PRIS™
PRIS is BugProve’s semi-dynamic security analysis engine that builds on different ideas from academic research in program analysis, and its main objective is to identify those vulnerabilities that have the highest potential of becoming practically exploitable security weaknesses.
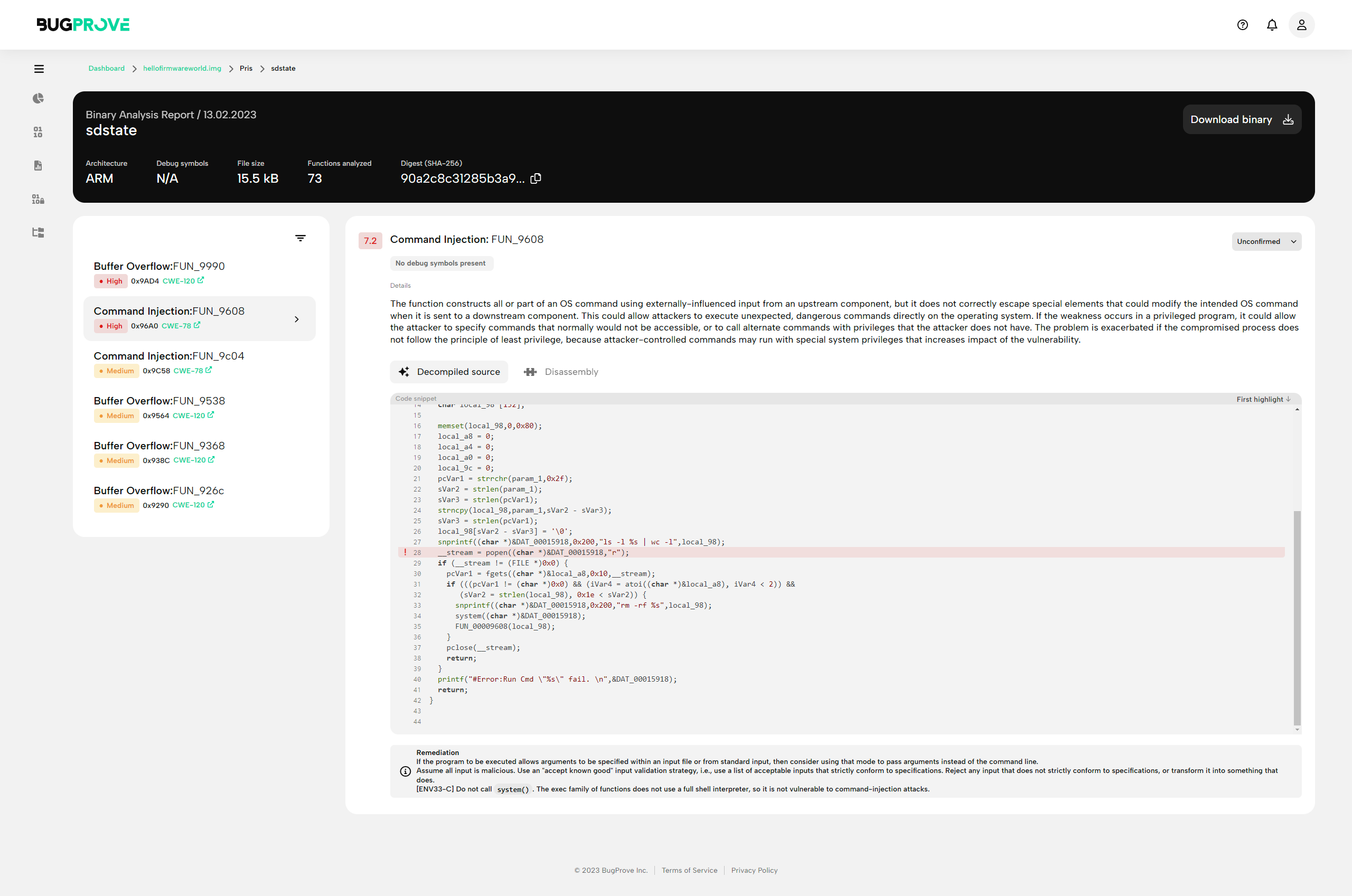
Header
- Top row
- Name of the binary (e.g. /var/www/cgi-bin/dataload.cgi) and scan date
- Tags (e.g. branch: main)
- Hash (e.g. sha256-e34eb7ae410994abcc5efad3a2862c955c57b4b62b1cc9de67a65fffff3d1def)
- Download binary button. Select this to quickly retrieve the binary for further analysis (e.g. in Ghidra or other reverse engineering software).
- Bottom row
- Architecture (e.g. ARM, MIPS-BE, x86-64)
- Debug symbols (e.g. “Not found”, “Found, unknown toolchain”, “Found, built w/ GCC 8.2“)
- File size (e.g. 15.4 MB)
- Functions analyzed (e.g. 43) Please note that BugProve’s control flow graphs reconstruction will not be complete in some cases due to the algorithmic complexity of the problem on hard instances. MIPS systems can be especially prone to these issues.
Vulnerabilities list
The findings are listed on the left side, sorted by their severity.
One row will contain the following pieces of information.
- Finding class and function name
- Memory address of vulnerability
- CWE category, linking to its MITRE description
Selecting a finding will display its details in the main component.
Finding detail
Header
- Severity score - CVSSv2 base score based on engine internal estimation parameters
- Finding name
- Debug information presence
- Binary name
Details
Description of the vulnerability class of the selected finding.
Code evidence
- Syntax highlighted decompiled C, displaying vulnerable function(s)
- Syntax highlighted disassembled ASM listing for vulnerable function(s)
- If the vulnerability can be tied to a particular callsite or instruction address, the problematic line will be highlighted
Remediation
Recommendation on fixing the vulnerability. Note that BugProve provides actionable implementation recommendations only, but it must be noted that many projects are going to require design considerations as well for fixing vulnerabilities properly.