Back to the articles
CVE-2024-35467 - Stack-based buffer overflow vulnerability in the WPS method on ASUS's RT-AC87U devices


Table of contents
Disclaimer: The following vulnerability was detected by BugProve's security research team conducting analysis on publicly available products/firmware. Firmware uploaded by users to BugProve's platform have no connection with any of our own research projects. For more information, check out our Vulnerability Disclosure Policy.
Disclosure timeline
Mar 14, 2024: BugProve reported the issues to ASUS.
Mar 28, 2024: Asus provided beta version 3.0.0.4.382.52546 with a security fix for testing.
May 22, 2024: Requested a CVE ID from MITRE.
May 29, 2024: MITRE assigned CVE-2024-35467.
July 18, 2024: Coordinated public release of advisory.
Affected products
ASUS’s RT-AC87U devices running firmware version 3.0.0.4.382.52546 and earlier are affected.
Product URLs
Summary
A buffer overflow vulnerability exists when some versions of the RT-AC87U devices improperly handle user-provided input. This vulnerability may allow an authenticated attacker to cause a system crash or remotely execute code on an affected device.
The rc binary, responsible for the system's initial setup, implements the WPS functionality with a specific flaw. An overly long value provided as wps_sta_pin can cause the system to crash and reboot. An attacker may leverage this vulnerability to trigger a denial-of-service condition on the targeted system.
Details
The following analysis has been performed on firmware version 3.0.0.4.382.52545 of ASUS's RT-AC87U device.
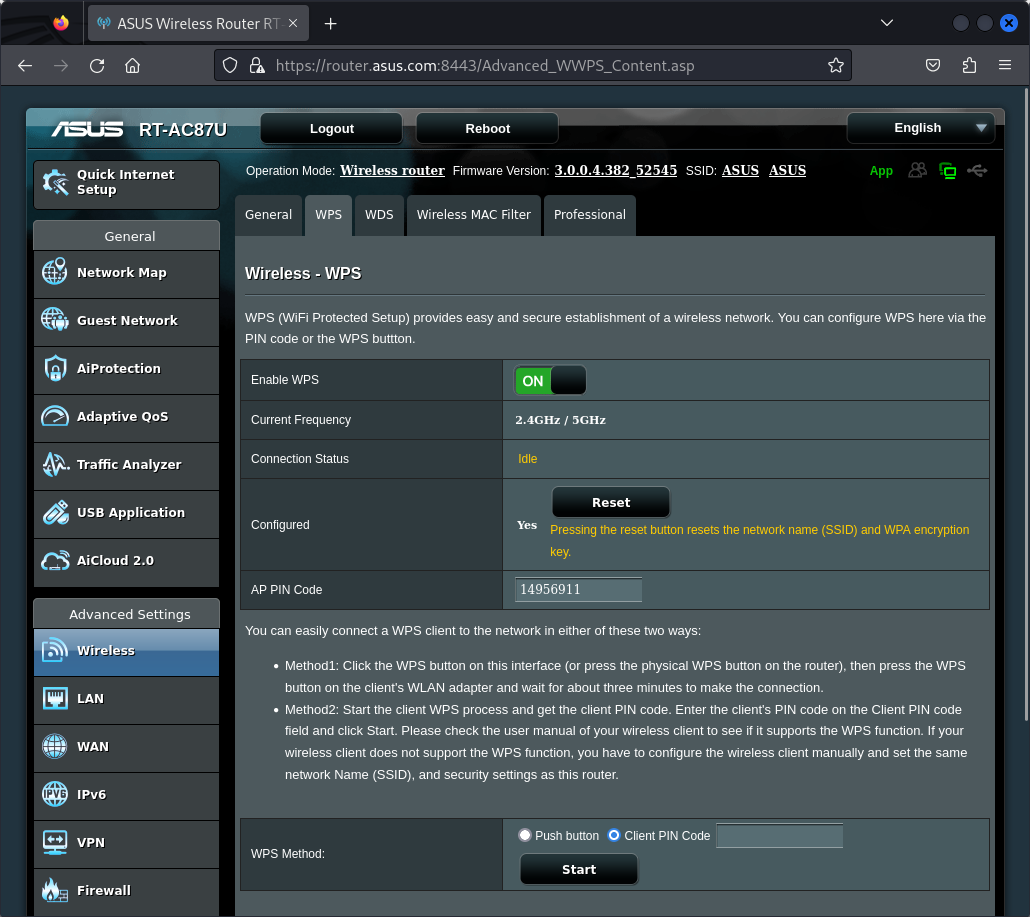
The advanced Wireless - WPS page of the device appears to be affected by a stack buffer overflow vulnerability, which can be triggered by initiating the WPS process with the Client PIN Code field set to an overly long value, as Figure 1. shows.
PRIS, BugProve's proprietary firmware analysis engine, revealed that the vulnerability lies in the FUN_00066fc8() function within the rc binary. The program constructs a string from the various WPS parameters, including the user-provided wps_sta_pin to start the WPS process. Figure 2. shows the result of a zero-day scan performed on the affected rc binary.
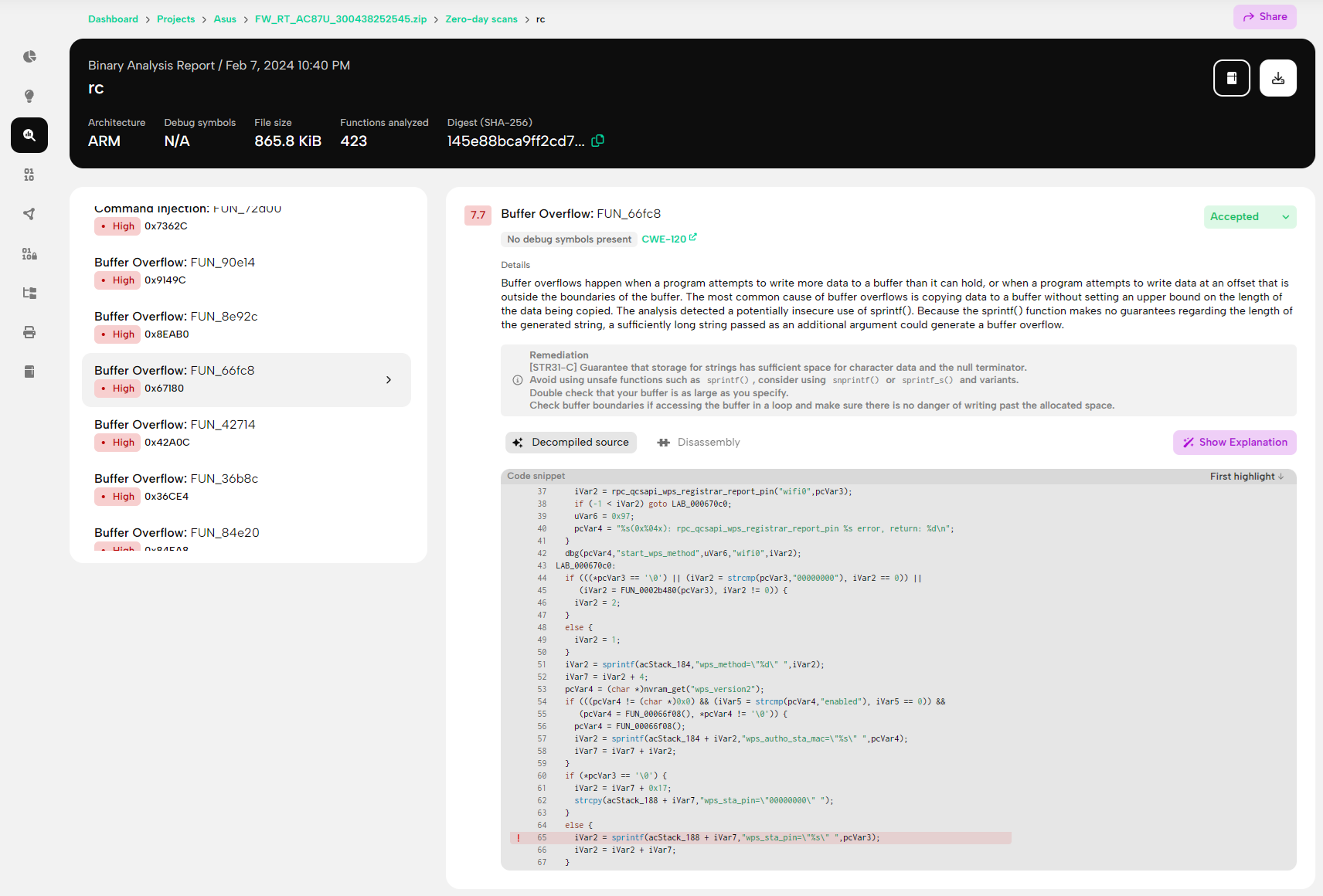
The following is the relevant excerpt of the decompiled source code of the affected FUN_00066fc8() function in the rc binary, showing the wps_sta_pin parameter copied to a stack buffer with the sprintf() function.
int FUN_00066fc8(void) {
...SNIP...
iVar2 = sprintf(acStack_184,"wps_method=\"%d\" ",iVar2);
iVar7 = iVar2 + 4;
pcVar4 = (char *)nvram_get("wps_version2");
if (((pcVar4 != (char *)0x0) && (iVar5 = strcmp(pcVar4,"enabled"), iVar5 == 0)) &&
(pcVar4 = FUN_00066f08(), *pcVar4 != '\0')) {
pcVar4 = FUN_00066f08();
iVar2 = sprintf(acStack_184 + iVar2,"wps_autho_sta_mac=\"%s\" ", pcVar4);
iVar7 = iVar7 + iVar2;
}
if (*pcVar3 == '\0') {
iVar2 = iVar7 + 0x17;
strcpy(acStack_188 + iVar7,"wps_sta_pin=\"00000000\" ");
}
else {
iVar2 = sprintf(acStack_188 + iVar7,"wps_sta_pin=\"%s\" ", pcVar3);
iVar2 = iVar2 + iVar7;
}
...SNIP...
return 0;
}
The vulnerability arises from the use of the sprintf() function to copy the value of pcVar3 into the acStack_188 buffer. However, the destination buffer's size remains unchecked, potentially causing an overflow if the input string size in pcVar3 surpasses the available space in acStack_188. The following excerpt from the start_wps_method() function indicates that the affected code may originate from the Broadcom SDK's services.c file, located in the wps-broadcom.c file within the Asuswrt-Merlin firmware's code repository.
int start_wps_method(void) {
char *wps_sta_pin;
char buf[256] = "SET ";
int len = 4;
...SNIP...
if (!HAPD_DISABLED()) {
...SNIP...
} else
{
if (strlen(wps_sta_pin) && strcmp(wps_sta_pin, "00000000") && (wl_wpsPincheck(wps_sta_pin) == 0))
len += sprintf(buf + len, "wps_method=\"%d\" ", WPS_UI_METHOD_PIN);
else
len += sprintf(buf + len, "wps_method=\"%d\" ", WPS_UI_METHOD_PBC);
if (nvram_match("wps_version2", "enabled") && strlen(nvram_safe_get("wps_autho_sta_mac")))
len += sprintf(buf + len, "wps_autho_sta_mac=\"%s\" ", nvram_safe_get("wps_autho_sta_mac"));
if (strlen(wps_sta_pin))
len += sprintf(buf + len, "wps_sta_pin=\"%s\" ", wps_sta_pin);
else
len += sprintf(buf + len, "wps_sta_pin=\"00000000\" ");
len += sprintf(buf + len, "wps_action=\"%d\" ", WPS_UI_ACT_ADDENROLLEE);
len += sprintf(buf + len, "wps_config_command=\"%d\" ", WPS_UI_CMD_START);
nvram_set("wps_proc_status", "0");
nvram_set("wps_proc_status_x", "0");
len += sprintf(buf + len, "wps_pbc_method=\"%d\" ", WPS_UI_PBC_SW);
len += sprintf(buf + len, "wps_ifname=\"%s\" ", ifname);
dbG("wps env buffer: %s\n", buf);
...SNIP...
nvram_set("wps_env_buf", buf);
nvram_set_int("wps_restart_war", 1);
set_wps_env(buf);
}
...SNIP...
return 0;
}
The start_wps_method() function constructs a space-separated string from the various WPS parameters as key=value pairs and stores it as wps_env_buf in NVRAM. However, the function does not ensure that the final string will fit the available space in the buf array. Hence, a long enough wps_sta_pin value can overflow the buffer into adjacent memory and cause the system to crash.
Figure 3. demonstrates how to reproduce the vulnerability by sending the HTTP request below using the curl utility as an authenticated user and a long wps_sta_pin parameter.
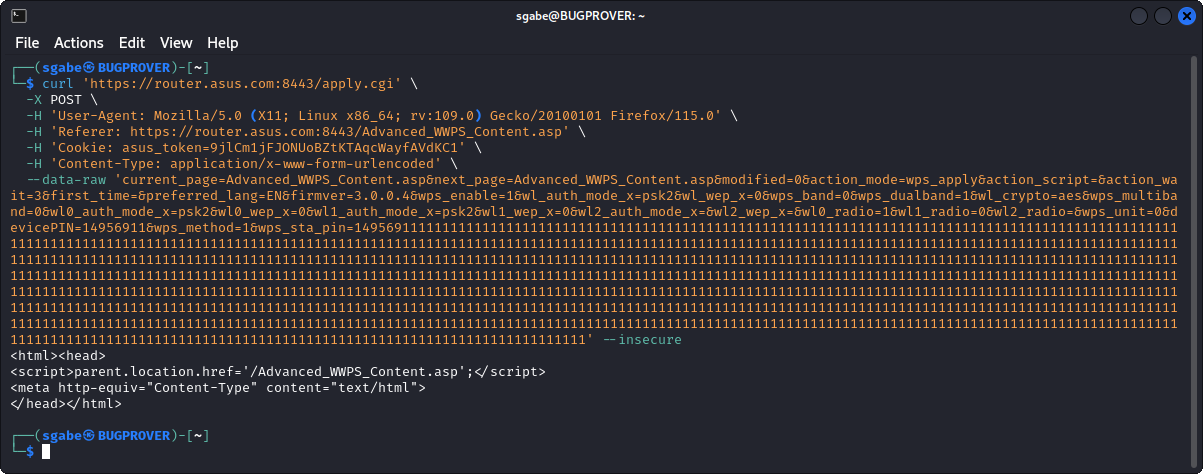
Upon receiving the above request, the device immediately stops responding, eventually reboots and comes back online as indicated by the following diagnostic messages in the /jffs/syslog.log file and the output of the dmesg command.
The vulnerability has been confirmed as an authenticated user on an RC-AC87U device, but other devices with the WPS functionality implemented using the same codebase and practices might also be affected.
Acknowledgments
The vulnerability was found by Gábor Selján at BugProve, using BugProve PRIS™. Thanks to ASUS’s PSIRT team for the effective coordination process.