Back to the articles
Product Update #5

Today, we are releasing the largest update to our platform since our launch in February. Some of the changes I will be talking about have been silently released (as usual) during the past week or two - but there are quite a few that are brand new.
A new way to browse findings
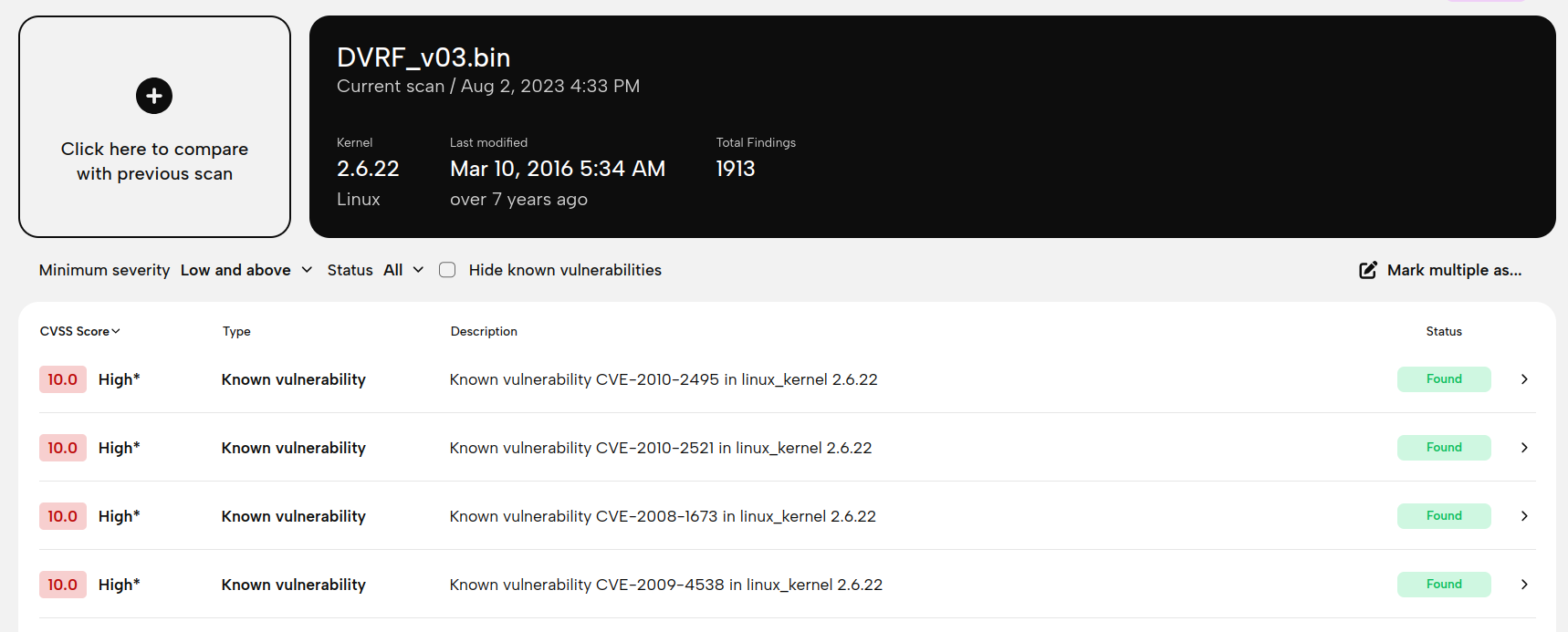
Perhaps the most important output of our scans is the list of findings. Previously, there was no single place where you could review these, and to be honest there was very little transparency on what we consider a "finding". The Known Vulnerabilities page we had sort of looked like such a place, but it did not include everything. So let me introduce you to the new Findings page: a single, convenient location to review all security-relevant findings. Clicking on a finding will take you to other pages in the scan report, and you can also accept or reject findings right here.
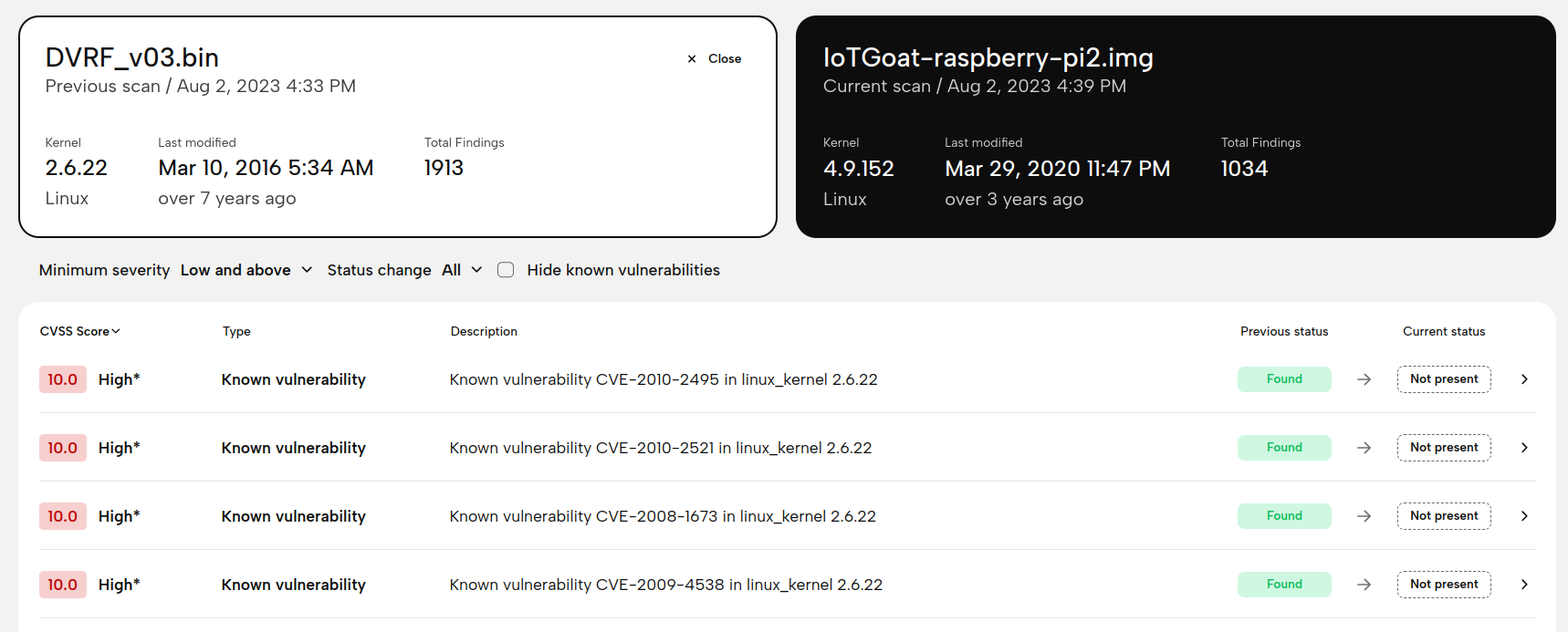
This new page also offered us the unique opportunity to add an often-requested feature: a way to compare the results of two scans. This can, for example, help you determine whether a newer version of the same firmware image fixes a particular vulnerability or not. Filters are available to highlight only findings that changed between versions.
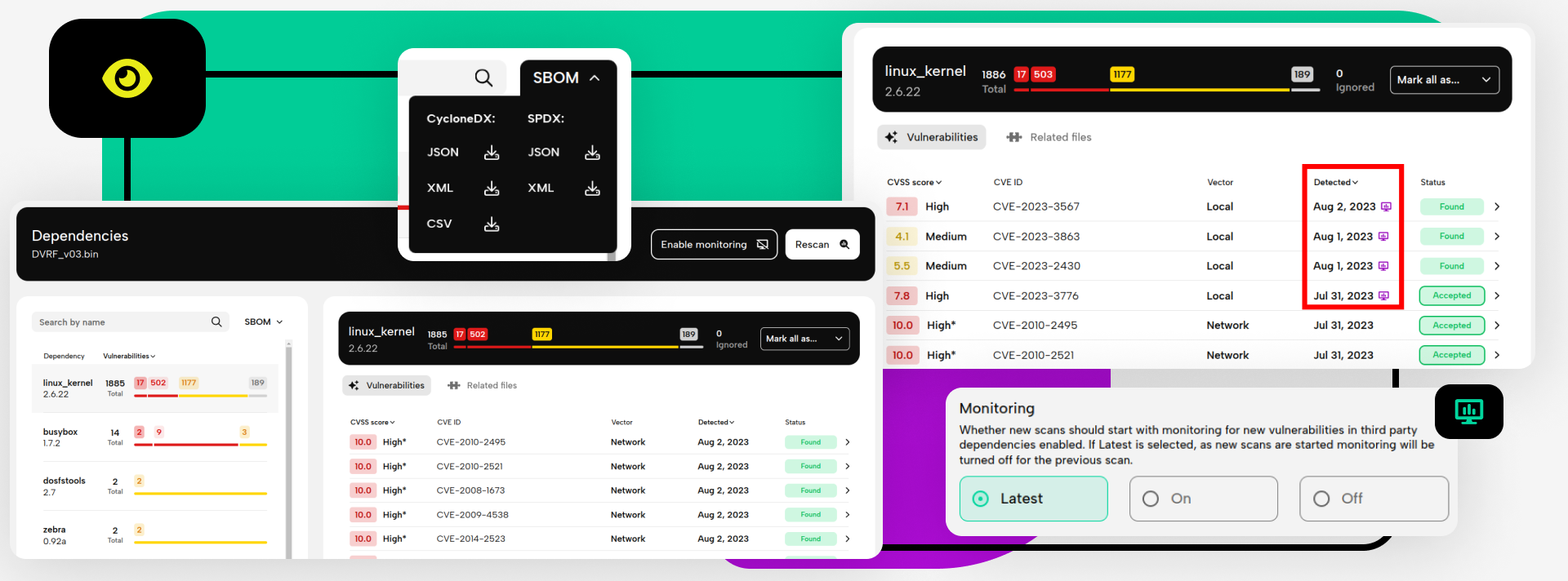
Dependencies and SBOM export
One of the steps we perform during every scan is the identification of third-party dependencies. Unfortunately, there wasn't any way to see a list of these, as we only used the list internally to look for known vulnerabilities, and we have shown those without any grouping. Dependencies without known vulnerabilities weren't shown at all. This changes with this update - Dependencies is now a dedicated report page. Together with the new Findings page, it replaces the old Known Vulnerabilities page, and shows a list of all identified third-party dependencies, as well as their known vulnerabilities and other metadata (including the list of files we used to identify it). You can also accept or reject all findings related to a single dependency, instead of going through them one by one.
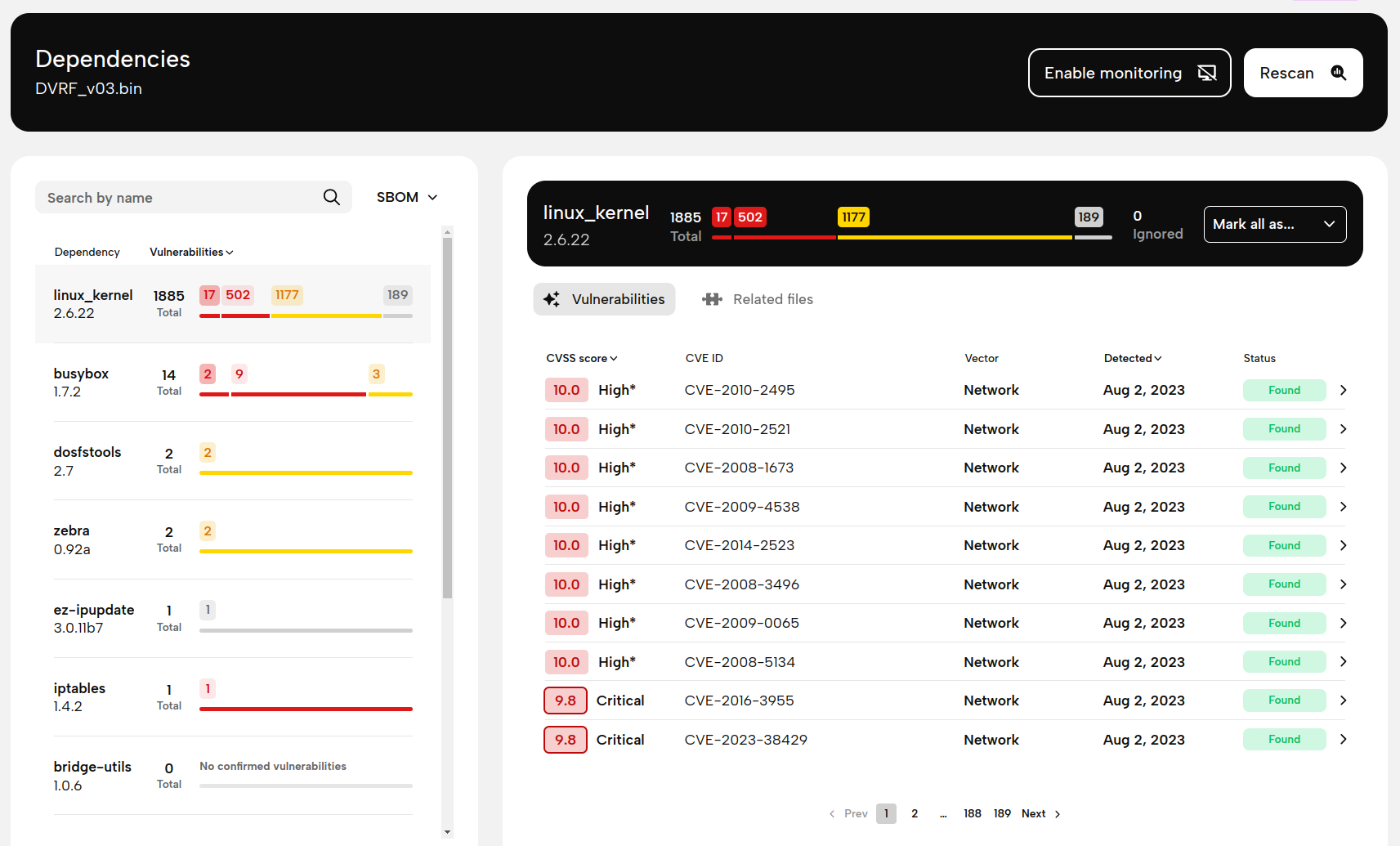
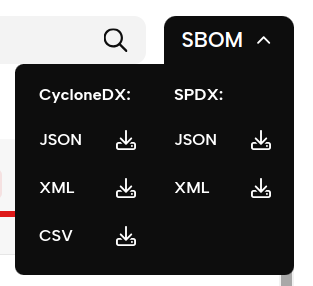
Additionally, you can now export this list - the reverse-engineered SBOM of the firmware image - in CycloneDX and SPDX format. If you choose to export a CycloneDX SBOM, we even include the list of known vulnerabilities, as well as their state (based on whether you accepted or rejected individual vulnerabilities).
Monitoring
If you have a keen eye, you might have noticed the new buttons in the header of the Dependencies page on the screenshot in the previous section. From now on (if you have an Enterprise plan), you can enable monitoring for new vulnerabilities for the dependencies we identified. For scans with monitoring enabled, whenever a new CVE appears in the National Vulnerability Database that affects the firmware image, you will get e-mail notifications and the report will update to include the newly identified vulnerability. (You will also get notified if the severity or classification of a vulnerability changes, or if it turns out that it does not affect the firmware image after all.)
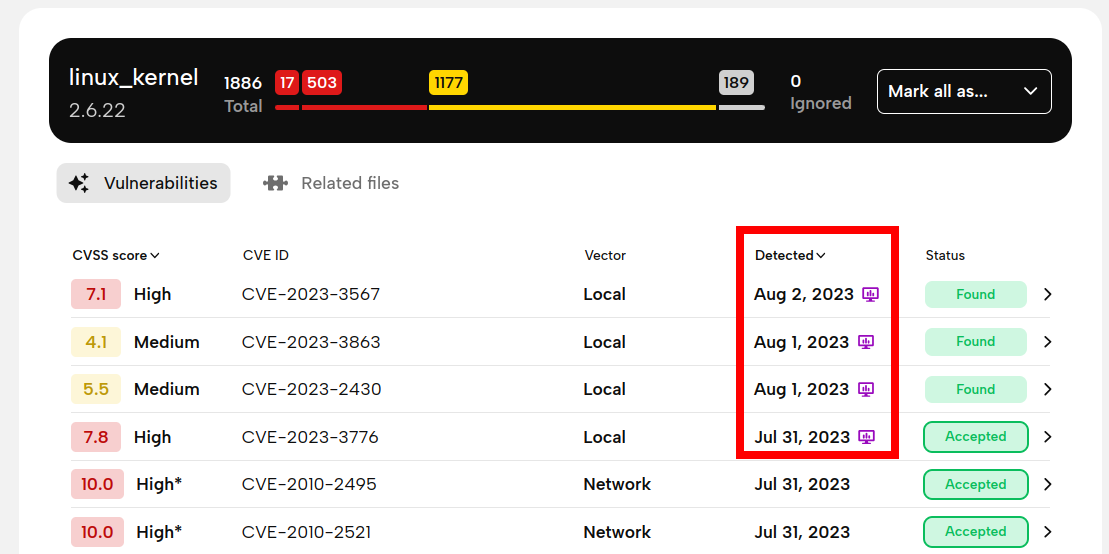
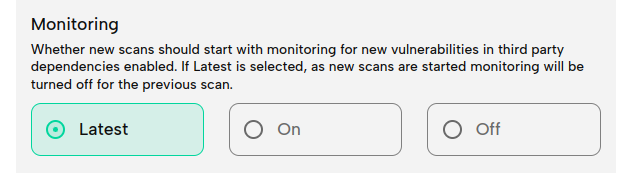
Monitoring is tightly integrated with product- or project-based scan grouping. When you start new scans and assign them to a product or project (and you should really consider doing so, it keeps your workspace neat and organized), the scan will by default inherit their monitoring policy, which can automatically enable monitoring. Products also support a special monitoring policy, "Latest" - this will turn monitoring off for the previous scan when a new one succeeds, ensuring that only the latest version of the firmware image is monitored for a particular product.
When you enable monitoring (and you can enable it for older scans, should you wish to), the scan will immediately be updated to reflect new vulnerabilities that were discovered since the scan was originally performed. You can trigger this without enabling monitoring using the Rescan button, if you want to bring the scan up to date. Manual rescans are available in all paid plans.
Watch me
A new feature related to (but not exclusive to) monitoring is the ability to "watch" scans, projects or products. Previously, you received e-mail notifications for all scans that were started in your workspace, and there was only a global opt-out of all such messages in the Profile page. From now on, you will only receive notifications (including vulnerability alerts) for scans you directly watch, or which are assigned to a project or product you watch. By default, you watch new scans you start and all products and projects you create, but you can change this with a single click. (This global opt-out is still there, if you need it.)
Exploitability
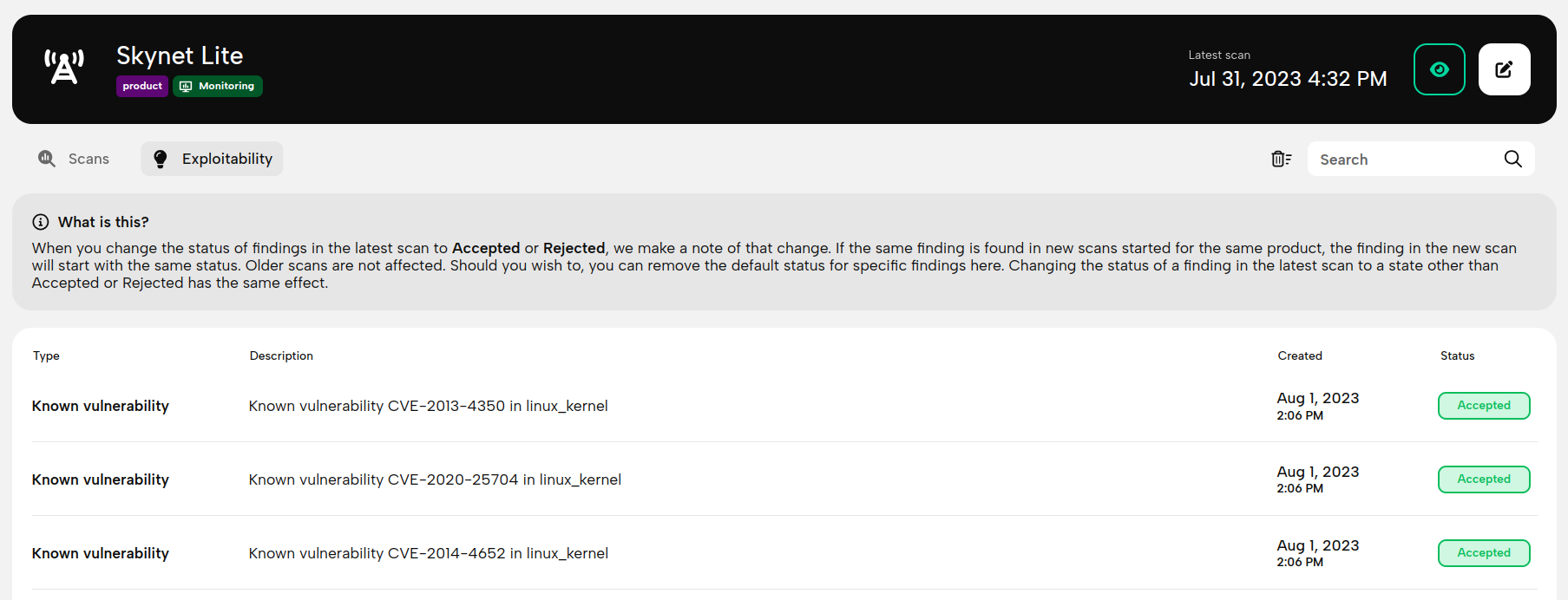
One of the less documented (okay, undocumented) features we have had for a while is that scans grouped by product tracked and shared exploitability information. If you accept or reject a finding in the latest scan that is assigned to a product, we make note of it. If the same finding is found in subsequent scans assigned to the same product, it will be accepted or rejected immediately. To expose this feature, and give you more control, we have added the Exploitability page - where you can see the list of findings that were accepted or rejected for a particular product.
Other improvements
- File uploads should fail less often, and can now be retried
- Progress bars will no longer take a step back after reaching 70%
- Most tables now have friendlier empty and loading states
- Added little icons to indicate if a scan report is shared via link
- Improved positioning of chart labels
- Better diagnostic messages for failed scans
- Slightly better experience when using (unsupported) mobile browsers
- File Explorer header finally aligns with the rest of the section headers
What's next
We have our work cut out for us - our documentation is still playing catch-up with new features, and since we planned to focus on UX improvements and better documentation for the next few weeks anyways, we will take a stab at improving the situation.