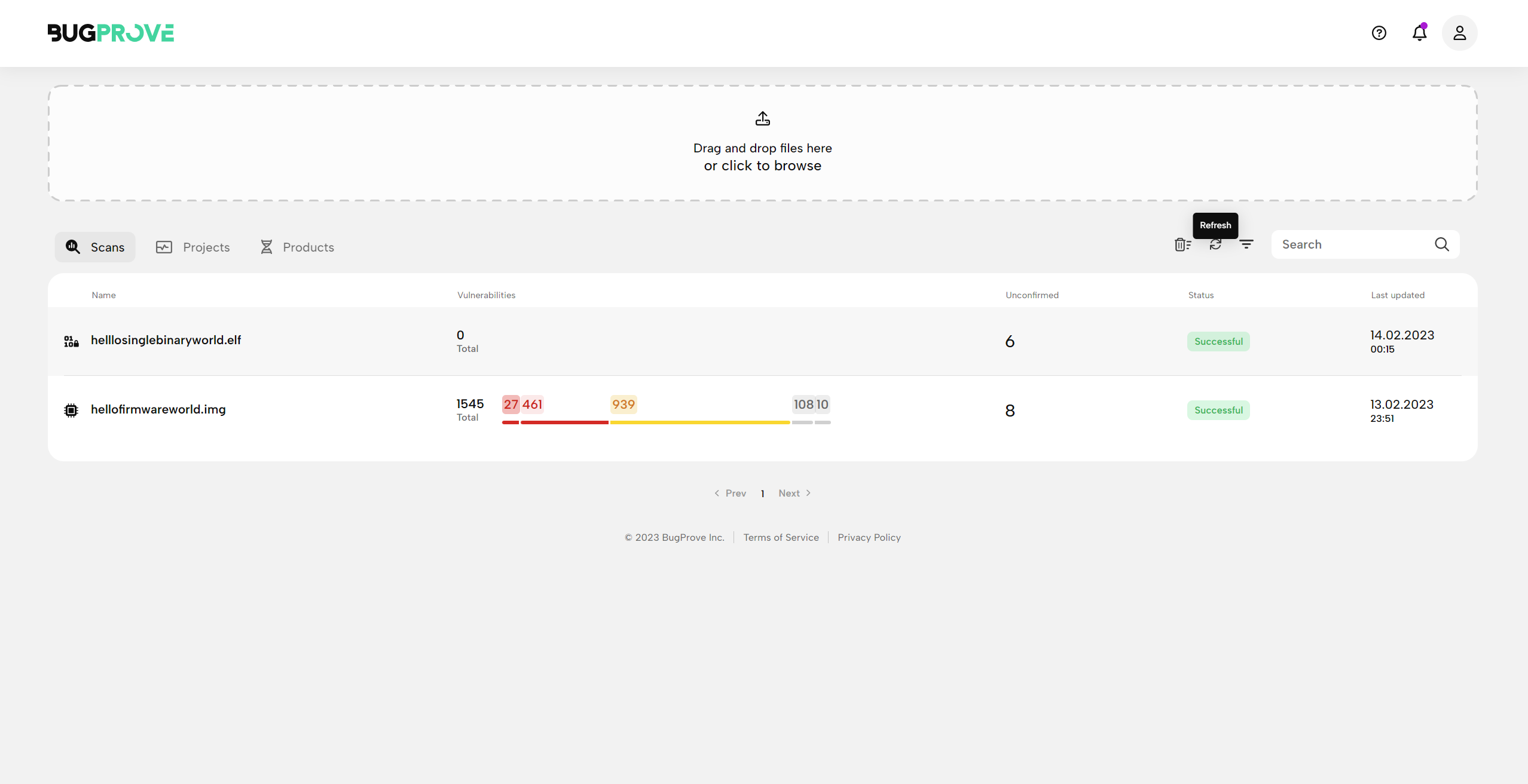
🎉 Congratulations, your first PRIS™ binary scan results are ready!
What’s next?
The scans have finished, it is time to interpret the results.