Cryptography
In the context of Internet of Things devices, ensuring the security of sensitive data is of paramount importance. Cryptographic materials, such as keys, certificates, and private keys, play a vital role in safeguarding the integrity and confidentiality of data transmitted and stored by IoT devices. However, inadequate management of these materials can result in the compromise of the entire integrity of the system and the confidentiality of important data assets. It is, therefore, important to maintain an inventory of all cryptographic material used in IoT devices, and to assess their strength against best practices and industry standards.
Using this feature, you can easily identify weaknesses, such as issues with key lengths, the use of insecure hash functions, and you can also inspect certificates in terms of their parameters expiration times.
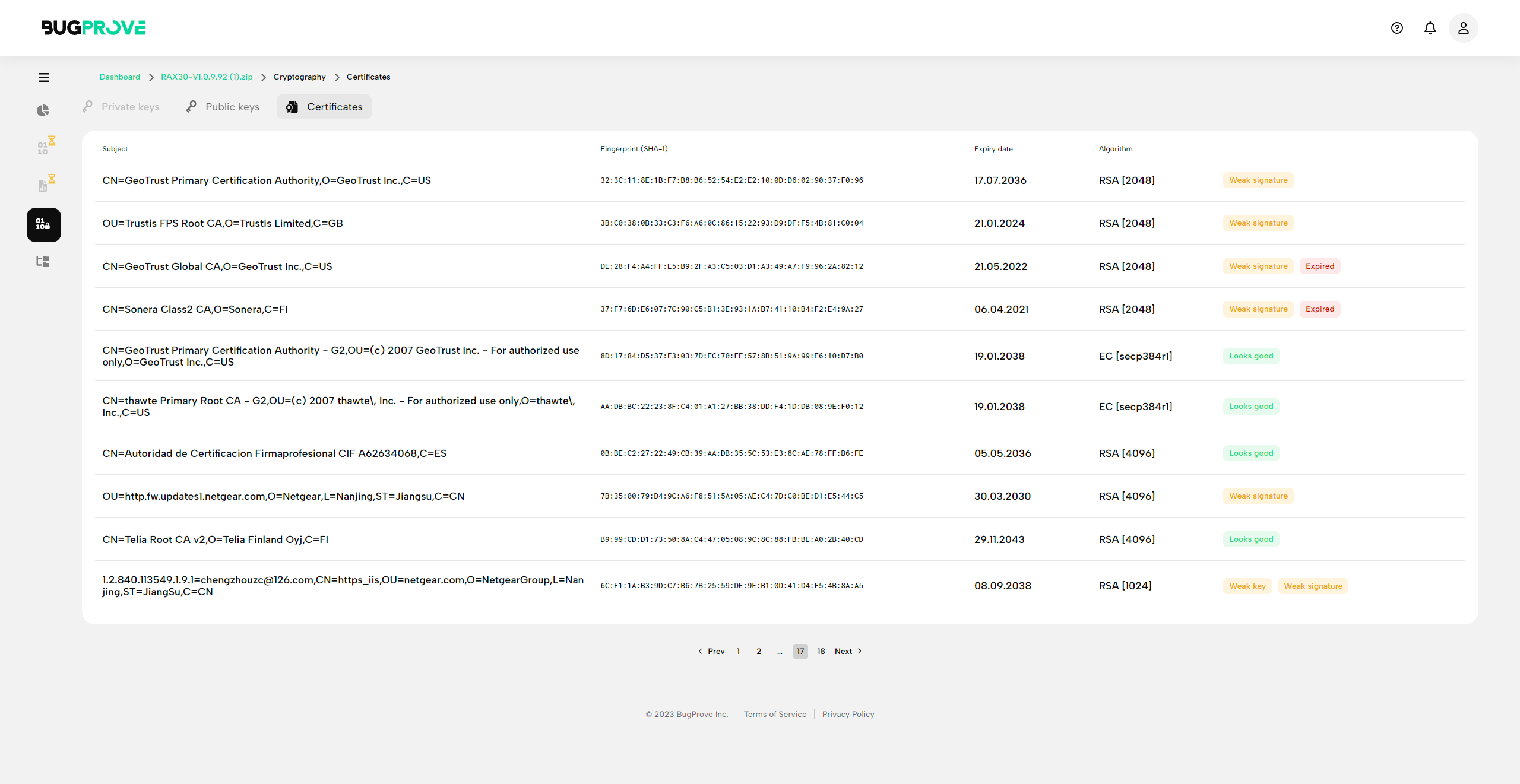
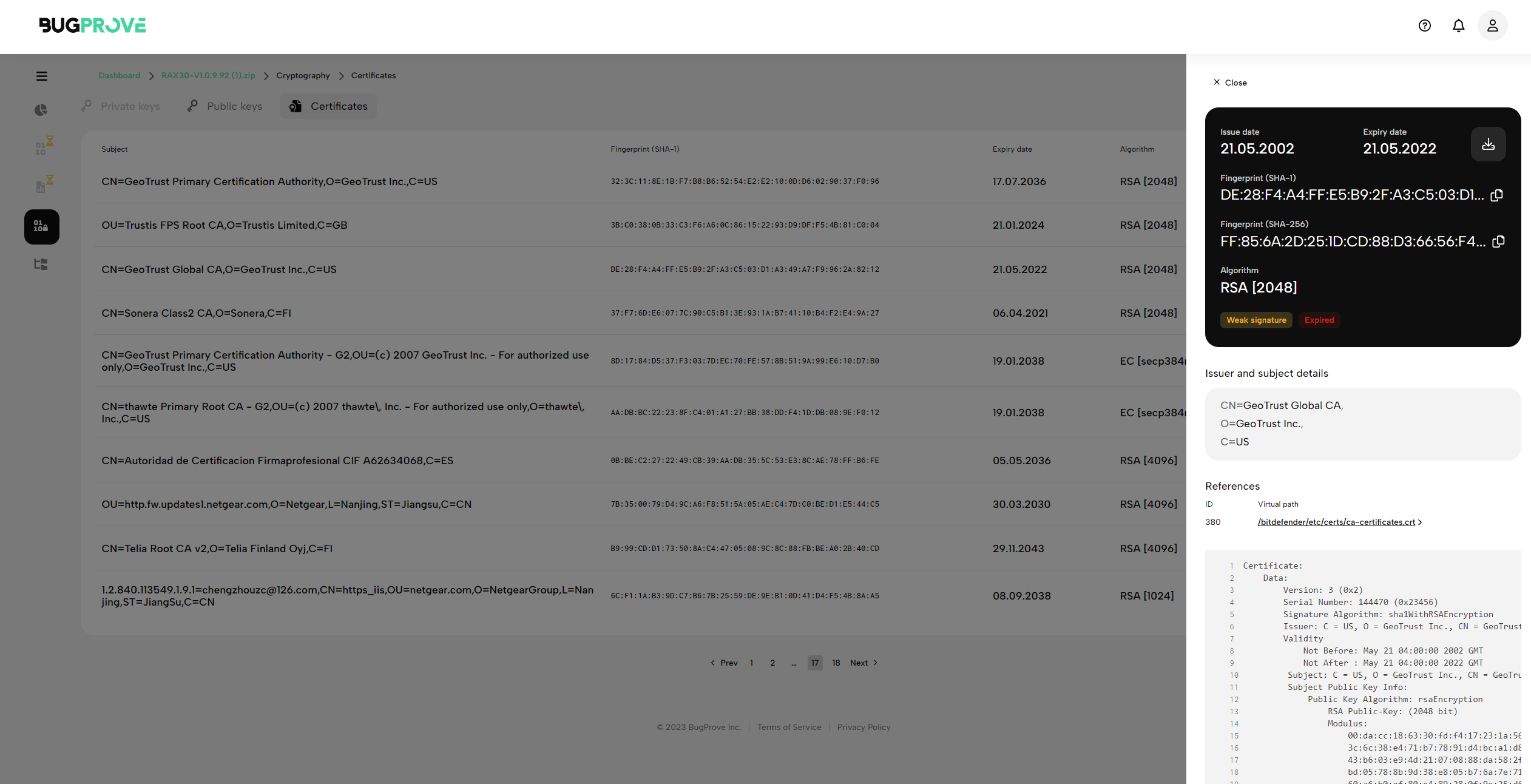
The page lists the following pieces of information on cryptographic keys and certificates found on the system.
Private keys
- Digest
- Algorithm (e.g. RSA, Ed25519)
- Key size (e.g. 2048, 256)
- Flags
- Reference to the source file (e.g. /etc/private/key.pem)
- Full OpenSSL dump of the key
Public keys
- Digest
- Algorithm (e.g. RSA, Ed25519)
- Key size (e.g. 2048, 256)
- Flags
- Reference to the source file (e.g. /home/ubuntu/key.pem)
- Full OpenSSL dump of the key
Certificates
- Subject (e.g. “CN = bugprove.com”)
- Fingerprint
- Expiry (e.g. 2022-06-02) - flagging expiring or expired certificates
- Algorithm
- Flags
- Fingerprints:
- SHA1
- SHA256
- Issuer details
- Subject details
- Reference to the source file (e.g. /home/ubuntu/certificate.pem)
- Full OpenSSL dump of the key