Back to the articles
Announcement: BugProve is available on-premise!


Ever since the launch of our platform as a cloud-hosted service, we understood that many organizations have specific requirements or preferences when managing their infrastructure and data.
BugProve was meticulously designed with security in mind, however, having formerly worked at infosec teams of large corporations, we knew that compliance with strict industry-specific regulations often prevents the use of hosted SaaS altogether.
In recent months, in particular, we've had several customers telling us they're interested in exploring BugProve for their company but not allowed to upload items that fall under the category of protected assets per information security policies in place.
We are excited to announce a significant update that finally addresses this need head-on - BugProve is now available for on-premises deployment to any enterprise interested in employing our firmware analysis and vulnerability management platform.
This provides flexibility for customers with complex IT infrastructure and standardized security controls. On the other hand, we built it to retain from the cloud version what is most important: unifying product security and development teams to protect device firmware from vulnerabilities and misconfigurations.
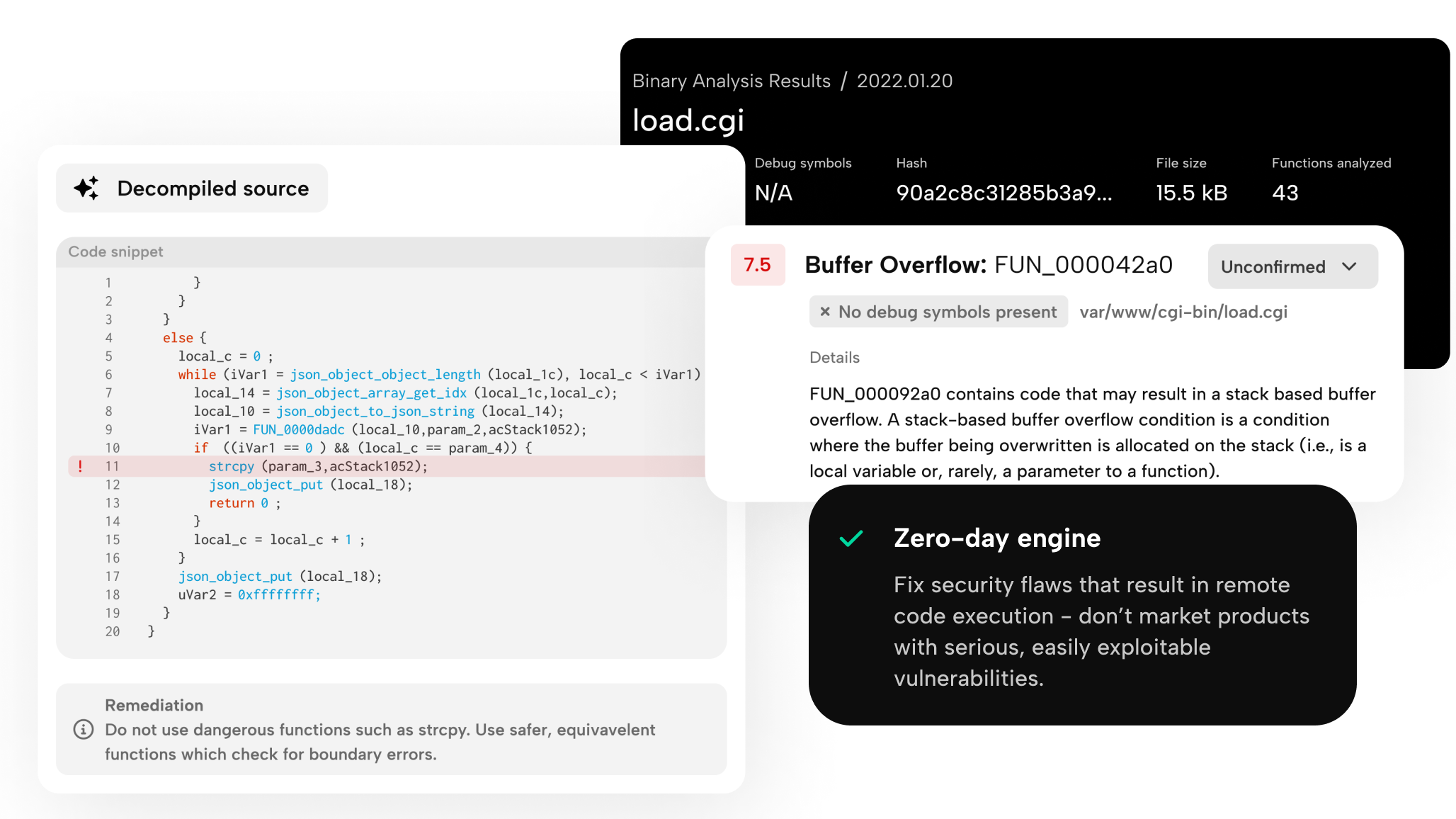
What you get with on-premise
Our product team has poured countless hours into making this update a reality, and we are especially happy to report that essentially all of BugProve’s features and capabilities remain available for customers opting for this new deployment model.
This means you get all the key functions for managing product vulnerabilities within your environment: both in terms of supply chain management and checking your code for new vulnerabilities.
In particular, regardless of the configuration, the following pieces of functionality are fully accessible in the self-hosted version:
- Identifying components and generating SBOM
- Zero-day engine to detect new vulnerabilities
- Managing third-party dependencies and known vulnerabilities
- Delta reporting
- Cryptographic analysis
- File explorer for extracted artifacts
- Product and project groups, version tracking
- Team collaboration and role-based access
- PDF report generation to document evidence you need for compliance
We wanted to make sure that even air-gapped setups are supported by the self-hosted version, enabling use for high-level physical security environments, such as those common for audited security laboratories and R&D centers.
Please note that the availability of the following features depends on networking configuration: receiving vulnerability alerts, AI assistant for recommendations and shareable reports.
Ready to test it yourself?
Contact us for a demo and we can provide an easy-to-install evaluation version so you can test it on your own firmware images.