Known vulnerabilities
Software Composition Analysis (SCA) is an essential practice in the security of IoT devices. It is crucial to identify and manage all the third-party components that are used in IoT firmware to prevent any security vulnerabilities that can be exploited by attackers. This is particularly important because many IoT devices run on embedded Linux firmware that often includes a complex mix of open-source and proprietary software components. To ensure that the IoT devices are secure, it is important to have an accurate and up-to-date Software Bill of Materials (SBOM) that lists all the components used in the firmware.
BugProve helps reduce the time and resources required to manually analyze the firmware, and provides a reliable and comprehensive inventory of all the components. The tool can automatically scan the firmware, identify open-source and proprietary components used, and generate an SBOM that can be used for further analysis and management. With an automated SCA tool, like BugProve, security professionals can easily identify and track vulnerabilities or issues associated with the components used in the firmware and take necessary action to mitigate them.
Below, we will explain the pieces of information shown on BugProve’s Known Vulnerabilities page to help you with streamlining your Product Security processes with automated dependency scanning.
Summary
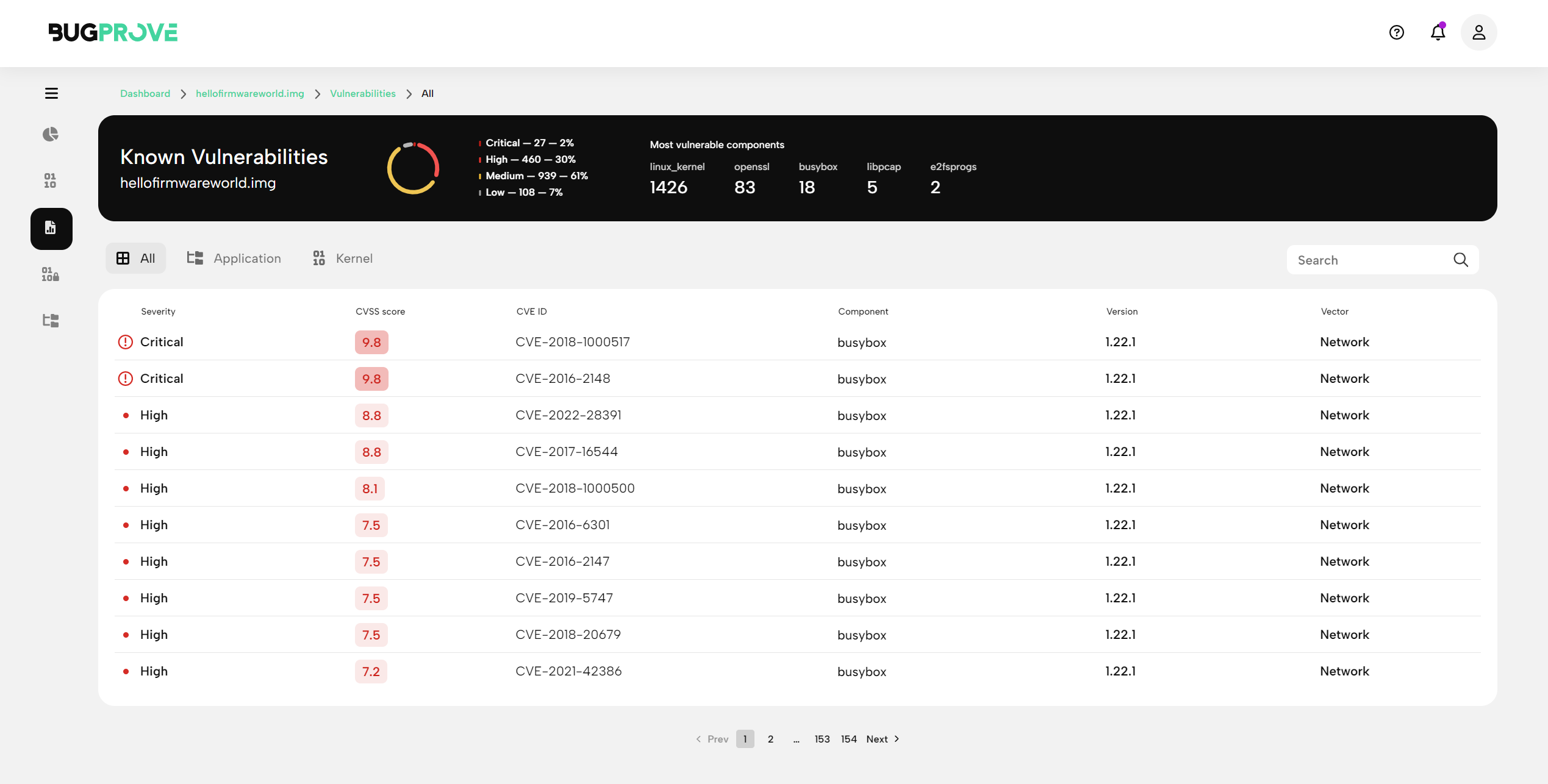
The summary view of Known Vulnerabilities will collect dependencies and associated CVEs in a table.
You can filter results using the tabulated controls.
-
All
This option shows all CVEs that BugProve found to be affecting the system. -
Application
This option filters the table to include only user-space components, such as open source libraries or executables/utilities. -
Kernel
This option filters the table to include only CVEs associated with the Linux kernel.
For each CVE row, we display the most important information:
- Severity
- CVSS score
- CVE ID
- Component name
- Component version
- Attack vector
CVE Details
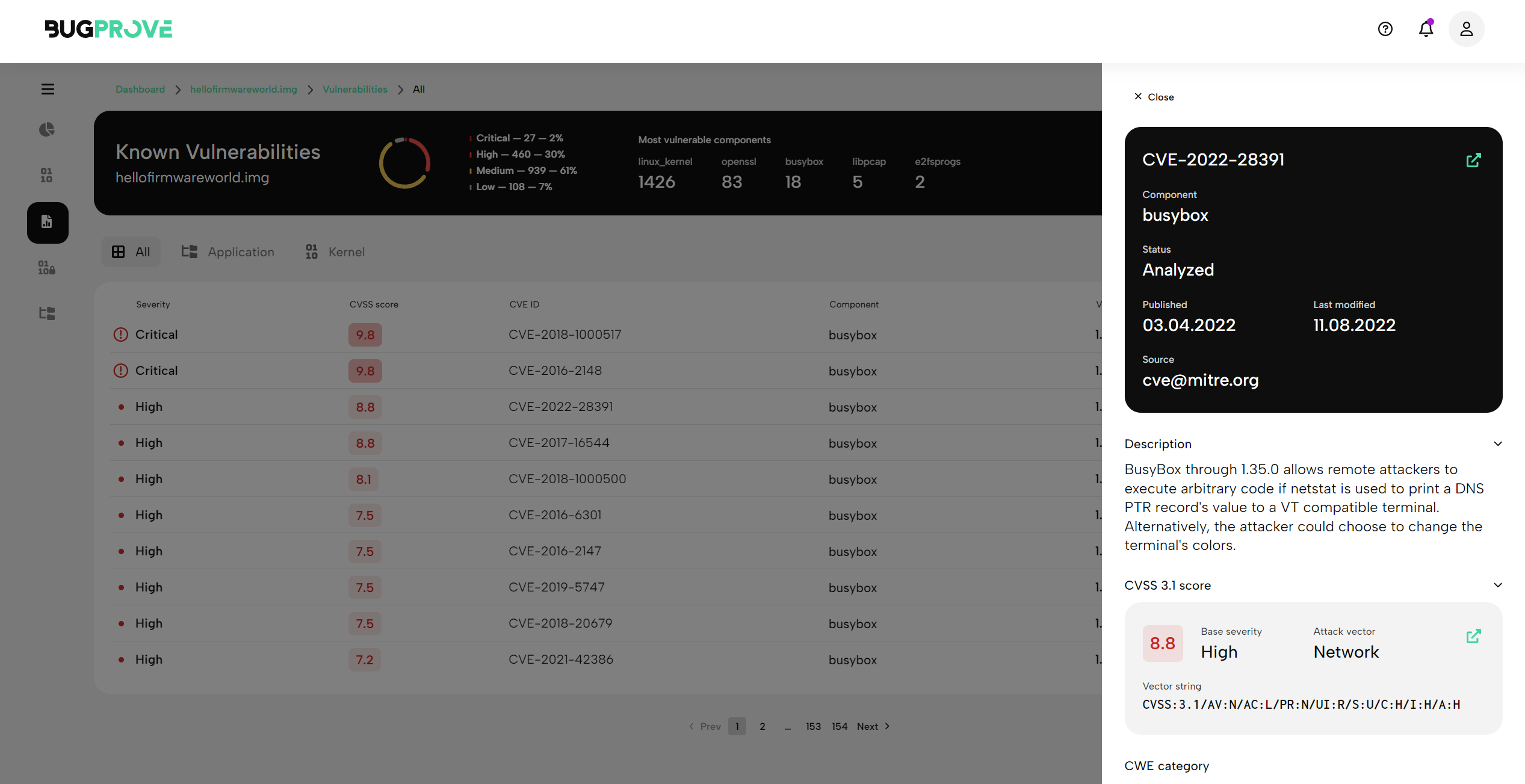
Clicking on a CVE, will bring up the detailed view including a summary, in-depth descriptions, and solutions for mitigation.
You will be able to see the following data.
Header
The header contains essential basic information on the CVE.
- Component name
- Status
- Published
- Last modified
- Source
Description
The description provides detail on the component version and the particular attack vector, including technical information.
CVSS score
We display the appropriate CVSS version score, including:
- Base severity
- Attack vector
- Vector string
CWE category
This is the common weakness enumeration category for the CVE. For more information, please refer to https://cwe.mitre.org/.
References
Links to sources providing more technical information on the particular issue.
Affected files
We link the files on the file system that are affected by the CVE.